Hazelcast IMDG Discover Scan
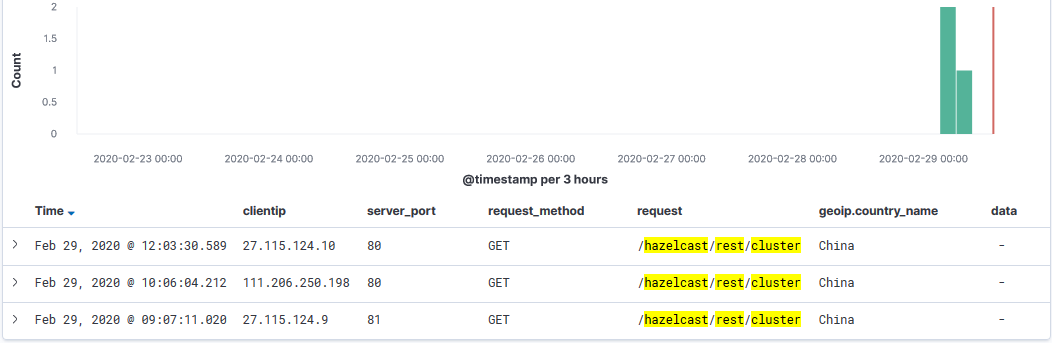
Today my honeypot has been capturing scans for the Hazelcast REST API. I checked my logs for the past 2 years and these only started today. The last vulnerability published for Hazelcast was CVE-2018-10654 and related to "There is a Hazelcast Library Java Deserialization Vulnerability in Citrix XenMobile Server 10.8 before RP2 and 10.7 before RP3."[3]
There was some discussion regarding this issue at the end of Sep 2019 that got fixed at the end of Nov 2019 [5] where /hazelcast/rest/cluster HTTP endpoint returns HTTP 500 status. If you are seeing similar discovery scans and when they started, we would like to hear from you.
[1] https://docs.hazelcast.org/docs/management-center/3.9.2/manual/html/Clustered_REST_via_Management_Center.html
[2] https://vulmon.com/searchpage?q=hazelcast
[3] https://vulmon.com/vulnerabilitydetails?qid=CVE-2018-10654&scoretype=cvssv2
[4] https://github.com/hazelcast/hazelcast/issues/15635
[5] https://github.com/hazelcast/hazelcast/pull/16150
[6] https://isc.sans.edu/forums/diary/Citrix+ADC+Exploits+Overview+of+Observed+Payloads/25704
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu


Comments
111.206.52.81 - - [13/Feb/2020:19:39:41 +0000] "GET /hazelcast/rest/cluster HTTP/1.0" 302 229 "-" "-"
27.115.124.74 - - [15/Feb/2020:17:58:20 +0000] "GET /hazelcast/rest/cluster HTTP/1.0" 302 239 "-" "-"
These requests were directed to port 80 on my server.
Anonymous
Feb 29th 2020
5 years ago
Anonymous
Mar 1st 2020
5 years ago
/var/log/apache2/access.log:111.206.250.230 - - - [22/Feb/2020:19:23:55 -0300] "GET /hazelcast/rest/cluster HTTP/1.0" 404 360 "-" "-"
Anonymous
Mar 2nd 2020
5 years ago