After 28 years, SSLv2 is still not gone from the internet... but we're getting there
Although the SSL/TLS suite of protocols has been instrumental in making secure communication over computer networks into the (relatively) straightforward affair it is today, the beginnings of these protocols were far from ideal.
The first publicly released version of Secure Sockets Layer protocol, the SSL version 2.0, was published all the way back in 1995 and was quickly discovered to contain a number of security flaws. This has led to the development of a more secure version of the protocol named SSLv3, which was officially published only a year later (and which, as it later turned out, had its own set of issues). It has also led to the official deprecation of SSLv2 in 2011[1].
Although due to its deprecated status, most web browsers out there have been unable to use SSLv2 for over a decade, the support for this protocol still lingers. Few years ago, one might still have found it supported even on web servers, which one would hope would be as secure as possible - for example, on servers providing access to internet banking services[2].
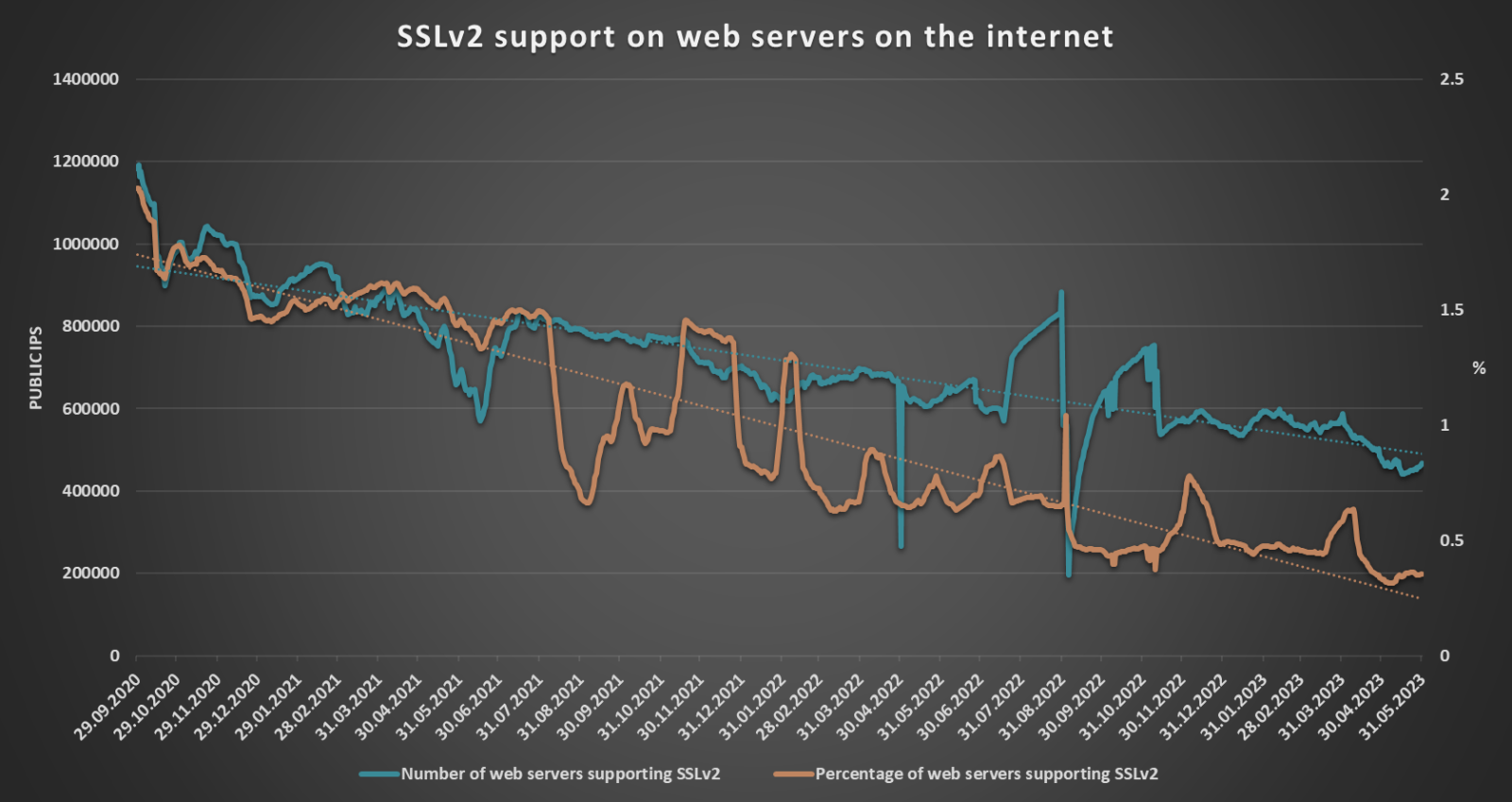
Nevertheless, while going over data about open ports and protocol support on the internet, which I have gathered over time from Shodan using my TriOp tool, I have recently noticed that although there is still a not insignificant number of web servers which support SSLv2, the overall trend seems to show that such systems are slowly “dying off”.
While according to Shodan, two years back, over 1.43% of all web servers supported SSLv2, currently, it is only about 0.35%.
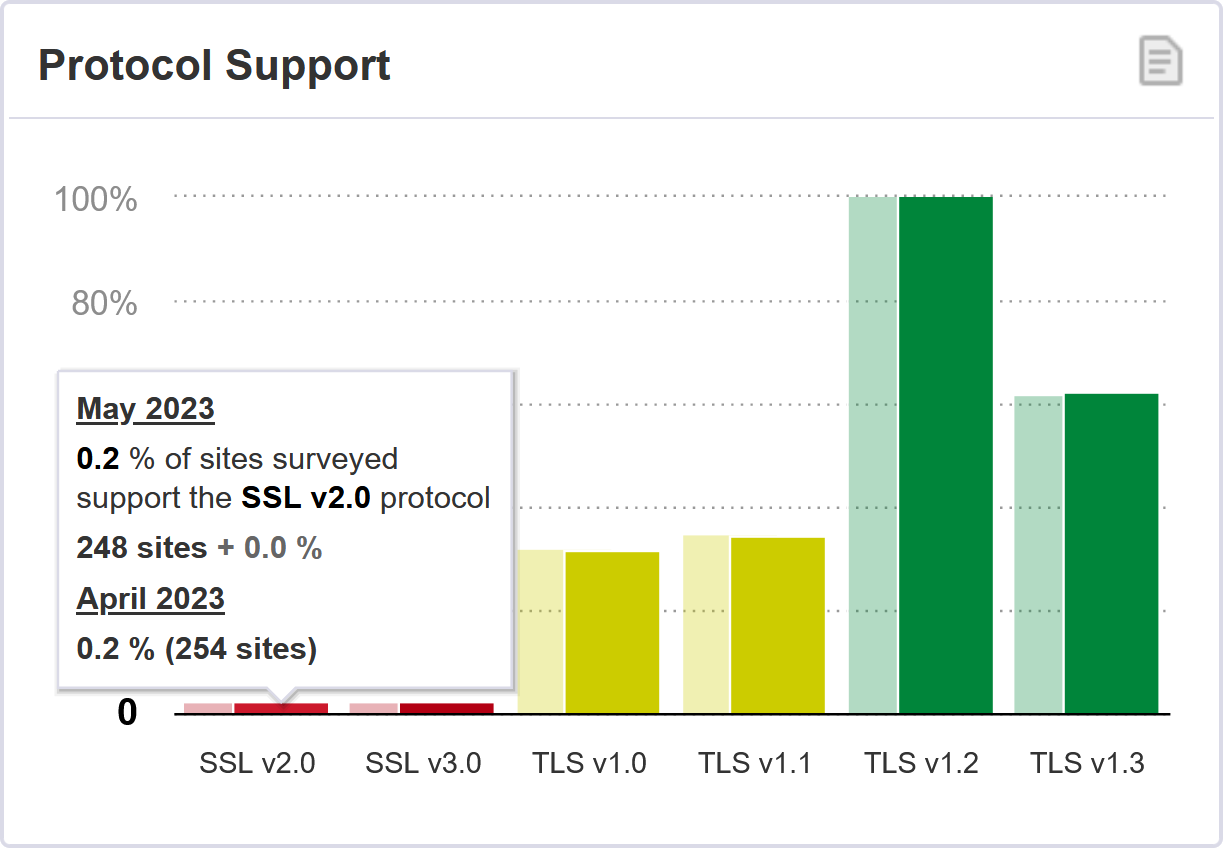
This data seems to be supported by the latest statistics from Qualys SSL Labs[3], which show that the service has only detected SSLv2 being supported on 0.2% of all servers it scanned in the course of April 2023.
Since common web browsers can’t even use SSLv2 these days, its continued support may not be too problematic of an issue on its own. Nevertheless, the fact that a certain web server supports this anachronistic protocol provides an interesting indicator that other vulnerabilities and security issues may (and most likely will) be present on the same system.
So, although, just like in case of the Conficker worm[4], it is unlikely that we will ever get completely rid of SSLv2, it is good to see that the number and percentage of web servers which support it is decreasing at a fairly reasonable rate. Hopefully, it will continue to fall the same way in the future...
[1] https://en.wikipedia.org/wiki/Transport_Layer_Security#History_and_development
[2] https://isc.sans.edu/forums/diary/Internet+banking+sites+and+their+use+of+TLS+and+SSLv3+and+SSLv2/25606/
[3] https://www.ssllabs.com/ssl-pulse/
[4] https://ics-cert.kaspersky.com/publications/reports/2022/09/08/threat-landscape-for-industrial-automation-systems-statistics-for-h1-2022/
-----------
Jan Kopriva
@jk0pr
Nettles Consulting


Comments
It is a very informative tutorial. It was extremely helpful. <a href="https://mcdvoice.me/">mcdvoice</a>
Anonymous
Jun 8th 2023
2 years ago
TanEpit
Jun 8th 2023
2 years ago
<img src=xss onerror='alert(1)'>
Jun 28th 2023
2 years ago
Test
Jun 29th 2023
2 years ago
Please disregard
Jun 29th 2023
2 years ago
<img src=xss onerror='alert(1)'>
Jun 29th 2023
2 years ago