3D Printers in The Wild, What Can Go Wrong?
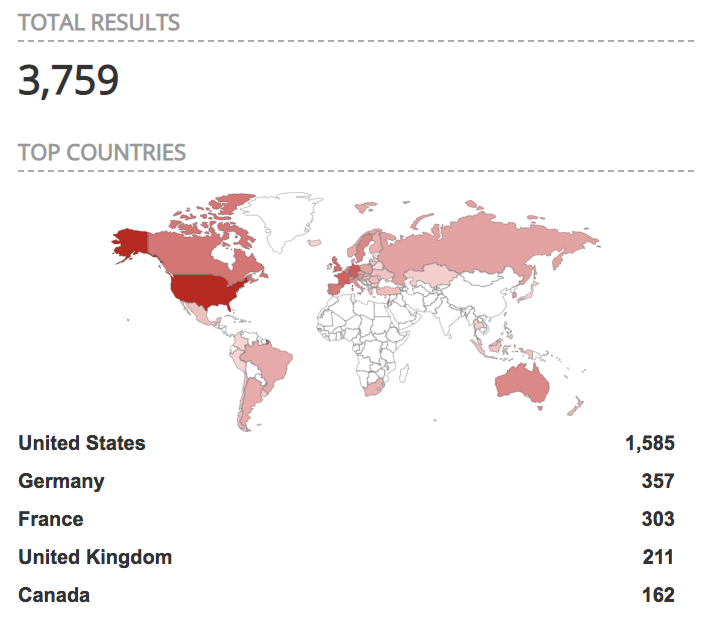
Richard wrote a quick diary yesterday about an interesting information that we received from one of our readers. It's about a huge amount of OctoPrint interfaces that are publicly facing the Internet. Octoprint[1] is a web interface for 3D printers that allows to control and monitor all features of the printer. They are thousands of Octoprint instances accessible without any authentication reported by Shodan:
Here is an example of a publicly open interface connected to an online printer (status is "operational"):
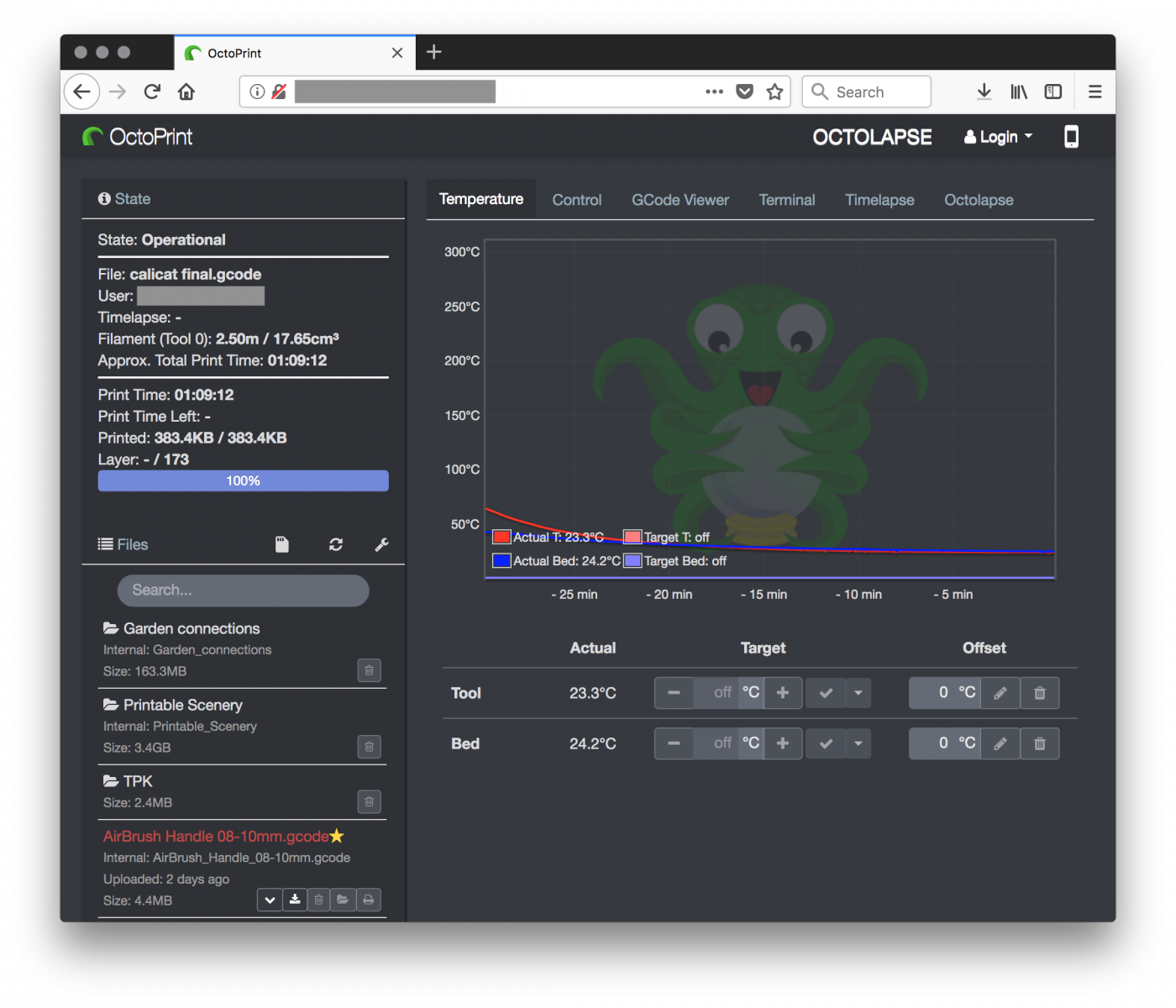
So, what can go wrong with this kind of interface? It’s just another unauthenticated access to an online device. Sure but the printer owners could face very bad situations.
The interface allows downloading the 3D objects loaded in the printer. Those objects are in G-code format[2]. To make it simple, G-code is a language in which people tell computerized machine tools how to make something. G-code files are simple text files and are not encrypted:
$ cat sample.gcode G90 M82 M106 S0 M104 S210 T0 M109 S210 T0 G28 ; home all axes G92 E0 G1 E-3.0000 F1800 G1 Z0.135 F1002 ; process CR10S4 ; layer 1, Z = 0.135 T0 ; tool H0.150 W0.400 ; skirt G1 X190.485 Y170.099 F4800 G1 E0.0000 F540 G92 E0 G1 X190.631 Y169.944 E0.0050 F1080 G1 X190.641 Y169.933 E0.0054 G1 X191.500 Y169.102 E0.0337 G1 X191.511 Y169.092 E0.0341 G1 X191.671 Y168.952 E0.0391 G1 X191.682 Y168.942 E0.0395 G1 X192.634 Y168.188 E0.0682 G1 X192.646 Y168.179 E0.0686 G1 X192.821 Y168.054 E0.0737 G1 X192.833 Y168.046 E0.0740 G1 X193.848 Y167.394 E0.1026 ...
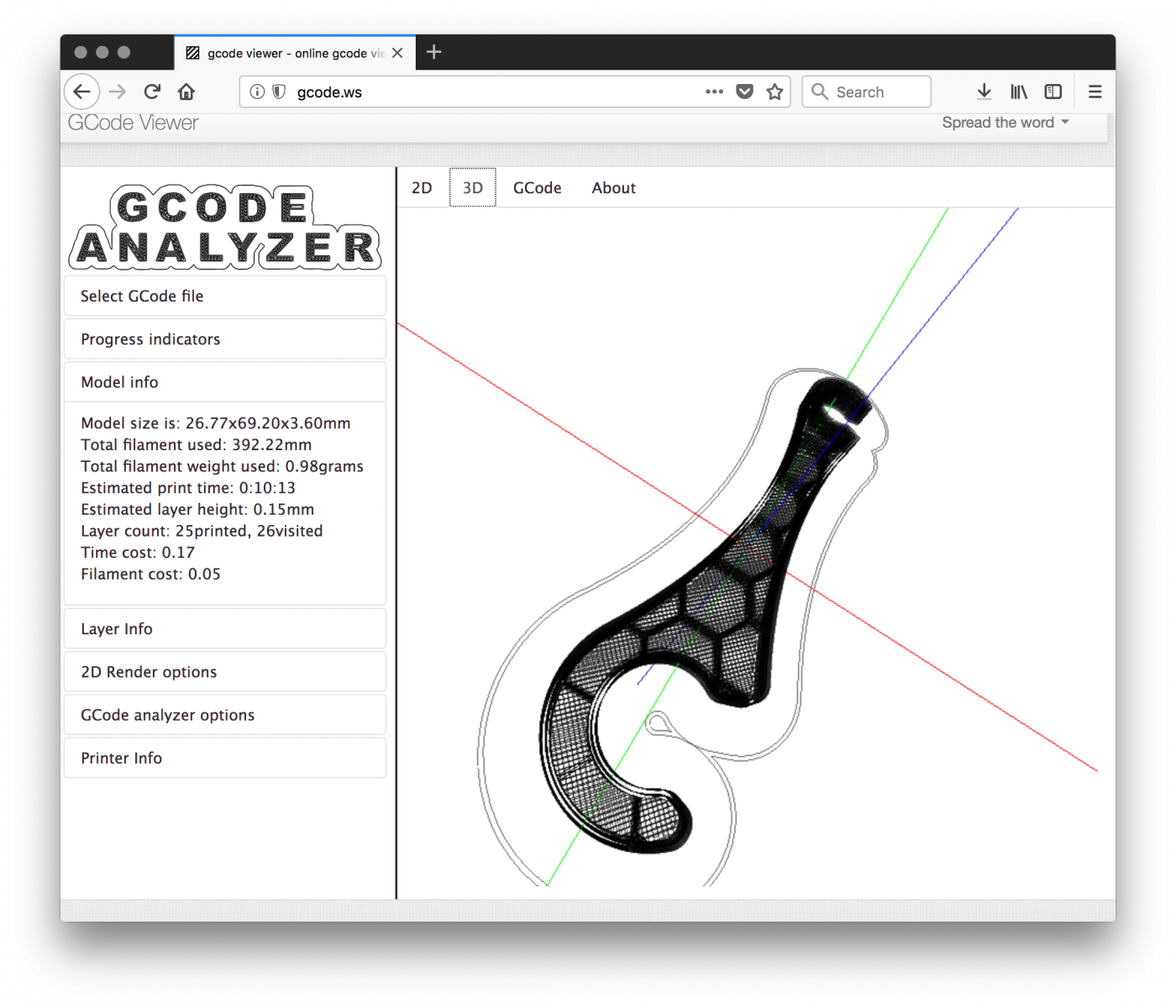
We are facing here the first issue: G-code files can be downloaded and lead to potentially trade secret data leak. Indeed, many companies R&D departments are using 3D printers to develop and test some pieces of their future product. Here is an example of G-code file rendered via an online tool:
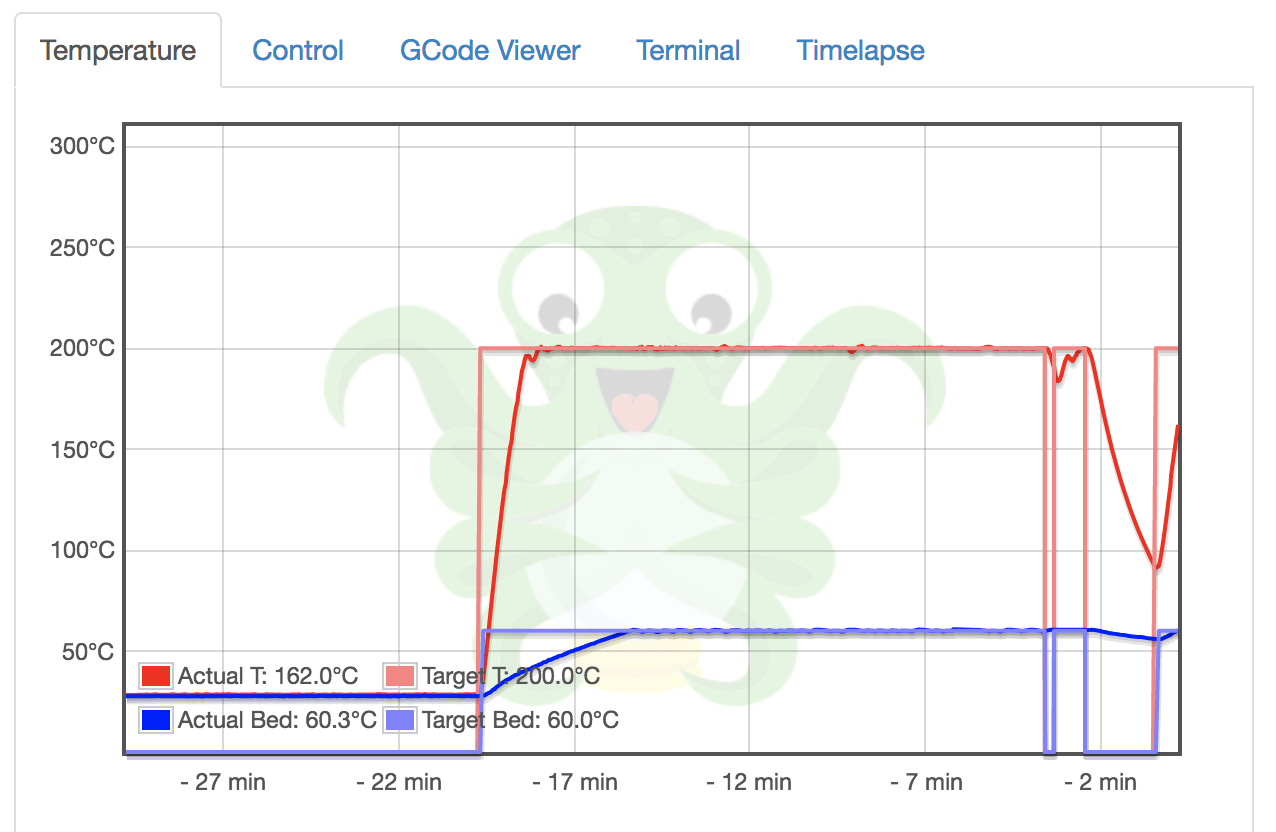
If the authentication is completely disabled, it is possible to upload G-code files and… print them! What if an anonymous person sends a malicious G-code file to the printer and instructs to print it while nobody is around? There were bad stories of low-cost 3D printers which simply burned![3]. Here is one found busy to print an object. Did you see the temperature?
Worse, what if the attacker downloads a G-code file, alters it and re-upload it. Be changing the G-code instructions, you will instruct the device to print the object but the altered one won’t have the same physical capabilities and could be a potential danger once used. Think about 3D-printer guns[4] but also 3D-printed objects used in drones. Drone owners are big fans of self-printed hardware.
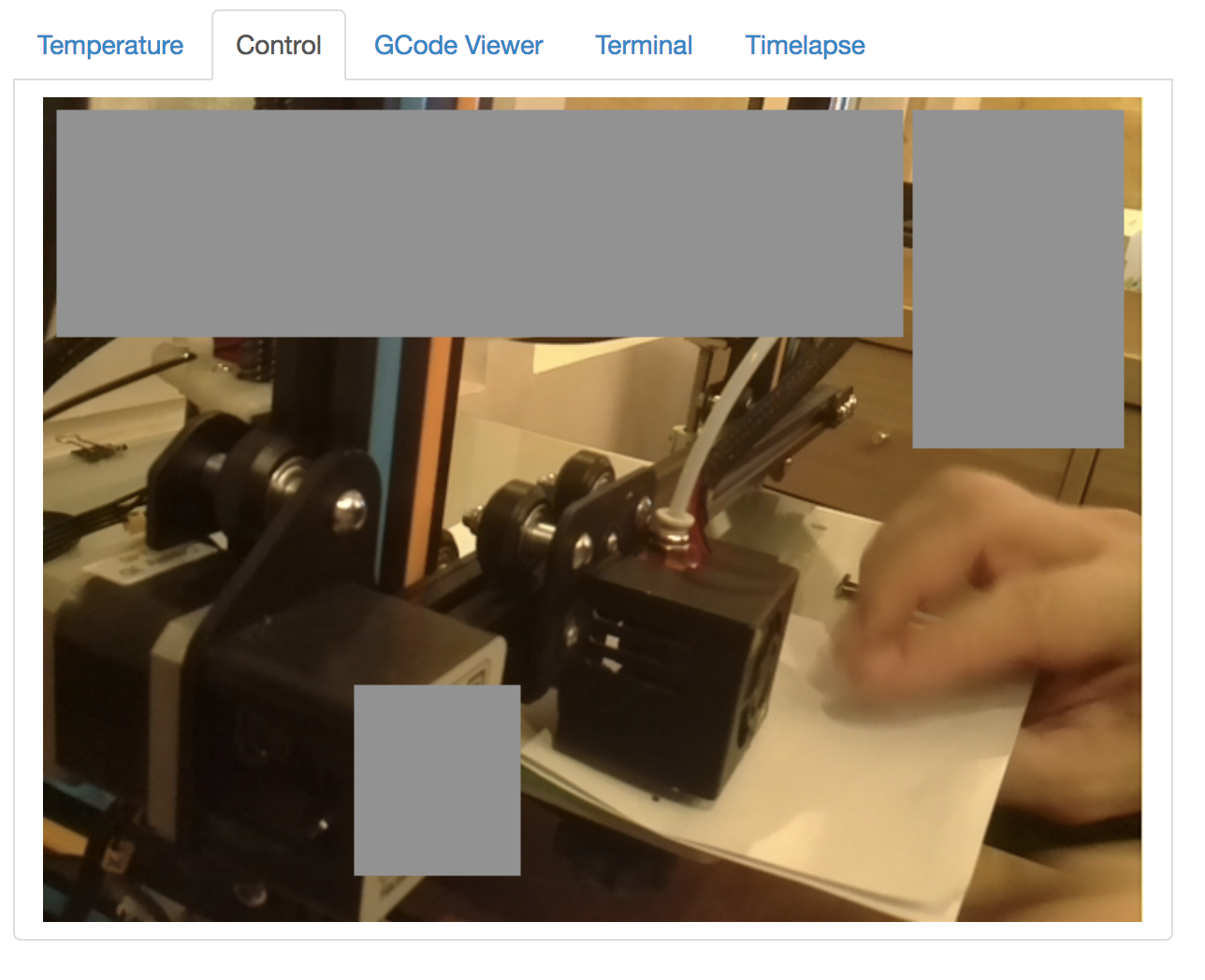
Finally, OctoPrint offers a monitoring feature based on an embedded webcam which can affect the remote user privacy. On this screenshot, the operator was preparing his printer but we can also see some details behind the printer.
How to protect your OctoPrint instance? The documentation says about access control[5]:
"When Access Control is enabled, anonymous users (not logged in) will only see the read-only parts of the UI which are the following” (followed by a long list of features). Most critical is accessing to the webcam and downloading G-code files. As suggests the documentation: “If you plan to have your OctoPrint instance accessible over the internet, always enable Access Control".
Thank you again to Kalaireas for sharing this.
[1] https://octoprint.org/
[2] https://en.wikipedia.org/wiki/G-code
[3] https://hackaday.com/2018/03/18/3d-printer-halts-and-catches-fire-analysis-finds-a-surprising-culprit/
[4] https://en.wikipedia.org/wiki/3D_printed_firearms
[5] http://docs.octoprint.org/en/master/features/accesscontrol.html
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments
Anonymous
Aug 29th 2018
7 years ago
https://isotropic.org/papers/chicken.pdf
https://isotropic.org/papers/chicken.ppt
Anonymous
Aug 29th 2018
7 years ago