How was your stay at the Hotel La Playa?
I made the following demo for a customer in the scope of a security awareness event. When speaking to non-technical people, it's always difficult to demonstrate how easily attackers can abuse of their devices and data. If successfully popping up a "calc.exe" with an exploit makes a room full of security people crazy, it's not the case for "users". It is mandatory to demonstrate something that will ring a bell in their mind.
As people want to be constantly online, they (ab)use of wireless access points. By default, connected devices keep a history of all used wireless networks and constantly try to find them again. The idea of the demo is simple:
- Collect all the SSID's broadcasted by mobile devices present in the audience
- Geolocate the SSID's using the Wigle API
- Display them on a map
[Note: For privacy reason, this demo must be performed with the authorization of people in the audience]
First, collect SSID's using tshark and a Wireless network card that can be switch into monitoring mode:
# iwconfig $interface mode monitor # ifconfig $interface up # tshark -i $interface -n -l subtype probereq | tee -a /tmp/ssids.tmp Feb 7 18:37:39 Probe Request from 08:ee:8b:xx:xx:xx for SSID 'xxxx Airport' Feb 7 18:36:54 20:a2:e4:xx:xx:xx trying to associate with 'Free Wireless' Feb 7 18:36:49 Probe Request from 20:a2:e4:xx:x:xx for SSID 'Free Wireless' Feb 7 18:36:25 Probe Request from 58:40:4e:xx:xx:xx for SSID 'Free Wireless' Feb 7 18:36:22 Probe Request from 0c:e7:25:xx:xx:xx for SSID 'Free' Feb 7 18:36:12 Probe Request from e8:50:8b:xx:xx:xx for SSID 'xxxxx-wifi' Feb 7 18:36:04 f0:25:b7:xx:xx:xx trying to associate with 'Airport_Free_xxxxxx' Feb 7 18:36:04 Probe Request from f0:25:b7:xx:xx:xx for SSID 'Airport_Free_WiFi_xxxxxx' Feb 7 18:35:46 64:9a:be:xx:xx:xx trying to associate with 'swisscom' Feb 7 18:35:46 Probe Request from 64:9a:be:xx:xx:xx for SSID 'swisscom' Feb 7 18:35:40 Probe Request from 24:77:03:xx:xx:xx for SSID 'UM' Feb 7 18:35:38 Probe Request from 24:77:03:xx:xx:xx for SSID 'UM' Feb 7 18:35:34 Probe Request from 20:a9:9b:xx:xx:xx for SSID 'xxxxx' Feb 7 18:35:31 Probe Request from 20:a2:e4:xx:xx:xx for SSID 'Free Wireless' Feb 7 18:35:15 Probe Request from 8c:00:6d:xx:xx:xx for SSID 'xxxxNET' Feb 7 18:35:15 Probe Request from 80:ea:96:xx:xx:xx for SSID 'Airport_Free_WiFi' Feb 7 18:35:10 38:ca:da:xx:xx:xx trying to associate with 'xxxxNET'
Let tshark collect SSID's for a few minutes (the list will quickly grow). The next step is to use the Wigle[1] API to get geolocation data.
[Note: The free API allows only a limited number of queries per day]
I wrote a Python script[2] which queries the API and generates a CSV file:
# grep SSID /tmp/ssids.tmp | awk -F "'" '{ print $(NF-1) }'| sort -u >wigle.data
# python wigle.py
# head wigle.csv
SSID,Lat,Lon
AIRPORT FREE WIFI,50.88093567,7.11556339
AIRPORT FREE WIFI,28.45140457,-13.8698101
AIRPORT FREE WIFI,43.30202866,-8.38176537
xxxxxxxxxxx,43.52931595,5.45100164
xxxxxxxxxxx,36.88293457,10.33142185
xxxxxxxxxxx,48.85987091,2.22434855
xxxxx,40.48699951,-3.58421397
Airport_Free_WiFi,-6.86642265,39.20762634
Airport_Free_WiFi,52.30990219,4.76001358
The last step is to map those coordinates on a world map. Splunk does this with just one query:
| inputcsv wigle.csv | stats count by SSID, Lat, Lon | geostats latfield=Lat longfield=Lon count by SSID
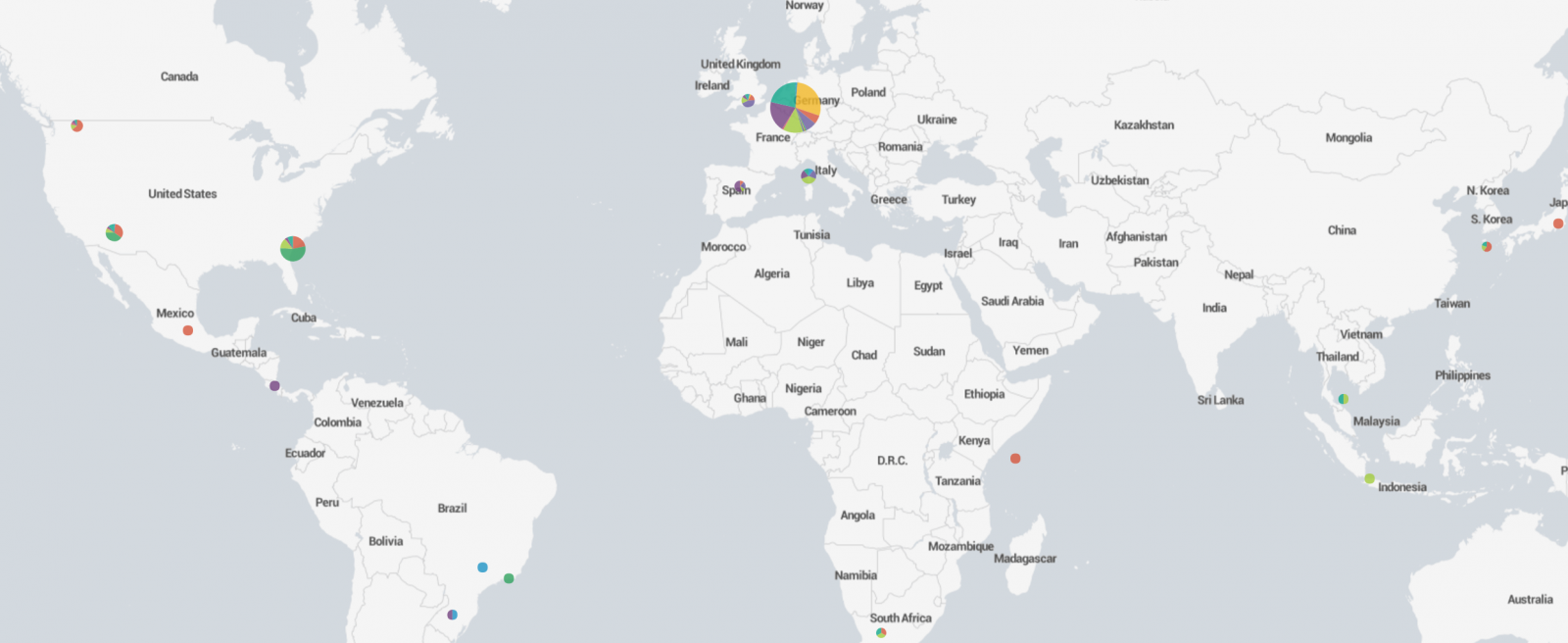
A zoom on the map may reveal nice locations where your victim could have spent some fun times:
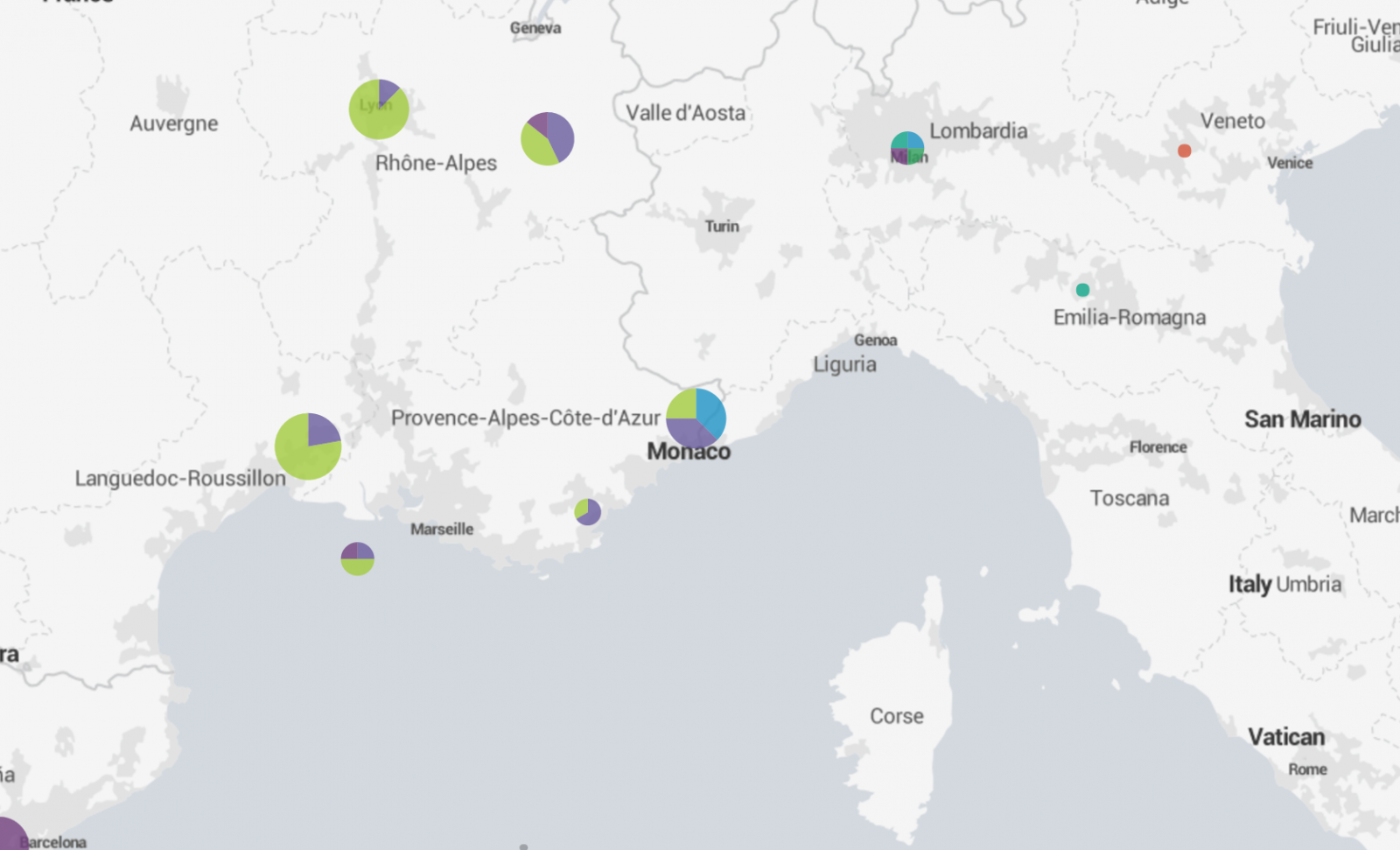
What about the accuracy of those maps? It relies on the Wigle database which is populated by volunteers. Generic SSID's like "Free Wifi" or "Guest" won't give good results but a unique hotel name will make it perfectly. It is not possible to put the broadcasted SSID's on a timeline to track the moves in the past but it's easy to spot two people who met or visited the same place in the past.
Given that people keep their phone default name ("iPhone of John Doe"), this demo generates always a little stress when you ask the victim: "So, Mr Doe, How was your stay at the hotel La Playa?".
[1] https://wigle.net/index
[2] https://github.com/xme/toolbox/blob/master/wigle.py
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments
SSID probes but don't send the devices (host) name.
The host name will be sent when the device connects to an access point's DHCP server.
[quote]Generic SSID's like "Free Wifi" or "Guest" won't give good results[/quote]
Windows stores the SSID plus MAC address of the AP/default gateway of "known" networks in the registry. Apple's and Google's geolocation services record MAC addresses...
Anonymous
Feb 15th 2017
8 years ago
i stayed at Hotel La Playa.
i used that wifi SSID
i'm now out of range of the hotel.
my iPhone is probing for that SSID
but that SSID does not show up on my iPhone to "forget" that SSID since it is out of range.
how would one remove a remembered SSID without making another SSID in range on a WAP i control?
Anonymous
Feb 16th 2017
8 years ago
Anonymous
Feb 17th 2017
8 years ago
1 )use a wifi sniffer to find and note those SSIDs
2) configure a wireless access point with each of those SSIDs
3) disconnect the iPhone and access each SSID that was not in range before
4) forget those SSIDs
or
reset network and add the needed/desired SSIDs back to the iPhone
this seems to be a big security problem.
I can sniff, configure a WAP with the SSIDs in probe requests.
then dauth the iPhone, hope it connects to that SSID.
Anonymous
Feb 17th 2017
8 years ago
Anonymous
Feb 21st 2017
8 years ago
Anonymous
Feb 22nd 2017
8 years ago
I've registered with Wigle, but can't find my API key to put into the script, any ideas where I can find it??
Thanks.
Anonymous
Feb 24th 2017
8 years ago
Anonymous
Feb 26th 2017
8 years ago
This is an excellent demo for security awareness! I tried to simulate it but appears to have run into a snag with the wigle.py API script. It appears that there is a keyerror associated with the JSON response. Do you think its because there was an update to the API?
Anonymous
Mar 13th 2017
8 years ago