Fake Australian Electric Bill Leads to Cryptolocker
Our reader Mark sent us a link he recovered from a Phishing e-mail. We don't have the e-mail right now, but the web site delivering the malware is kind of interesting in itself.
The e-mail claims to come from "Energy Australia", an actual Australian utility company, and the link leads to:
hxxp://energymar.com/ data/ electricity/ view/get/ energy.php ?eid=[long number]
Note the somewhat plausible domain name (energymar.com). The actual domain name for Energy Australia is "www.energyaustralia.com.au".
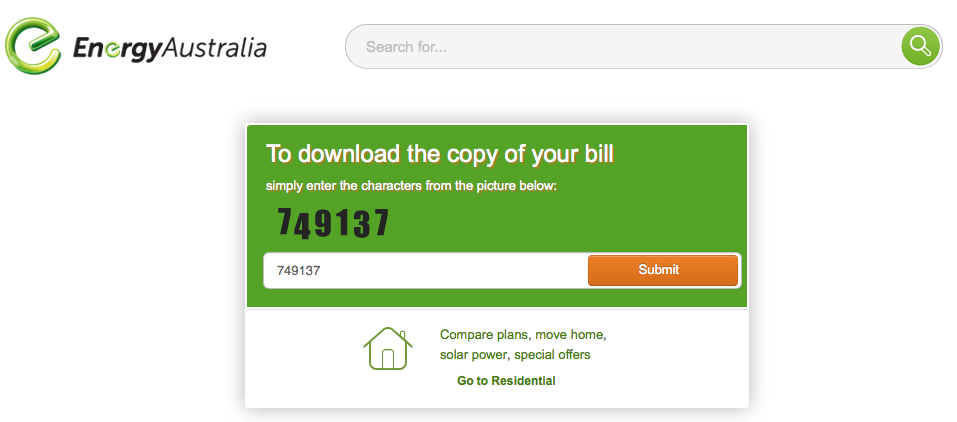
The first screen presented to the user asks the user to solve a very simple CAPTCHA. This is likely put in place to hinder automatic analysis of the URL:
(click on images to see full size)
The layout of the page matches the original very well. Users are confronted with CAPTCHAs regularly in similar sites, so I doubt this will raise suspicion.
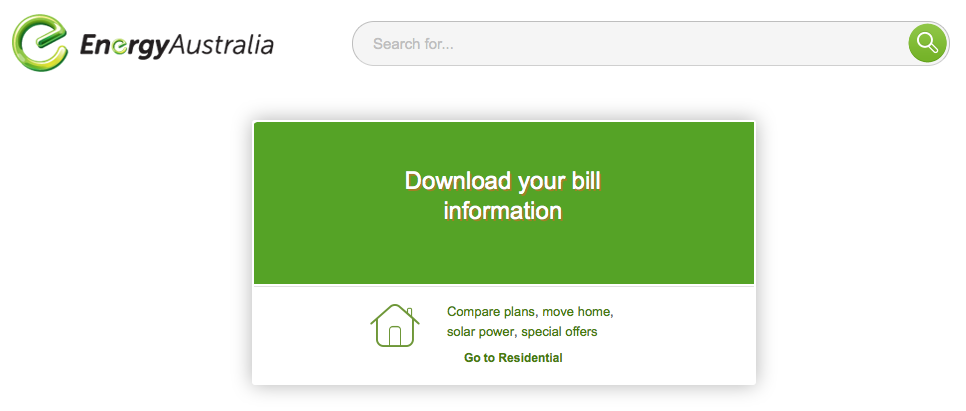
Next, we are asked to download the file, again using a similar layout.
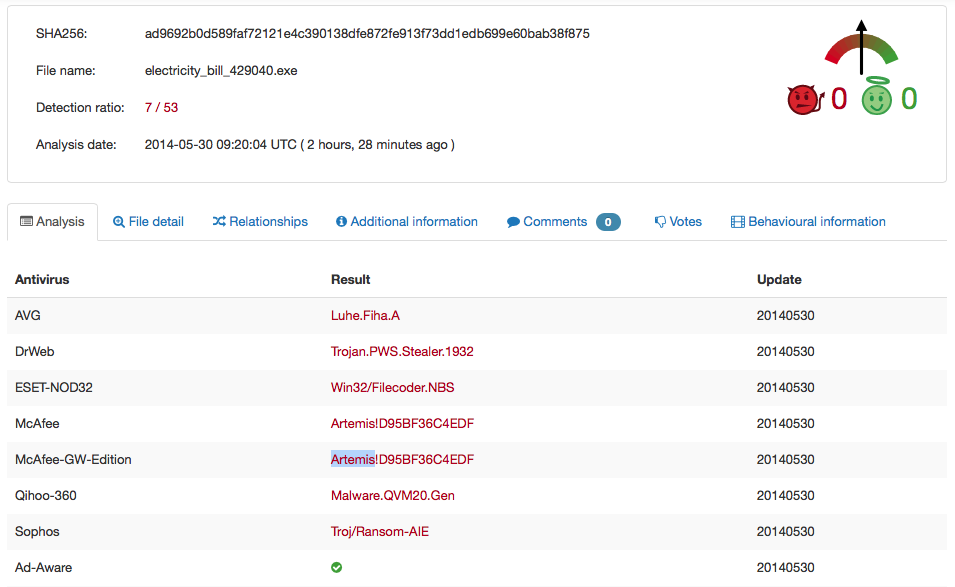
The "bill" itself is a ZIP file that includes a simple ZIP file that expands to an EXE. Virustotal shows spotty detection:
You can also review the full updated results here: https://www.virustotal.com/en/file/ad9692b0d589faf72121e4c390138dfe872fe913f73dd1edb699e60bab38f875/analysis/
It doesn't look like the checksum of this sample changes between downloads, so I hope AV signatures will catch up quickly.
Once downloaded and unzipped, the malware presents itself as a PDF:
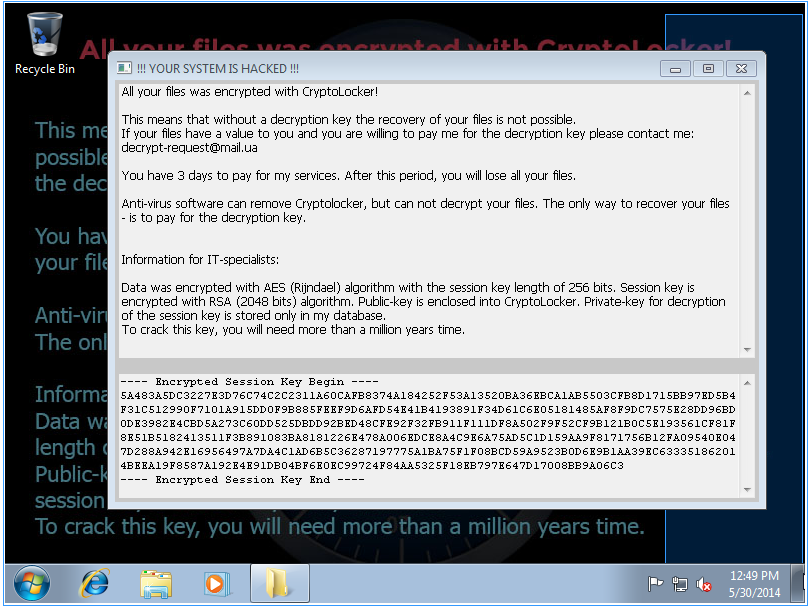
But then, as soon as the malware is launched, it does reveal it's true nature:
We ran this on a fresh Windows 7 Ultimate SP1 32 Bit install with one round of patches, so there wasn't much to encrypt for Cryptolocker.
After launching the malware, the system connected via https to 151.248.118.193.( vps.regruhosting.ru ), likely to retrieve/send the key. I did not see a DNS lookup. The self signed SSL certificate include the IP address 213.183.60.75 as a Subject:
Serial Number:
b7:ff:8c:36:d5:71:51:b2
Signature Algorithm: sha1WithRSAEncryption
Issuer: CN=213.183.60.75
Validity
Not Before: Apr 10 09:41:14 2012 GMT
Not After : Apr 8 09:41:14 2022 GMT
Subject: CN=213.183.60.75
---
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
Anonymous
May 30th 2014
1 decade ago
best way to send us a file: encrypted zip with password "infected".
Thanks!
Anonymous
May 30th 2014
1 decade ago
398 450179:DHCPS: 1:0x001aa09f4bd2, 192.168.1.100, ACK in request.
399 452312:DHCPS: 1:0x002215a1b903, 192.168.1.101, ACK in request.
400 452891:DHCPS: 1:0x001aa09f4bd2, 192.168.1.100, ACK in request.
Time = 2014-05-30 16:16:45 453601s
H-Ver = TL-R860 v5 1001225B : S-Ver = 4.3.3 Build 100519 Rel.41023n
L = 192.168.1.1 : M = 255.255.255.0
W1 = DHCP : W = 99.225.236.35 : M = 255.255.254.0 : G = 99.225.236.1
Free=4992, Busy=38, Bind=36, Inv=0/6, Bc=0/10, Dns=0, cl=256, fc=0/0, sq=0/0
Anonymous
May 30th 2014
1 decade ago
Anonymous
May 31st 2014
1 decade ago