Dropbox Phishing via Compromised Wordpress Site
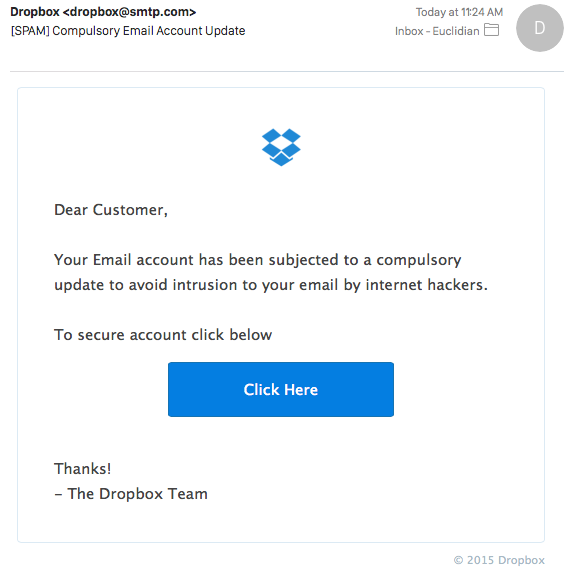
I got a couple of emails today notifying me of a "Compulsory Email Account Update" for my Dropbox account. The e-mails do overall mimic the Dropbox look and feel, and use dropbox@smtp.com as a "From" address. Nothing terrible new, but a nice case study on how defense in depth helps against these types of emails.
First of all, the email is sent from "dropbox@smtp.com". The domain smtp.com is owned by an e-mail marketing service, and it publishes SPF records. The IP address the e-mail was sent from (74.116.248.222) is not in SMTP.com's approved list:
"spf2.0/pra,mfrom include:_spf2.smtp.com ~all"
"v=spf1 ip4:192.40.160.0/19 ip4:74.91.80.0/20 include:salesforce.com ?all"
But note the "?all" part, which specifies that for all IPs not listed, the result is "neutral" which usually means the e-mail is accepted. So in the end, it kind of invalidates the SPF record, but a spam filter could still include the fact in its score.
Moving on to our spam filter. Our not well tuned spamassassin implementation gave it a score of 33! URLs listed in the email are blocklisted for example. The e-mail agent (Outlook) does not match the layout of the MIME message.
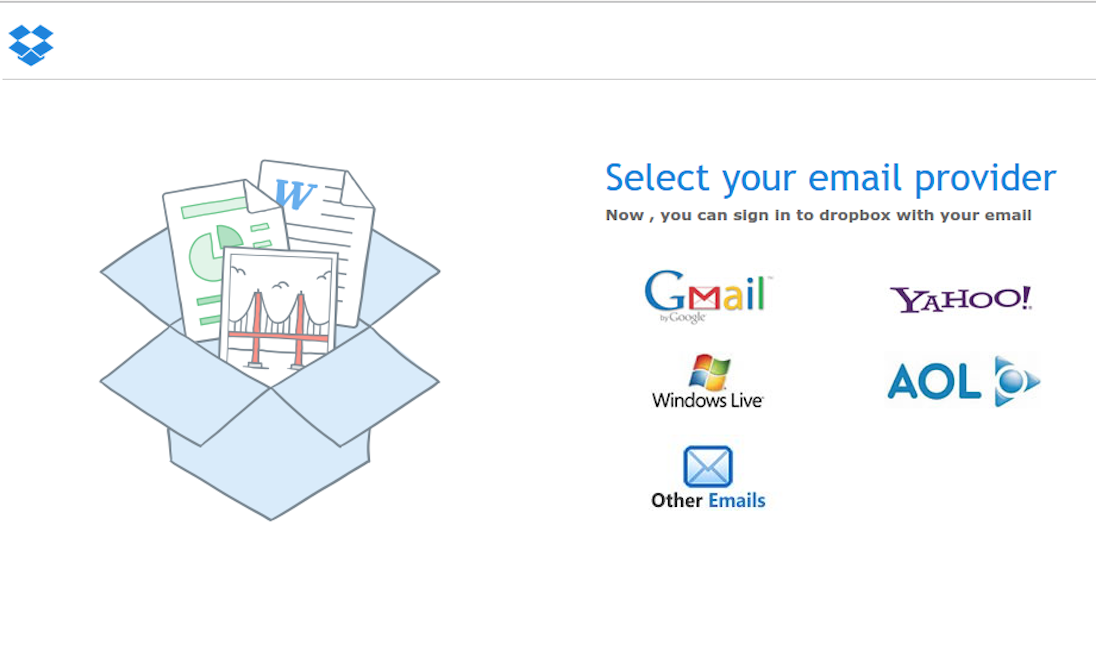
Should the email arrive in your inbox, you may be tempted to click on it. The attacker did not attempt to obfuscate the URL. Your browser will be directed straight to a .vn (Vietnam) site. The site is already blocklisted and your browser is likely going to warn you about the site. It appears, based on the URL, that the attacker compromised a Wordpress site to upload a simple phishing form. The form will offer the victim a number of different e-mail services to chose from, in order to "verify" the user's credentials. No matter which e-mail address / password is used, the victim will be directed to a google document, which should be another tip for the victim that they just fell for a phishing scam.
So there are many ways how a user will NOT fall for this email. But why do users still click even on simple emails like this?
- These e-mails tend to be most successful very early on in their live cycle, before blocklists pick up on them (I looked at the email a couple hours after it arrived in my inbox)
- Phishing is a numbers game. Out of thousands of phishing e-mails, only a few users will "click" and even less will enter their credentials. But then again, sending these emails is cheap
- Do not assume that all attackers are succesful and rolling in cash made from their illicit ventures. Just like other criminal undertakings, there are a few who make money, and an awful lot who live in their moms basement and dream of making money but don't have the skills to do it.
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
Anonymous
Aug 25th 2015
1 decade ago