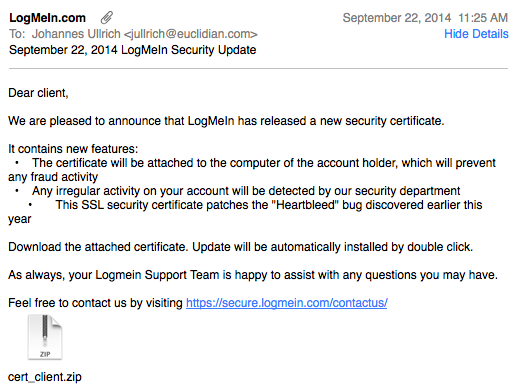
Fake LogMeIn Certificate Update with Bad AV Detection Rate
I just receive a pretty "plausible looking" e-mail claiming to originate from Logmein.com. The e-mail passed the first "gut check".
- The "From" address is auto-mailer@logmein.com.
- It was sent to an address I have used for Logmein in the past
- The only link inside the e-mail went to a legit Logmein URL.
Of course, the .zip attachment did set off some alarm bells, in particular as it unzipped to a .scr (Screen Saver).
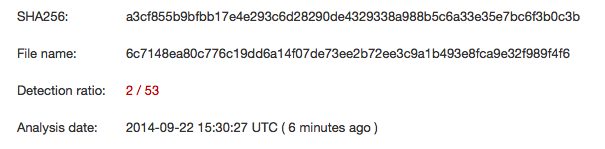
According to VirusTotal, AV detection is almost non-existant at this point:
LogmeIn does publish a SPF record, and the e-mail did not originate from a valid LogmeIn mail sender, so it should be easy to descriminate against these emails using a standard spam filter.
My next class:
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |
×
![modal content]()
Diary Archives


Comments
Anonymous
Sep 22nd 2014
1 decade ago
Anonymous
Sep 22nd 2014
1 decade ago
v=spf1 mx:3amlabs.com ip4:82.150.61.82 ip4:63.251.133.64/27 ip4:77.242.192.1 ip4:69.25.20.1 ip4:74.201.74.1 ip4:173.48.77.106 ip4:195.56.119.18 ip4:67.20.183.208/28 ip4:216.52.233.0/24 ip4:64.94.18.0/24 ip4:64.94.46.1 ip4:74.112.65.204 ip4:74.112.65.210 ip4:72.22.169.96/27 ip4:207.106.191.64/26 ip4:67.208.179.240/28 ip4:63.251.46.1 ip4:195.70.42.217 ip4:91.82.95.146 ip4:162.211.109.78 ip4:111.221.57.0/24 ip4:117.20.45.0/24 ip4:63.254.155.0/24
include:salesforce.com -all
Anonymous
Sep 22nd 2014
1 decade ago
Sanesecurity.Malware.24300.ZipHeur.UNOFFICIAL FOUND
Sanesecurity.Rogue.0hr.20140922-1644.UNOFFICIAL FOUND
ClamAV 3rd Party signatures: sanesecurity.com
Anonymous
Sep 23rd 2014
1 decade ago
Let me know if I can supply any other data...
Anonymous
Sep 23rd 2014
1 decade ago