Analysis of a Distributed Denial of Service (DDoS)
I was sent this past week a file containing 10,711 unique IP addresses used in a DDoS. The entire DDoS occurred over a period of about 48 hours. This traffic is from the second day where all requests at the firewall were logged (1.5M reqs) and the traffic was dropped. Using the logs I was provided, I generated 3 graphs: a list of the TCP flags and the Top 10 ASN and countries associated with the source IPs.
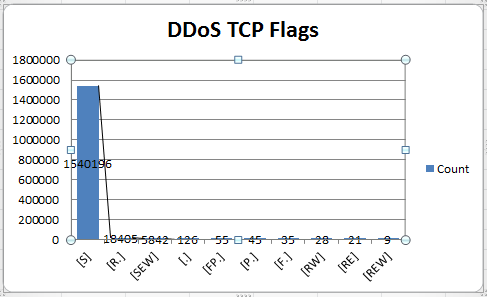
The time frame of this activity occurred between 02:28 - 17:37 GMT. The first graph represents the TCP flags captured in this traffic. The data contains over 1.5M SYN packets followed by just over eighteen thousand TCP RST packets, etc. This is not a huge DDoS since it occurred over a period of 15 hours, it amounts to about 104,300 packets per hour.
TCP Flags
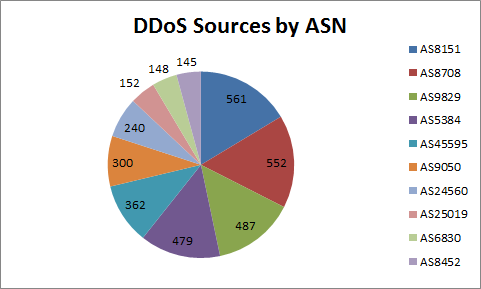
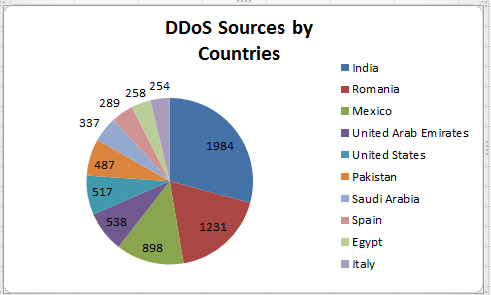
I used Maxmind geoiplookup[1] tool to graph only the top 10 Autonomous System Number (ASN) and countries assigned to each inbound IPs. Since it is a DDoS, I have to assume the traffic is likely spoofed and likely controlled by a botnet.
Maxmind Analysis of IPs by ASN - Top 10
Maxmind Analysis of IPs by Countries - Top 10
Just for fun, I also sorted the TCP options. Below is the Top 20 list. What is also interesting in this output is the most common windows of 8192 which is usually associated with the Windows OS. The maximum segment size (MSS) is anywhere between 1360 to 1460 use to indicate the maximum payload a packet can carry which might be associated with smaller MTU. For example, an MTU of 1452 is often associated with PPPoE and DSL routers.[4] The 16,628 packets with a "win 0, length 0" are all the Reset packets captured in the traffic.
Count TCP Options
131661 win 8192, options [mss 1460,nop,wscale 2,nop,nop,sackOK], length 0
115274 win 8192, options [mss 1460,nop,nop,sackOK], length 0
69531 win 8192, options [mss 1452,nop,nop,sackOK], length 0
66714 win 65535, options [mss 1460,nop,nop,sackOK], length 0
66670 win 8192, options [mss 1452,nop,wscale 2,nop,nop,sackOK], length 0
61611 win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
43965 win 8192, options [mss 1452,nop,wscale 8,nop,nop,sackOK], length 0
35975 win 65535, options [mss 1452,nop,nop,sackOK], length 0
31301 win 8192, options [mss 1412,nop,wscale 2,nop,nop,sackOK], length 0
25286 win 8192, options [mss 1412,nop,nop,sackOK], length 0
19160 win 8192, options [mss 1400,nop,nop,sackOK], length 0
18457 win 8192, options [mss 1440,nop,nop,sackOK], length 0
18290 win 8192, options [mss 1440,nop,wscale 2,nop,nop,sackOK], length 0
17903 win 8192, options [mss 1440,nop,wscale 8,nop,nop,sackOK], length 0
17418 win 8192, options [mss 1360,nop,wscale 2,nop,nop,sackOK], length 0
16628 win 0, length 0
15921 win 8192, options [mss 1400,nop,wscale 8,nop,nop,sackOK], length 0
15058 win 8192, options [mss 1360,nop,nop,sackOK], length 0
14720 win 8192, options [mss 1400,nop,wscale 2,nop,nop,sackOK], length 0
14651 win 8192, options [mss 1380,nop,wscale 2,nop,nop,sackOK], length 0
[1] https://github.com/maxmind/geoip-api-c
[2] http://kbeezie.com/geoiplookup-command-line/
[3] https://isc.sans.edu/forums/diary/DDOS+is+down+but+still+a+concern+for+ISPs/20701
[4] http://www.cisco.com/c/en/us/support/docs/long-reach-ethernet-lre-digital-subscriber-line-xdsl/asymmetric-digital-subscriber-line-adsl/12918-router-mtu.html
[5] http://dev.maxmind.com/geoip/legacy/geolite/
[6] https://en.wikipedia.org/wiki/Autonomous_system_%28Internet%29
-----------
Guy Bruneau IPSS Inc.
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu


Comments
Great analysis- it is so interesting to see the story told by the data and is so much more valuable than "we just had a DDoS".
Russell
Anonymous
May 29th 2016
9 years ago
Anonymous
May 29th 2016
9 years ago
couldnt you get more out of the data like rps/time, volume/time etc?
cheers, mex
Anonymous
May 30th 2016
9 years ago
First great analysis! always interesting to learn more about the subject of DDoS.
But except for the need pursue knowledge, do you think such data can help organizations deal with DDoS attacks? If so how?
Anonymous
May 30th 2016
9 years ago
Anonymous
May 30th 2016
9 years ago
Anonymous
May 30th 2016
9 years ago