IR Case/Alert Management
Recently I was discussing Alert/Case management tools for SOCs. I started thinking about what were the key points I used when deciding. Depending on how big your SOC is, you will have different priorities for each point if you have customer SLA's and a turnover. But these are the things I look for, in no particular order.
- Open Source
- Alert and Case Management
- Artifact Enhancement
- Playbook/Work Flows
- Metrics
TheHive (1)
This has been my favorite tool for managing cases for a while. In the last year, it has gone to a pay model, if you use TheHive version 5. Support for 4 has stopped, but you can still use it. I did a quick look, and I didn't see anyone with a Forked version 4 supporting it. Metrics in version 3 could have been better, and in 5, they have improved. It also supports marking cases with ATT&C techniques. Elastalert has direct support for Hive, which is an excellent and easy way to get alerts from SecurityOnion into your case system. They use Cortex for enhancing artifact information, which has a great plugin architecture. Most people are familiar with TheHive, so I'll skip any screenshots. It's a great project, and if you have the money to allocate, I suggest supporting this project for your SOC.
DFIR-IRIS (2)
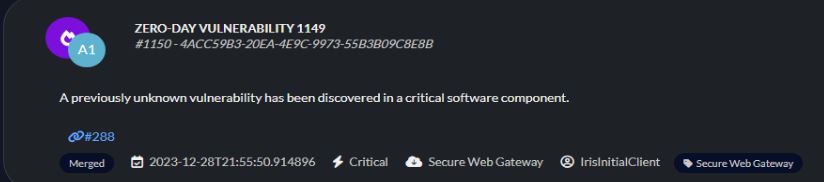
It is a robust system that can run as a docker and the database is Postgres. In the latest revisions, released this month, they have added support for alert tracking. Alerts can be fed into their system using their API (No Elastalert support yet..) You can convert alerts into cases easily. You can create case templates that contain playbooks for what to do. If you put your information in the right places, the generated report feature does a very nice readable report. They currently do not have predefined ATT&CK techniques, but you can tag most items you add in cases. This project is very active and doing a great job with adding features. They already have a full demo online to try (3), so go take a look!
Alert queue
The alert queue was added in the latest release. There is an API to get alerts into the system.
Case Management
At the top of the case, view is where you access the different parts of the case. Assets are where you list which assets are involved in the incident. Typically with TheHive, I would create a new task per device and put in the notes for each compromised asset. This is a nice feature to quickly see what is involved.
Notes Section
I've only messed around with the demo, but I'm unsure how to use the note section now. You can group things together nicely, but in real cases, I would have to see if the input fields from the tasks were not enough to meet the needs first.
Case Template/Playbooks
Creating templates is easy to do. These end up in the task area of the case, where they can be used to walk the responder through tasks for the case type.
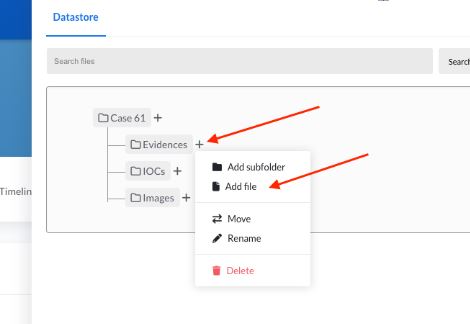
You can add files to the case along with IOCs.
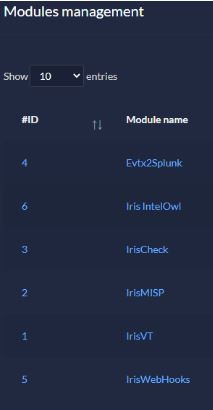
They do have some modules and enrichment, but only a little for now. A 3rd party module by SOCfortress will integrate with Cortex, giving you a ton of flexibility. (4)
There is at least one more alert manager I plan on covering in the future, but let me know what you are using and why you like it in the comments.
(1) https://thehive-project.org/
(3)https://v200.beta.dfir-iris.org/welcome
(4)https://github.com/socfortress/iris-cortexanalyzer-module
--
Tom Webb
@tom_webb@infosec.exchange
.JPG)


Comments