Scanning with nmap?s NSE scripts
If someone asked me 7 or 8 years ago what I use nmap for, my answer would be: simple port scanning – it’s a port scanner, and that’s what it should be used for. Boy was I wrong.
As some of our readers certainly know, nmap includes the map Scripting Engine (NSE), which turns nmap into much more than a scanner – it allows creation of scripts which can perform all sort of actions. The scripts are written in the Lua programming language and nmap comes with many them – the very latest SVN version comes with 601 NSE script.
While scripts can be updated separately, nmap is actually one of the rare tools I download, compile and install manually. The main reason is because with nmap we really do want to have the very latest version always – development is very active and new features and bugs are constantly added. Besides that, the whole compilation process is typically trivial.
Since I do a lot of network penetration tests, where quite often I need to scan large networks (and report on findings), I found some NSE scripts unbelievably useful – this diary will contain some of the top NSE scripts I use during penetration tests – let us know if you have other candidates!
SSL/TLS testing
There is a bunch of scripts that test for various SSL/TLS configuration issues. These are a must – if you are doing a penetration test or you simply want to check if you have servers supporting SSLv3 in your enterprise, these scripts will do the job.
I actually already wrote about SSL/TLS testing – so if you want to read those diaries please go here and here.
- ssl-enum-ciphers – this script will enumerate supported protocols and cipher suites by the target web site. It will even give grades which are simulating what Qualys’ SSL Server Test web site does too. Just keep in mind that it does not support SSLv2 – for that we need another script ...
- sslv2 – you guessed it – this script will check if SSLv2 is supported by the target service.
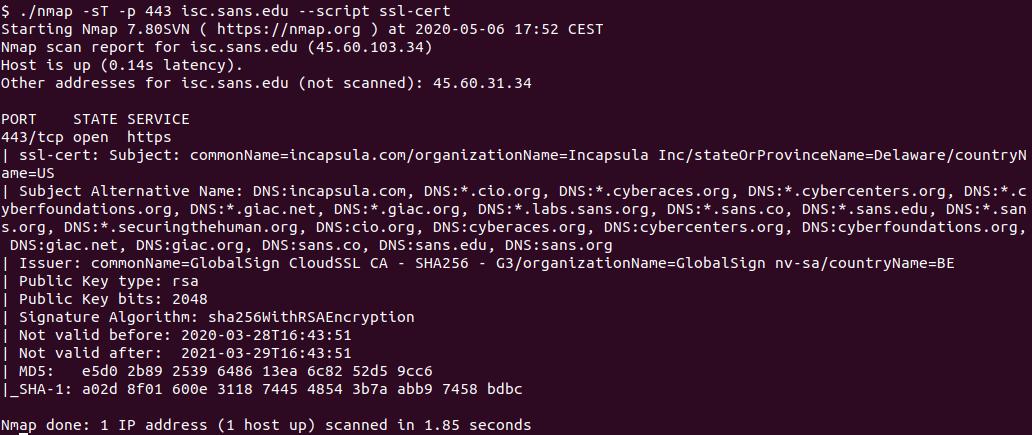
- ssl-cert – this script will retrieve information about the X.509 certificate used by the target service. It’s another handy script that allows you to retrieve certificates of all servers in your scope. Need to know which certificates expire soon? Just do a whole enterprise scan on TCP port 443 with ssl-cert and parse the output. Can’t get easier than that.
- ssl-dh-params – this script checks if the target service is using weak Diffie-Hellman groups and parameters.
Here is one example of me checking the certificate on the isc.sans.edu web site:
Hmm, do you see something interesting here? Let us know.
SMB testing
Issues in configuration of SMB services can be devastating – anyone who even remotely heard about Responder, Impacket and ntlmrelayx knows what I’m talking about. That’s why I think it is mandatory to check SMB configuration in every penetration test (and in your enterprises). Nmap comes to the rescue here, again with a number of great scripts:
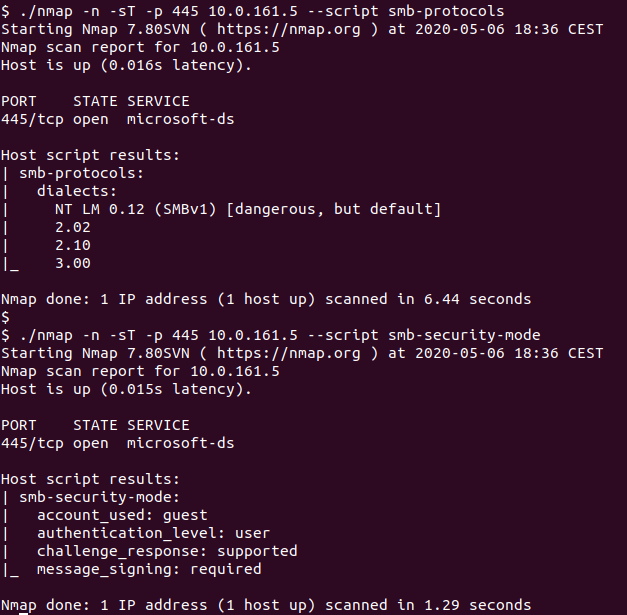
- smb-protocols – this script will check which SMB protocols are supported by the target server. If you see SMBv1 supported – that’s really bad.
- smb-security-mode – the script will check for various information about the SMB security level. Besides checking for authentication, probably the most important configuration parameter is message signing – this shows if it is required by the target server or not. Whenever you see message signing not being required, this should be reported as a vulnerability (misconfiguration) since it will allow all those scary tools listed above (Responder etc) to be used by an attacker.
- smb2-security-mode – the script check whether message signing is enabled, but for SMB2/3 protocols. Do not forget to use it if your target server supports only SMBv2.
I am running these scripts here against a server – we can see that it’s misconfigured because it supports SMBv1 (which should really be disabled everywhere), but at least it has message signing set to required:
HTTP scripts
There is a large number of HTTP scripts – 135 of them currently so I suggest that you get familiar with what is available so you can use them when needed. That being said, there are few cool scripts that I tend to run almost every time, just because they are so convenient:
- http-apache-server-status – the Apache /server-status web page can often leak a lot of very sensitive information. I actually had cases where I completely compromised a target environment just based on leaked information I saw in the /server-status web page. That’s why I like to automatically check every single server for this web page, and this script will do that easily.
- http-methods – the script identifies all supported methods. Handy in first phases of a penetration test.
- http-shellshock – while Shellshock is a bit old now, internally it can still be found quite often. This script allows for an easy check if the target server is vulnerable to Shellshock.
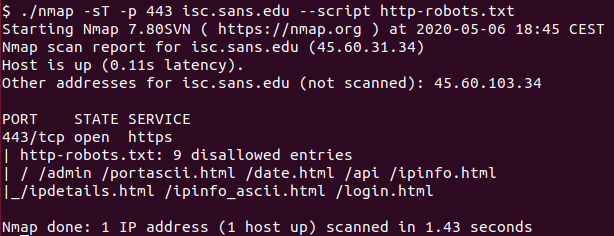
- http-robots.txt – another very handy script that will automatically retrieve contents of the /robots.txt file and display them.
Again, this is very useful in cases when you need to check a large number of target servers – simply run the script against them and analyze the results offline.
Here I am running the http-robots.txt NSE script against isc.sans.edu:
Huh, look at those results, do you see anything suspicious there?
I hope you liked this selection of nmap NSE scripts – there are many, many other useful scripts. Let us know which ones are your favorites!
Ah yes – we cover nmap (of course) in the SEC 542 (Web application penetration testing and ethical hacking) course as well, in context of web application penetration tests, of course. There's even time to sign up for the course next week - I'll be teaching the new (updated) version of the course for the first time live.
| Web App Penetration Testing and Ethical Hacking | London | Mar 2nd - Mar 7th 2026 |


Comments