Massive spike in BGP traffic - Possible BGP poisoning?
Reader Yin wrote in after noticing a huge spike in unsolicited border gateway protocol (BGP) traffic. This same spike in BGP connections has also been noted on DShield's sensors [1]. Thankfully he provided a packet capture which contained numerous BGP OPEN [2] messages.
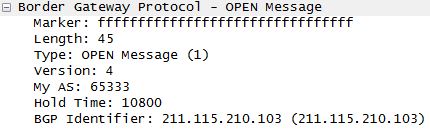
Here is a snippet of the BGP packet with the relevant details:
These messages all originated from the same system, based in Korea.
The Korean system IP is part of:
AS Number : AS9848
AS Name : SEJONGTELECOM-AS
From my understanding of BGP, this system is attempting to pass itself off as AS 65333, a private ASN [3] and poison the router with false details.
Whether misconfiguration or a malicious act is unknown at this point. Most, if not all routers should have basic protections in place to protect against this type of event having an effect [4].
Please let us know if you're seeing the same thing, can added anything further or if my analysis needs correcting.
UPDATE: Thank you to Reader Job for the clarification on private ASNs
[1] https://isc.sans.edu/port.html?port=179
[2] http://www.inetdaemon.com/tutorials/internet/ip/routing/bgp/operation/messages/open.shtml
[3] http://www.apnic.net/services/services-apnic-provides/helpdesk/faqs/asn-faqs#UsePrivateASN
[4] http://www.inetdaemon.com/tutorials/internet/ip/routing/bgp/security/index.shtml
Chris Mohan --- Internet Storm Center Handler on Duty


Comments
AS65333 is a so called 'private autonomous system', which are free to be used by anybody. can you explain why you correlate AS65333 with Cymru's Bogon Service? Is there data you left out of this post that supports this claim?
There are many organisations that use AS65333.
Job
Jun 28th 2012
1 decade ago
I've only seen AS 65333 used for Cymru's Bogon Service, so thanks for the clarification. I'll update the diary.
Chris
Jun 28th 2012
1 decade ago
Jason R
Jun 28th 2012
1 decade ago
MattS
Jun 28th 2012
1 decade ago