Webshells, Webshells everywhere!
I recently started experimenting with a new page to analyze our web honeypot data. This page lists all URLs not seen before. (see https://isc.sans.edu/weblogs/firstseenurls.html ). So far, this has been useful in finding some new or exciting data.
For example, yesterday, an attacker started scanning for webshells. These scans popped up because the attacker also supplied some unique parameters to the shells (not sure these parameters made sense, but they helped me :) ).
The IP in question, 97.89.144.44, sent 28454 requests to 40 of our honeypots (some of the honeypots cover multiple IP addresses). 941 different URLs were probed, and about 150 distinct URLs after removing the parameters. Too many to list them all here, but this is a list of the more popular requests:
/PHPSPY.php
/egy.php
/Loaderz_WEB_Shell.php
/FaTaLisTiCz_Fx.php
/Simple_PHP_backdoor.php
/c99_locus7s.php
/c99ud.php
/Moroccan_Spamers.php
/PHANTASMA.php
/locus.php
/iskorpitx.php
/c99-Ultimate.php
/ironshell.php
/filesman.php
/antichat.php
/aspydrv.php
/c99v2.php
/sniper.php
/c100.php
/cbfphpsh.php
Webshells are one of the more common payloads delivered by various exploits. They provide an attacker with persistent and convenient access to a compromised site. Usually, webshells use some form of authentication, but attackers are making mistakes too, and default passwords are about as common in webshells as in the applications they compromise. As a defender, it is essential to look out for unauthorized changes to your code, which may point to the inclusion of webshells. Attackers may use a compromised developer workstation or library to sneak a webshell into your site. Below is a code snippet from the old PHPSPY webshell (#1 on the list scanned) that shows the default password used by this webshell. And yes, the comment above the password translates to "If password verification is required, please modify the login password."
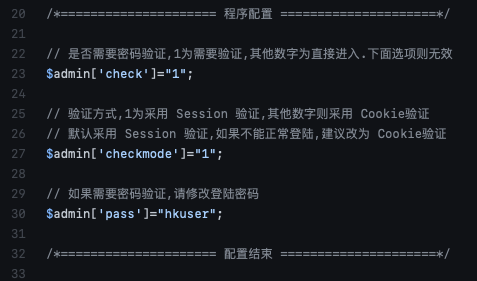
The source IP for these attacks has had a couple of dozen other reports from back in June. This appears to be a cable modem IP address (Spectrum/Charter communications). The activity stopped today. I hope the victim managed to clean up their system, or the ISP notified them of the activity.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments