What are they looking for? Scans for OpenID Connect Configuration (Update: CitrixBleed)
Update: Thanks to our reader Dustin Decker for pointing out that these scans are likely looking for Citrix devices. The recent "CitrixBleed" vulnerability is exploited using the OpenID connect URL (CVE-2023-4966, CVE-2023-4967). An attack would also include an oversized Host header in a request to the OpenID URL. The scans I have observed do not appear to include this oversized Host header. Looks like they are just looking for possible targets to exploit later.
One of our honeypots received unusually many requests for an OpenID connect configuration file. This honeypot is configured a bit differently as it is more experimental to test new software, so the logs do not show up on our main site. Overall, there are only a few requests targeting this specific URL.
OpenID connected is an authentication scheme often used by websites to facilitate features like "Log in with Facebook/Google...". The specification asks for a configuration file, .well-known/openid-configuration, to facilitate the automatic discovery of OpenID connect capabilities.
The URL, /oauth/idp/.well-known/openid-configuration, has only been seen a few times by our "normal" honeypots. But the development honeypot has seen about a dozen requests per IP address.
The scans appear to originate from four different IP addresses, all hosted with XHOST INTERNET SOLUTIONS, a company with an address in England.
185.73.124.213: Our other honeypots see requests for the index page (/) from this IP address, but only on December 12th. My best guess is that the IP address is located in the Netherlands. Shodan has no information about the IP address.
185.73.124.214: Same network as above. Again, no information in Shodan. This IP started scanning for "/" a day after the address above (December 13th).
80.66.66.190: This IP is also part of XHOST but uses ASN51765. This puts it likely in Russia. We do not have any activity from our normal sensors for this IP, and Shodan shows an open RDP server. Interestingly, Shodan also shows Ubuntu running on this IP based on the web server headers (and ssh). This may be a NAT gateway forwarding traffic to other hosts.
%i%p:80.66.83.180%%: Same network as 80.66.66.190; Shodan shows an NGINX server running at this IP address (Ubuntu). We do have a few prior reports from this IP address going back to November 29th.
My real question: Is there anything that could leak in openid-configuration? Obviously, it may indicate the presence of a specific OpenID implementation. But have there been any recent vulnerabilities that these scans may be looking for? I hope to adjust our honeypots to deliver a more appropriate response in these cases.
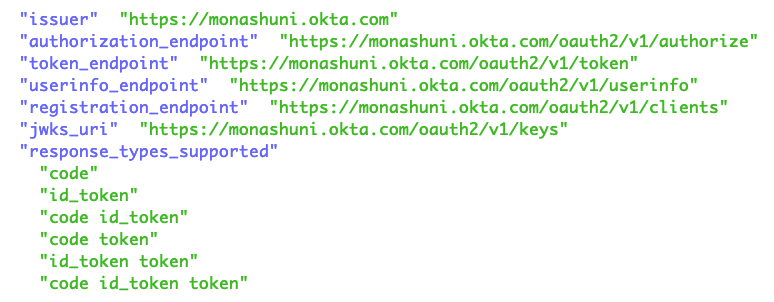
As an example, Googling leads to this sample: https://monashuni.okta.com/.well-known/openid-configuration
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|


Comments