Phishing message to the ISC handlers email distro
Introduction
The ISC handlers email distro gets plenty of spam and phishing emails on a daily basis. Most of these are filtered so they never make it to the inbox; however, every once in a while one gets through.
Today's diary reviews an example of a phishing email from our inbox on Tuesday 2021-02-09.
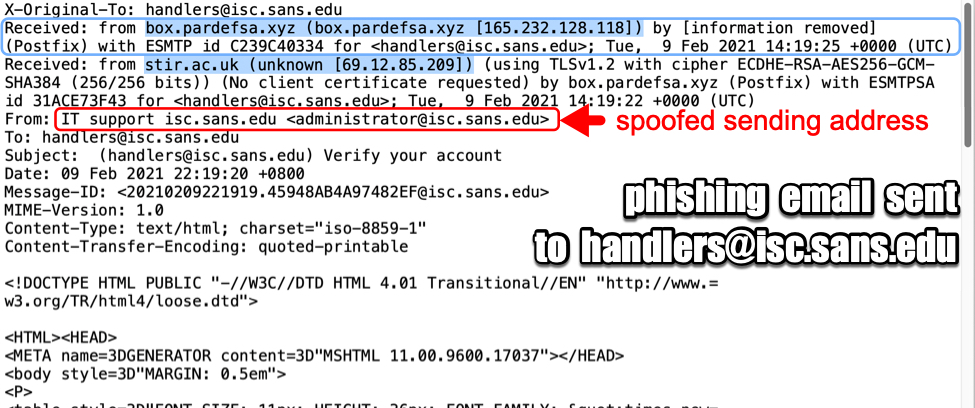
Shown above: Email headers from the phishing message.
The email
As shown in the previous image, the sending address had been spoofed to look like it came from administrator@sans.isc.edu. But the message actually came to our mail server from 165.232.128[.]118. That much we can confirm, because it was the most recent Received: from line before it hit our mail server. Anything else can be spoofed. Based on the only other Received: from line, this message might have originated from 69.12.85[.]209, but that line could have been added to confuse analysts.
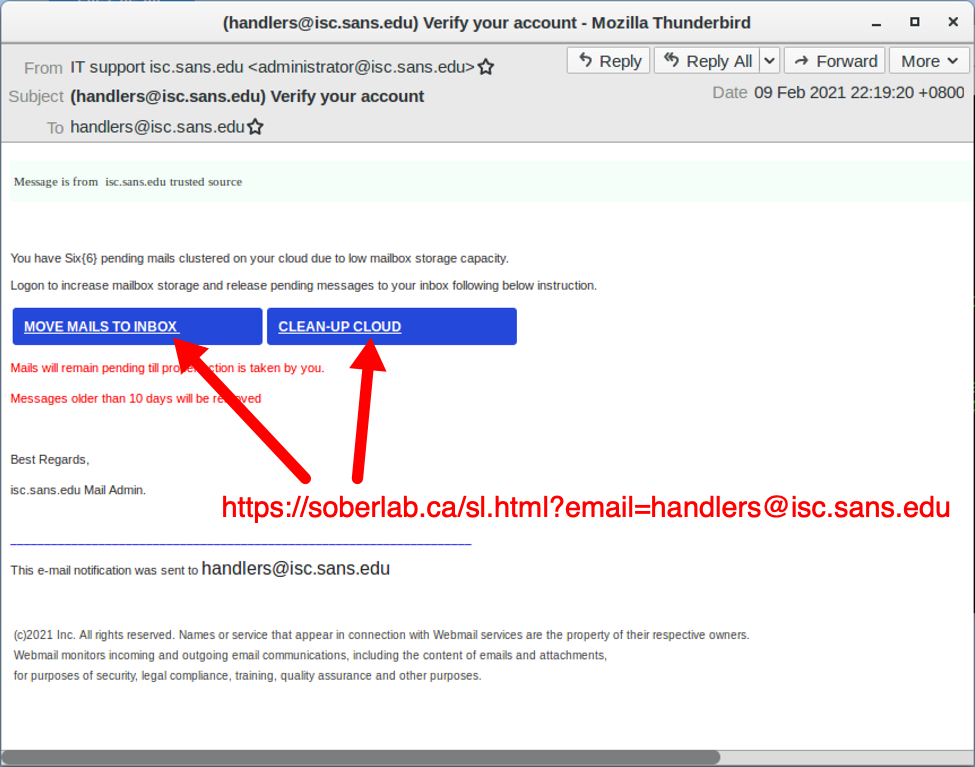
Shown above: Screenshot of the phishing messaged when viewed in the Thunderbird email client.
The phishing message has a URL to hxxps://soberlab[.]ca/sl.html?email=[phishing recipient's email address]. The domain oberlab[.]ca seems like it is hosting a legitimate website, and that legitimate website may have been compromised to host the phishing URL.
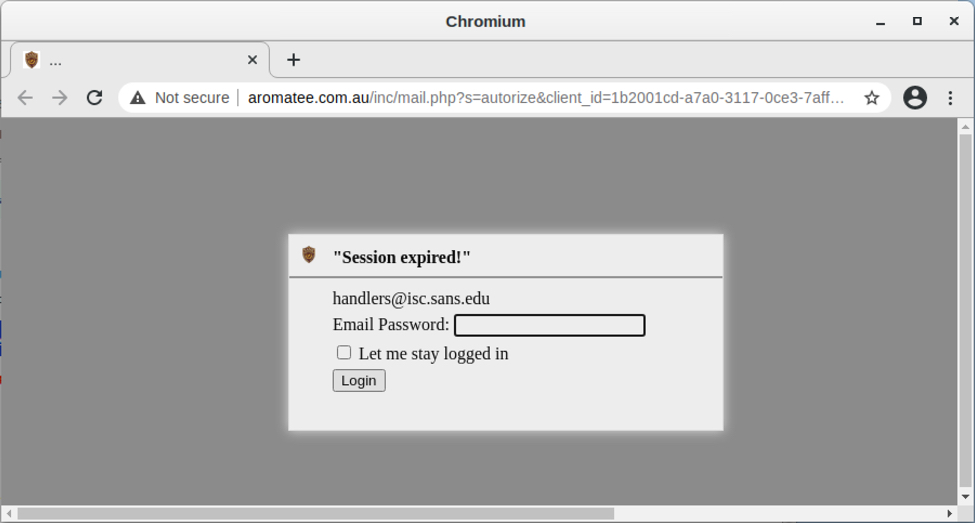
Shown above: Opening link from the phishing message in a web browser.
Phishing traffic
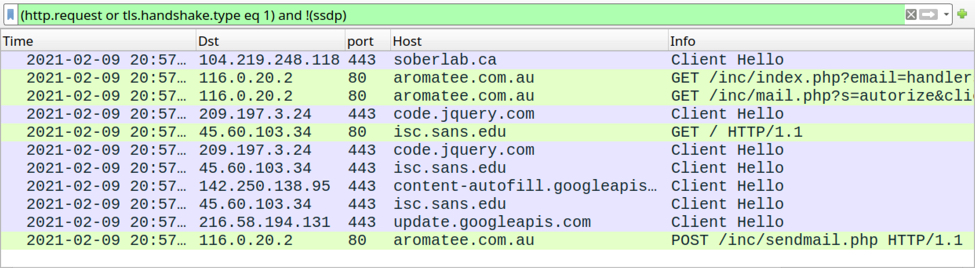
Shown above: Traffic from viewing the email link filtered in Wireshark.
The HTTPS link from the email redirects to a phishing page at hxxp://aromatee[.]com[.]au/inc/mail.php. Like the previous URL, this one looks like it's hosted on a legitimate domain using a server that's been compromised to host a phishing URL. I entered a fake password, and the data was sent over HTTP back to the server.
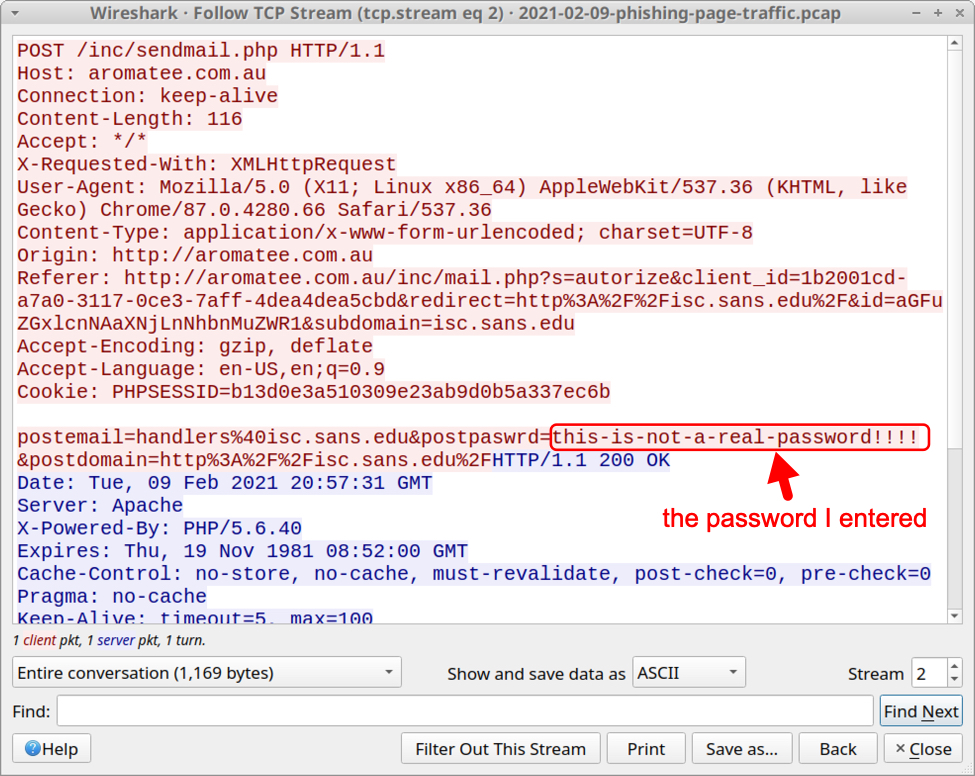
Shown above: HTTP POST request with the fake password I entered.
Final words
These types of emails are all too common, and they're remarkably cost-effective. While most of you wouldn't fall for it, people are fooled by similar messages. Therefore, phishing will remain a viable social engineering technique.
A sanitized version of the email shown in this diary, along with a pcap of traffic to the associated phishing page, can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments
Anonymous
Feb 10th 2021
4 years ago
For handlers of mail gateways: I've applied two additional checks on the From:-Header to stop such spoofed mails at our gateway.
Referring to Brads example,
1. check for "our" Domain: "*@isc.sans.edu"
2. check for active user names "IT .AND. support"
The second is to stop mails from "IT support isc.sans.edu <someone@otherdomain.tld>"
The user names list is created with a simple powershell script from active AD users and imported once a month on the gateway.
Btw. Please check your SPF entry, I guess there went something wrong:
$ dig +short isc.sans.edu txt
"v=spf1 include:isc.sans.edu._nspf.vali.email include:%{i}._ip.%{h}._ehlo.%{d}._spf.vali.email ~all"
Anonymous
Feb 13th 2021
4 years ago