Dridex Redirecting to Malicious Dropbox Hosted File Via Google
Thanks to Wayne for sending us in the latest Dridex sample. He observed them arriving this morning around 8am ET. According to Wayne, this malware may use Google Analytics to count how many people opened the file, but I haven't confirmed that. Google redirects are however used to obscure the destination.
Checking my own inbox, I found a couple of the messages in my spam folder. Here is an example I received:
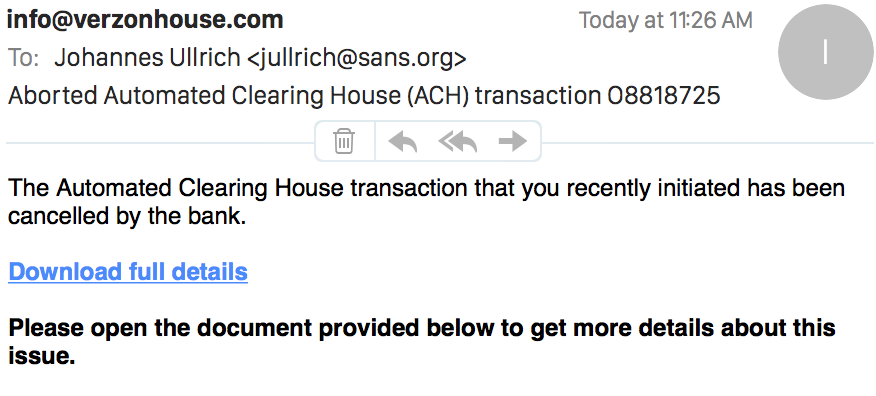 The link is kind of interesting. It leads to Google, but Google will redirect you to the malicious file which is hosted on dropbox. At least the file above was still available.
The link is kind of interesting. It leads to Google, but Google will redirect you to the malicious file which is hosted on dropbox. At least the file above was still available.
The link:
hxxps://www.google.com/url? q=https://www.dropbox.com/s/ 0c5we7id7mgwk89/ACH transaction0336.doc?dl=1 &sa=D&sntz=1&usg=AFQjCNFvX9uqV7uVjP8NWYKa4xkImgXPBA
Google will show a note that the user was redirected, but the file will download right away. It will not open, and the user will have to open it an enable the Macro to execute.
Hashes of the Word document:
MD5: f12cfa3f42784769c1542155a4f9cde8
SHA1: 5a939df2692091c89b5a75db3bba990aae3b6d10
And a quick review with fellow handler Didier's oledump tool shows indeed a number of suspect macros.
$ ./oledump.py -p ./plugin_dridex.py ../ACH\ transaction0336.doc -e
1: 114 '\x01CompObj'
2: 4096 '\x05DocumentSummaryInformation'
3: 4096 '\x05SummaryInformation'
4: 10927 '1Table'
5: 136110 'Data'
6: 666 'Macros/PROJECT'
7: 161 'Macros/PROJECTwm'
8: m 683 'Macros/VBA/Module1'
Plugin: Dridex decoder
9: m 683 'Macros/VBA/Module2'
Plugin: Dridex decoder
10: M 3592 'Macros/VBA/Module3'
Plugin: Dridex decoder
11: m 683 'Macros/VBA/Module4'
Plugin: Dridex decoder
12: M 2526 'Macros/VBA/Module5'
Plugin: Dridex decoder
13: M 10321 'Macros/VBA/ThisDocument'
Plugin: Dridex decoder
14: 5094 'Macros/VBA/_VBA_PROJECT'
15: 649 'Macros/VBA/dir'
16: 7220 'WordDocument'
Virustotal only shows 4 "hits" out of 57 AV tools tested for this binary
https://www.virustotal.com/en/file/efd9e8d6fe04bf8b7abcdd208c7f1b2b2fabf2ae09bce9775631047455cd533b/analysis/1429631351/
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
hxxps://www.google.com/url?q=https%3A%2F%2Fwww.dropbox.com%2Fs%2Fds1eifzw8wej5fr%2FACH%2520transfer2611.doc%3Fdl%3D1&sa=D&sntz=1&usg=AFQjCNEFqV5Vn-Y6oDa43qpV4x39RolDBQ
hxxps://www.dropbox.com/s/ds1eifzw8wej5fr/ACH%20transfer2611.doc?dl=1&sa=D&sntz=1&usg=AFQjCNEFqV5Vn-Y6oDa43qpV4x39RolDBQ
https://www.virustotal.com/en/file/8a7534b23f0133de3027f0bb0aa04b3b8ea61af275f2128a9dead90f3264ab5d/analysis/1429637255/
https://malwr.com/analysis/YjNlZjY4MGRhNGEyNDU5YWJiOWU4ZWU4ODdiMGUzMWI/
MD5: b504965c00c94aa93d093fb72035d200
SHA1: 18df8417fce6f9e24c8369a2897eaf29b1ec11c4
SHA256: 8a7534b23f0133de3027f0bb0aa04b3b8ea61af275f2128a9dead90f3264ab5d
Anonymous
Apr 21st 2015
1 decade ago
There is additional analysis there via Hybrid-Analysis and the variant that I received tries to connect to Belgium and China.
Anonymous
Apr 21st 2015
1 decade ago
I looked for Amazon.com, and copied the result link for it. (below)
http://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=1&cad=rja&uact=8&ved=0CB4QFjAA&url=http%3A%2F%2Fwww.amazon.com%2F&ei=oeI4VdPkEIHpgwST6oCoBw&usg=AFQjCNGcA9BfTgNdpb6LfcoG0sjA7hNW6A&bvm=bv.91427555,d.eXY
CT
Anonymous
Apr 23rd 2015
1 decade ago
https://www.google.com/url?q=https%3A%2F%2Fwww.dropbox.com%2Fs%2Fumcqamd258150yp%2FACH%2520payment7451.doc%3Fdl%3D1&sa=D&sntz=1&usg=AFQjCNFKCjmpr9H3RTfCBB_kgrX9lTX-ZA
Anonymous
Apr 23rd 2015
1 decade ago