Angler EK campaign targeting several .co domains deploying teslacrypt 3.0 malware
by Manuel Humberto Santander Pelaez (Version: 1)
We have seen in the last two weeks a massive amount of websites hosting a variant of angler exploit kit that infects computers downloading and activating a variant of teslacrypt 3.0, crypting files with mp3 extension and being able to exploit the CWE-592 vulnerability for Mcafee products. The computer where the analysis took place has Mcafee Host IPS installed without the last patches and updates.
When the teslacrypt exe is executed, it tries to replicate several times as shown in the following figure:
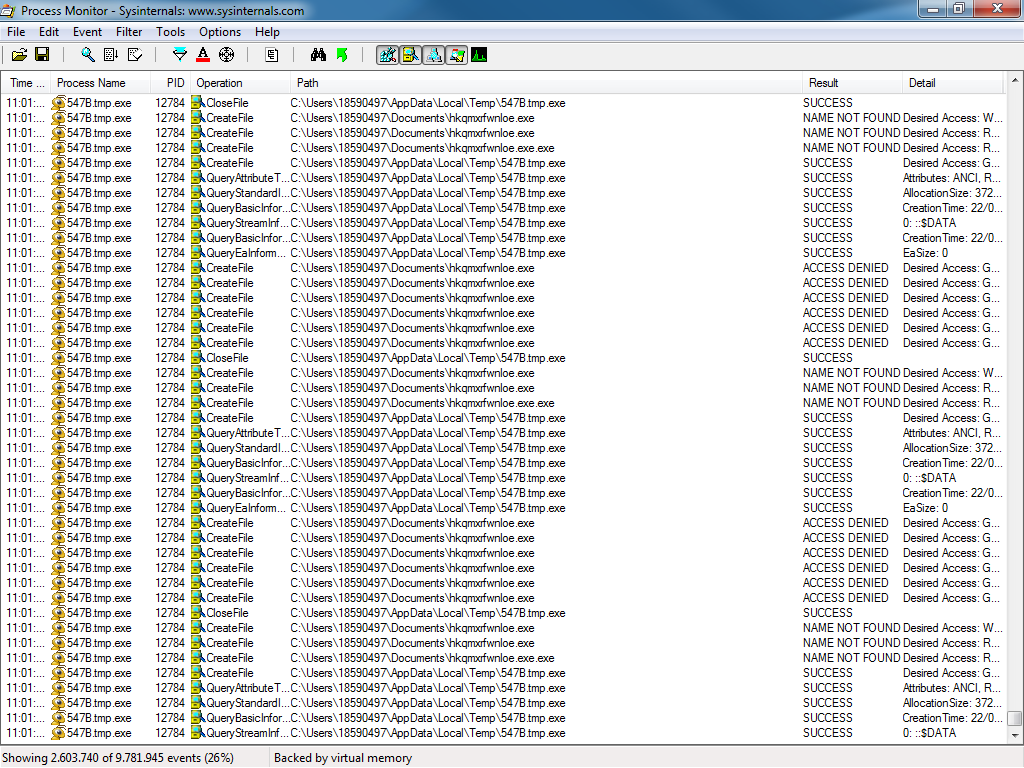
The Mcafee Host IPS works by blocking all the file creation attempts:
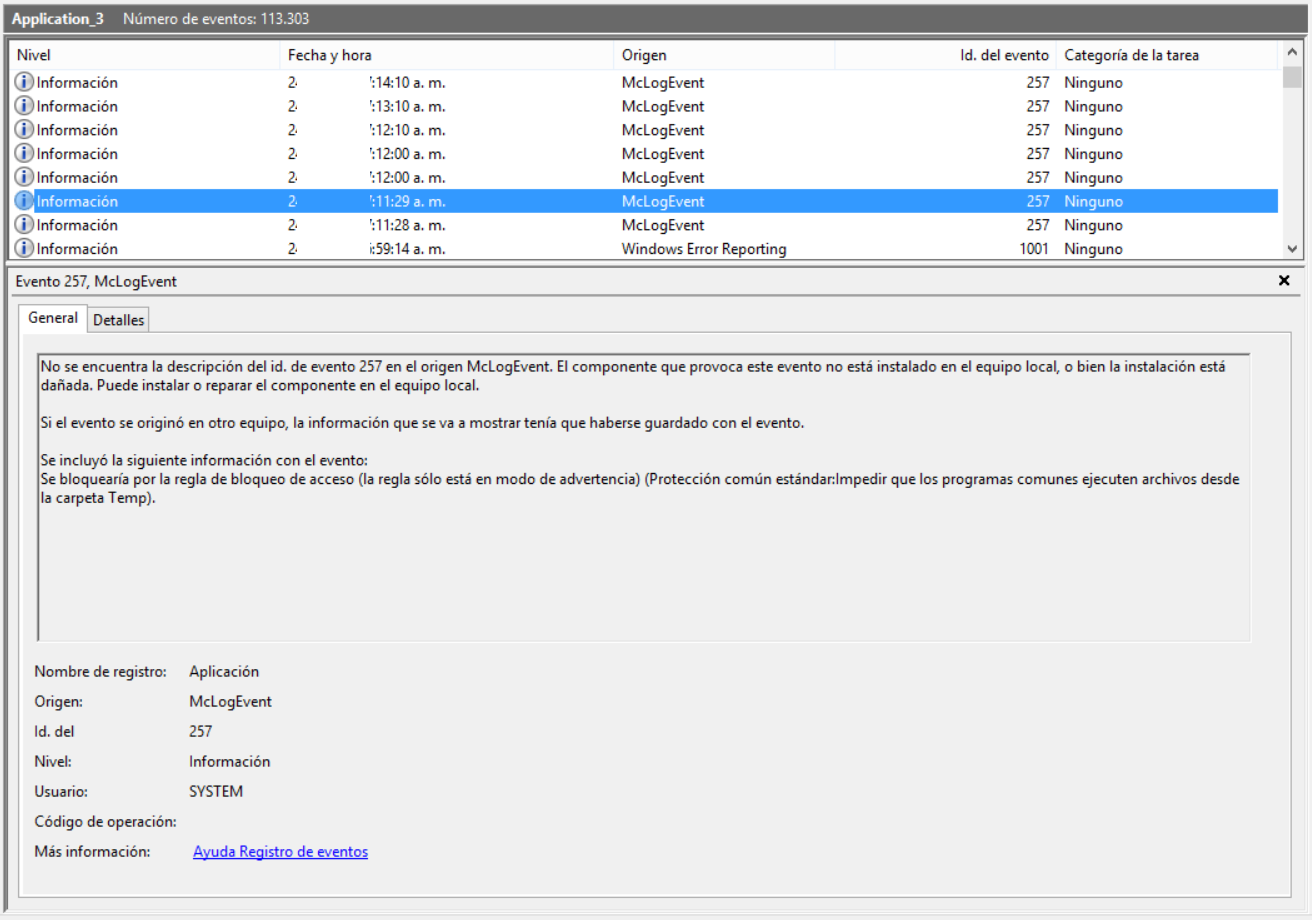
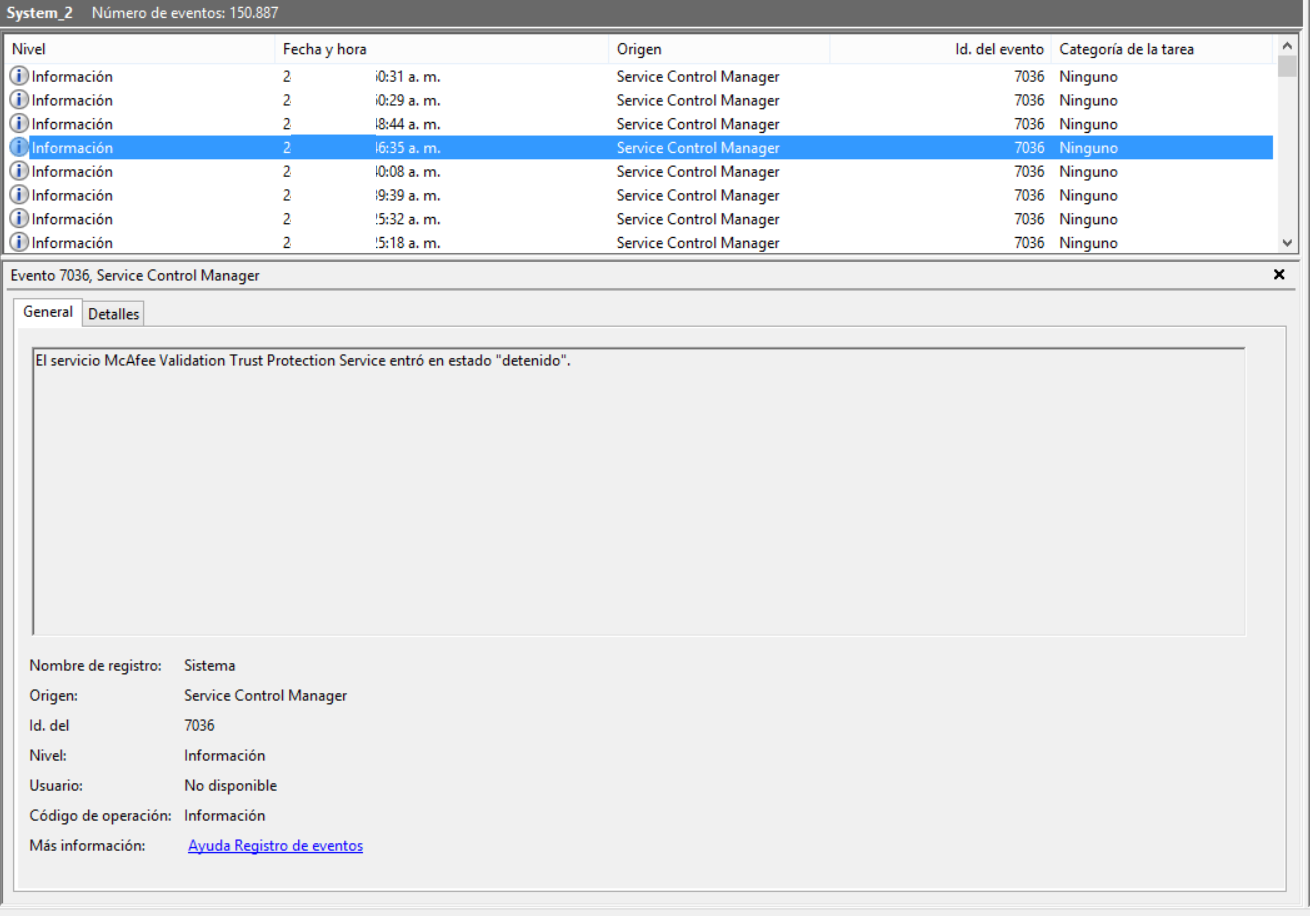
The Mcafee Validation Trust Protection service stops. This is where the malware takes advantage of CWE-592:
12-char malware exe file is successfully wrote in the filesystem:
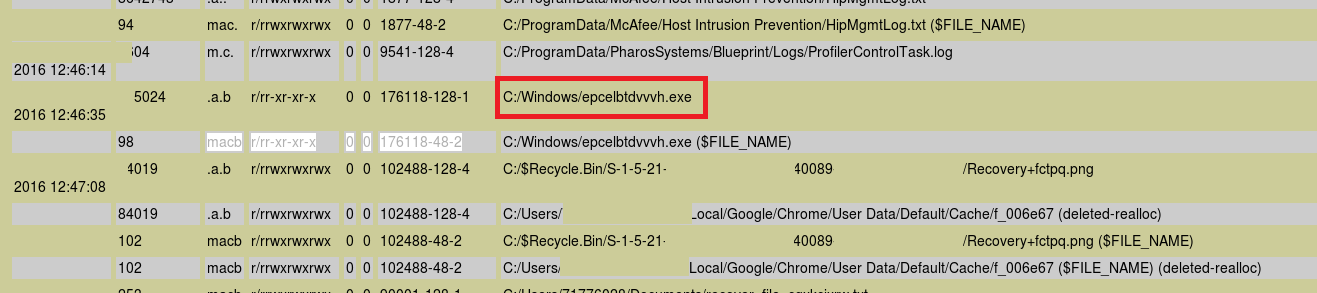
Teslacrypt inits the crypto process to all files in computer:
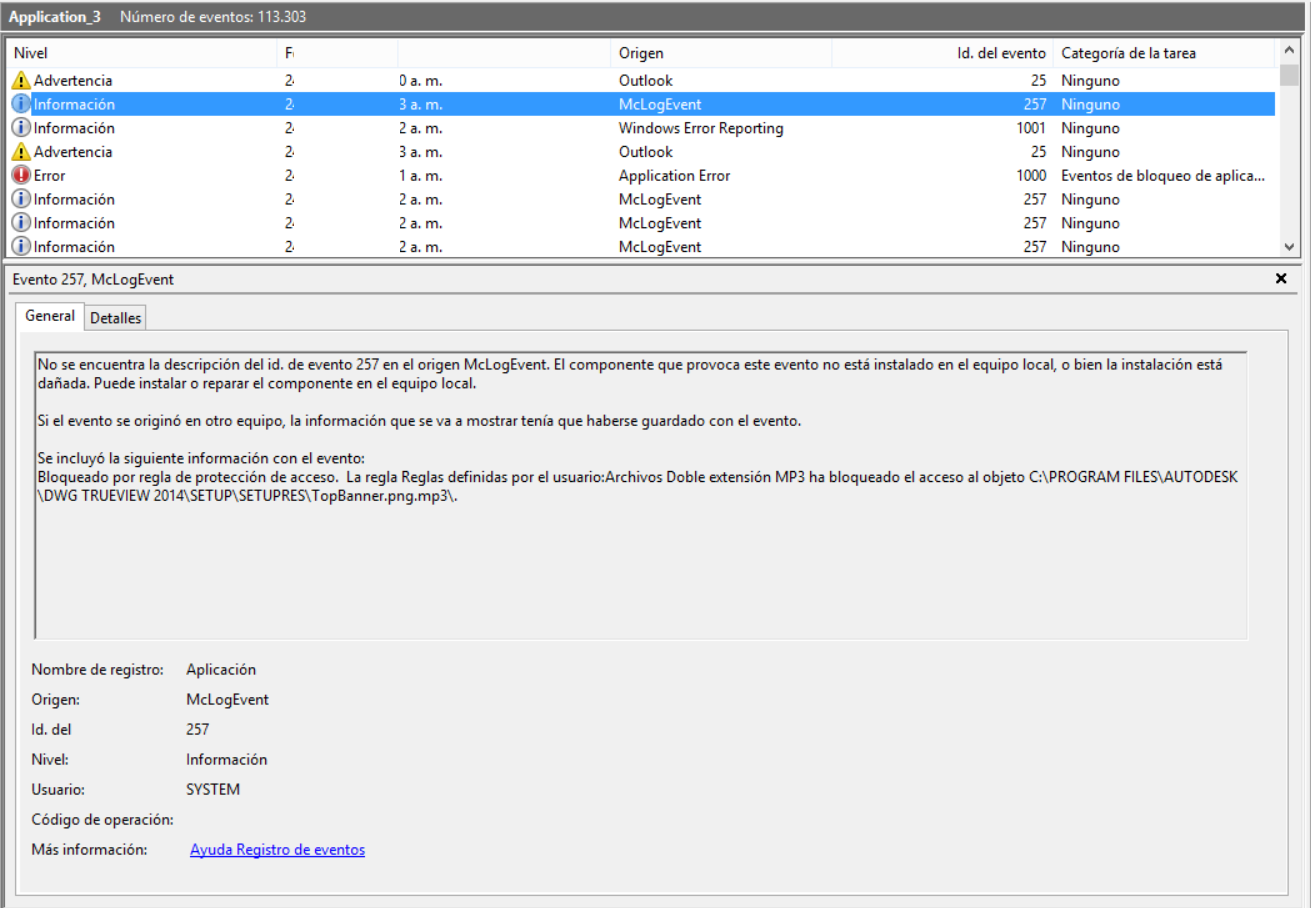
This teslacrypt malware is able to detect if somebody is trying to kill it, tamper it, perform investigation or any similar task, performing secure deletion of all possible evidence in the hard drive.
Along with this tendency, we have seen as well lots of attempts of LOCKY.A ransomware trying to infect computers using malicious emails directed to .co domains.
Please keep in mind some countermeasures to avoid infection by Angler EK or ransomware:
- Implements strong antispam, antimalware and antiphishing procedures.
- Keep operating systems patched against known vulnerabilities.
- Install patches from vendors as soon as they are distributed, after performing a full test procedure for each patch.
- Train your users to be careful when opening attachments.
- Configure antimalware software to automatically scan all email and instant-message attachments.
- Configure email programs to do not automatically open attachments or automatically render graphics.
- Ensure that the preview pane of your e-mail reader is turned off.
- Use a browser plug-in like noscript to block the execution of scripts and iframes.
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter: @manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org


Comments
identified as Telsacrypt by some AV per
https://www.virustotal.com/en/file/b4d0f4a0482a40db4b4077d9ecfbe2fef6548e836a6a854a0a0f88069b1a3695/analysis/
It seemed to come from a zero-day JS-in-zip downloader sent Feb 24, from a domain hpalsowantsff.com created the day before, and was itself a zero-day variant when it was downloaded on Feb 25th.
Andrew Daviel
Anonymous
Mar 5th 2016
9 years ago