Cryptodefense infection, some lessons learned
A few weeks ago I worked on a cryptodefense incident. A few things were done right in the organization and a few not so well. However in this particular instance there is a happy(ish) ending.
Cryptodefense made its appearance around February this year on the back of the success of Cryptolocker. The basics remain the same though and once infected the malware searches out PDF, doc(x), jpg and a few more document types and encrypts those. Files are encrypted using a RSA 2048 bit key which is placed in the user's AppData Directory (/Users/xxxxxx/AppData/Roaming/Microsoft/Crypto/RSA/S-1-5-21-254666440-1725212059-1820442801-6608/28093c3a55c1788ef10f8a6ac25eff17_55be799d-cb75-4e81-9059-484e3bdbf27e ). The application then starts encrypting files in various directories. From the mactime time line the /User/ directories are done first as well as the recycling bin.
|
Each directory containing encrypted files also has three files in them starting with HOW_DECRYPT. The file contains instructions on how to have your files decrypted after paying. The three files provide instructions on how to decrypt the file, or more accurately provide a link to where you can pay to get the decrypt application which will use the key on your machine to decrypt your files. |
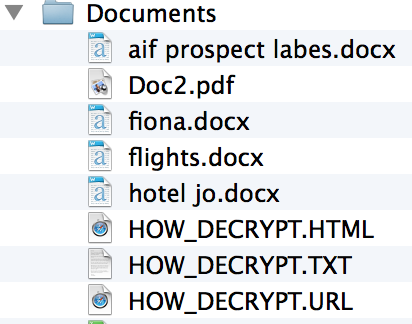 |
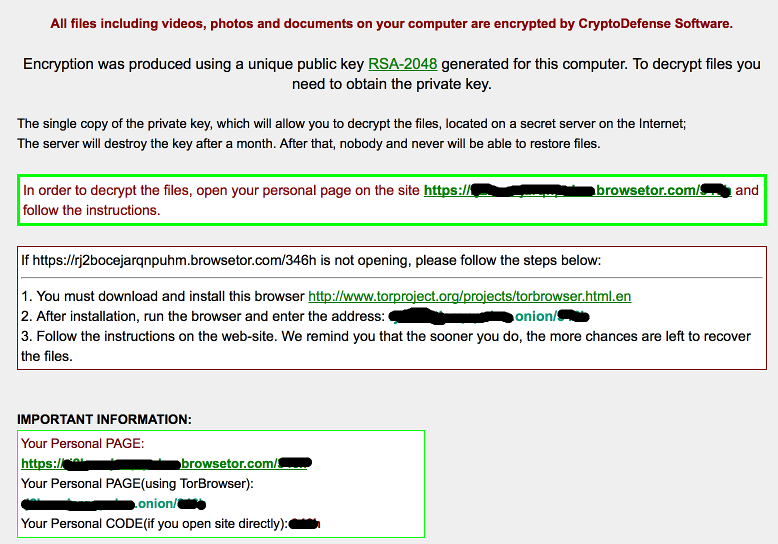
The impact of this particular malware can be devastating. Looking at what is left of the hard drive every directory that looks like it may have documents or pictures in it has been touched. This includes things like dropbox and network shares. In an incident elsewhere earlier in the year external harddrives were also encrypted.
The AV product used did not pick up this particular variant, nor did the web content filters. The AV did however find some malware (possibly related) on the machine around the same time the encryption processes started. However this was not responded to by the user or IT.
So what were the lessons learned in this instance? Well for starters backups are your friend. In this particular instance the organization had good backups of the files on the servers. So those files could be replaced from the backups. The Dropbox files were also ok as they have previous versions of the document available. Local files on the machines however did not have backups, so these were essentially lost (if infected with the pre April 2014 version you may have the key)*.
The other lesson learned was to take AV responses more seriously. Just because the AV says it has cleaned something does not necessarily mean that everything is gone, only the bits it knows about. In this instance it missed the malicious files (likely part of a Bing bar installation which happened prior to the infection starting), but picked up other rubbish that was running on the machine. Possibly a coincidence, but ... The encryption process took a few hours. Had the machine been pulled of the network when the infection was noticed, fewer files would have been affected.
So in short AV is not perfect, but respond when it tells you things have been infected. Secondly have viable backups, including files on roaming machines such as laptops. If not, be prepared to fork out money or go through a painful decrypting exercise (until they start putting the keys elsewhere).
Cheers
Mark H - Shearwater
*updated to clarify.


Comments
"Local files on the machines however did not have backups, so these were essentially lost (being decrypted, after all we have the key)"
If the key was present couldn't they be decrypted?
Anonymous
May 26th 2014
1 decade ago
But yes I could have put it better.
M
Anonymous
May 26th 2014
1 decade ago
If you only have the public key, you won't be able to decrypt the files unless the private key is also stored on the computer or if you caught it right after it has been generated and sent out to the cybercrooks.
So do you mean that the Cryotodefense version you have analyzed stores both keys on the victim's machine?
Anonymous
May 26th 2014
1 decade ago
M
Anonymous
May 26th 2014
1 decade ago
http://www.symantec.com/connect/blogs/cryptodefense-cryptolocker-imitator-makes-over-34000-one-month
Can you confirm that?
Anonymous
May 26th 2014
1 decade ago
Thanks,
Brian R.
Anonymous
May 27th 2014
1 decade ago
Jason
Anonymous
May 27th 2014
1 decade ago
Anonymous
May 27th 2014
1 decade ago