Customized Support Scam Supported by Typo Squatting
This attack got it "all", and shows how hard it can be for a non ISC reader to evade some of these tech support scams. The URL used, http://login.microsoftlonine.com is only one letter off from the legit Microsoft Office 365 login page (you noticed the extra letter?).
The content you will get back varies. But here is a screenshot submitted by our reader Daniel:
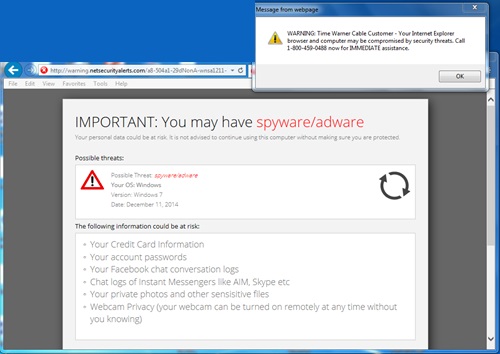
The user was redirected to warning.netsecurityalerts.com (the site appears down right now), and to bolster the site's credibility, it displays the user's correct ISP (we all know this is an easy whois lookup, but a user confronted with this message is much more likely to fall for it then a recent message).
Calling the 800 number now will lead to a sales system trying to sell you a medial alert button if you are 50 years or older.
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
Anonymous
Dec 15th 2014
1 decade ago
Anonymous
Dec 16th 2014
1 decade ago
Depends on how you count to "one":
... microsoft <L> on <missing-L> ine.com ...
One letter is out-of-place, but two "edits" are necessary to get to the actual Microsoft site.
The scammer's URL is:
... microsoft <L> on <L> ine.com ...
Don't go there! :-)
IE11 -> Tools -> Internet Options -> Security -> Restricted Sites -> type-'microsoftLonline.com' -> Add -> OK
Anonymous
Dec 16th 2014
1 decade ago
Anonymous
Dec 16th 2014
1 decade ago
Anonymous
Dec 16th 2014
1 decade ago
Anonymous
Dec 16th 2014
1 decade ago
http://gogle-analytics.com/cgi-bin/awstats.pl
http://gogleapis.com/cgi-bin/awstats.pl
Both are collecting stats on who loads scripts/css from them.
Anonymous
Dec 17th 2014
1 decade ago