Apple Updates Everything
Today, Apple released macOS, iOS, iPadOS, tvOS, watchOS, and Safari updates.
Three of the vulnerabilities are already exploited in the wild. Combining the three vulnerabilities, an attacker can gain complete system access as the user visits a malicious website. CVE-2023-32373 allows for arbitrary code execution as WebKit processes malicious content. CVE-2023-32409, in turn, enables breaking out of the web content sandbox, completing the full system compromise. The vulnerabilities are not indicated as "patched" for older versions of macOS, but they are covered in the Safari update, which applies the patch to older versions of macOS.
As usual, Apple's vulnerability descriptions are terse. As promised in a prior diary, I let ChatGPT "guess" the CVSS score for these updates. Let me know if you agree or not. The rating (moderate/important/critical) are mine. ChatGPT refused to provide a CVSS score for some vulnerabilities based on insufficient information. Let me know if you feel ChatGPT did ok or not (or if it is worthwhile keeping these ChatGPT CVSS scores or not)
| Safari 16.5 | watchOS 9.5 | tvOS 16.5 | iOS 16.5 and iPadOS 16.5 | iOS 15.7.6 and iPadOS 15.7.6 | macOS Big Sur 11.7.7 | macOS Ventura 13.4 | macOS Monterey 12.6.6 |
|---|---|---|---|---|---|---|---|
| CVE-2023-32402 [moderate] ChatGPT-CVSS: 4.3 WebKit An out-of-bounds read was addressed with improved input validation. Processing web content may disclose sensitive information |
|||||||
| x | x | x | x | x | |||
| CVE-2023-32423 [moderate] ChatGPT-CVSS: 5.3 WebKit A buffer overflow issue was addressed with improved memory handling. Processing web content may disclose sensitive information |
|||||||
| x | x | x | x | x | |||
| CVE-2023-32409 [moderate] ChatGPT-CVSS: 8.8 *** EXPLOITED *** WebKit The issue was addressed with improved bounds checks. A remote attacker may be able to break out of Web Content sandbox. Apple is aware of a report that this issue may have been actively exploited. |
|||||||
| x | x | x | x | x | |||
| CVE-2023-28204 [moderate] ChatGPT-CVSS: 7.5 *** EXPLOITED *** WebKit An out-of-bounds read was addressed with improved input validation. Processing web content may disclose sensitive information. Apple is aware of a report that this issue may have been actively exploited. |
|||||||
| x | x | x | x | x | x | ||
| CVE-2023-32373 [critical] ChatGPT-CVSS: 8.8 *** EXPLOITED *** WebKit A use-after-free issue was addressed with improved memory management. Processing maliciously crafted web content may lead to arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited. |
|||||||
| x | x | x | x | x | x | ||
| CVE-2023-32388 [important] ChatGPT-CVSS: N/A Accessibility A privacy issue was addressed with improved private data redaction for log entries. An app may be able to bypass Privacy preferences |
|||||||
| x | x | x | x | x | x | ||
| CVE-2023-32400 [moderate] ChatGPT-CVSS: N/A Accessibility This issue was addressed with improved checks. Entitlements and privacy permissions granted to this app may be used by a malicious app |
|||||||
| x | x | x | |||||
| CVE-2023-32399 [important] ChatGPT-CVSS: 4.3 Core Location The issue was addressed with improved handling of caches. An app may be able to read sensitive location information |
|||||||
| x | x | x | x | ||||
| CVE-2023-28191 [important] ChatGPT-CVSS: N/A AppleEvents This issue was addressed with improved redaction of sensitive information. An app may be able to bypass Privacy preferences |
|||||||
| x | x | x | x | x | x | ||
| CVE-2023-32417 [moderate] ChatGPT-CVSS: 4.0 Face Gallery This issue was addressed by restricting options offered on a locked device. An attacker with physical access to a locked Apple Watch may be able to view user photos or contacts via accessibility features |
|||||||
| x | |||||||
| CVE-2023-32392 [important] ChatGPT-CVSS: 4.3 GeoServices A privacy issue was addressed with improved private data redaction for log entries. An app may be able to read sensitive location information |
|||||||
| x | x | x | x | x | x | ||
| CVE-2023-32372 [important] ChatGPT-CVSS: 5.3 ImageIO An out-of-bounds read was addressed with improved input validation. Processing an image may result in disclosure of process memory |
|||||||
| x | x | x | x | ||||
| CVE-2023-32384 [critical] ChatGPT-CVSS: 7.8 ImageIO A buffer overflow was addressed with improved bounds checking. Processing an image may lead to arbitrary code execution |
|||||||
| x | x | x | x | x | x | x | |
| CVE-2023-32354 [important] ChatGPT-CVSS: 7.5 IOSurfaceAccelerator An out-of-bounds read was addressed with improved input validation. An app may be able to disclose kernel memory |
|||||||
| x | x | x | |||||
| CVE-2023-32420 [moderate] ChatGPT-CVSS: 7.5 IOSurfaceAccelerator An out-of-bounds read was addressed with improved input validation. An app may be able to cause unexpected system termination or read kernel memory |
|||||||
| x | x | x | x | ||||
| CVE-2023-27930 [important] ChatGPT-CVSS: 8.8 Kernel A type confusion issue was addressed with improved checks. An app may be able to execute arbitrary code with kernel privileges |
|||||||
| x | x | x | x | ||||
| CVE-2023-32398 [important] ChatGPT-CVSS: 8.8 Kernel A use-after-free issue was addressed with improved memory management. An app may be able to execute arbitrary code with kernel privileges |
|||||||
| x | x | x | x | x | x | x | |
| CVE-2023-32413 [important] ChatGPT-CVSS: 8.8 Kernel A race condition was addressed with improved state handling. An app may be able to gain root privileges |
|||||||
| x | x | x | x | x | x | x | |
| CVE-2023-32352 [important] ChatGPT-CVSS: 7.0 LaunchServices A logic issue was addressed with improved checks. An app may bypass Gatekeeper checks |
|||||||
| x | x | x | x | x | |||
| CVE-2023-32407 [important] ChatGPT-CVSS: N/A Metal A logic issue was addressed with improved state management. An app may be able to bypass Privacy preferences |
|||||||
| x | x | x | x | x | x | x | |
| CVE-2023-32368 [important] ChatGPT-CVSS: 6.5 Model I/O An out-of-bounds read was addressed with improved input validation. Processing a 3D model may result in disclosure of process memory |
|||||||
| x | x | x | x | x | |||
| CVE-2023-32403 [important] ChatGPT-CVSS: 4.3 NetworkExtension This issue was addressed with improved redaction of sensitive information. An app may be able to read sensitive location information |
|||||||
| x | x | x | x | x | x | x | |
| CVE-2023-32390 [moderate] ChatGPT-CVSS: 4.3 Photos The issue was addressed with improved checks. Photos belonging to the Hidden Photos Album could be viewed without authentication through Visual Lookup |
|||||||
| x | x | x | |||||
| CVE-2023-32357 [moderate] ChatGPT-CVSS: 7.0 Sandbox An authorization issue was addressed with improved state management. An app may be able to retain access to system configuration files even after its permission is revoked |
|||||||
| x | x | x | x | x | x | ||
| CVE-2023-32391 [moderate] ChatGPT-CVSS: N/A Shortcuts The issue was addressed with improved checks. A shortcut may be able to use sensitive data with certain actions without prompting the user |
|||||||
| x | x | x | x | ||||
| CVE-2023-32404 [important] ChatGPT-CVSS: 6.2 Shortcuts This issue was addressed with improved entitlements. An app may be able to bypass Privacy preferences |
|||||||
| x | x | x | |||||
| CVE-2023-32394 [moderate] ChatGPT-CVSS: 5.3 Siri The issue was addressed with improved checks. A person with physical access to a device may be able to view contact information from the lock screen |
|||||||
| x | x | x | x | ||||
| CVE-2023-32376 [important] ChatGPT-CVSS: 7.0 StorageKit This issue was addressed with improved entitlements. An app may be able to modify protected parts of the file system |
|||||||
| x | x | x | x | ||||
| CVE-2023-28202 [moderate] ChatGPT-CVSS: N/A System Settings This issue was addressed with improved state management. An app firewall setting may not take effect after exiting the Settings app |
|||||||
| x | x | x | x | ||||
| CVE-2023-32412 [moderate] ChatGPT-CVSS: 7.8 Telephony A use-after-free issue was addressed with improved memory management. A remote attacker may be able to cause unexpected app termination or arbitrary code execution |
|||||||
| x | x | x | x | x | x | x | |
| CVE-2023-32408 [important] ChatGPT-CVSS: 7.5 TV App The issue was addressed with improved handling of caches. An app may be able to read sensitive location information |
|||||||
| x | x | x | x | x | x | ||
| CVE-2023-32389 [important] ChatGPT-CVSS: 7.5 Wi-Fi This issue was addressed with improved redaction of sensitive information. An app may be able to disclose kernel memory |
|||||||
| x | x | x | x | ||||
| CVE-2023-32411 [important] ChatGPT-CVSS: 6.5 AppleMobileFileIntegrity This issue was addressed with improved entitlements. An app may be able to bypass Privacy preferences |
|||||||
| x | x | x | x | x | |||
| CVE-2023-32422 [moderate] ChatGPT-CVSS: 6.5 SQLite This issue was addressed by adding additional SQLite logging restrictions. An app may be able to access data from other apps by enabling additional SQLite logging |
|||||||
| x | x | x | |||||
| CVE-2023-32415 [important] ChatGPT-CVSS: 5.3 Weather This issue was addressed with improved redaction of sensitive information. An app may be able to read sensitive location information |
|||||||
| x | x | x | |||||
| CVE-2023-32371 [important] ChatGPT-CVSS: 6.5 Associated Domains The issue was addressed with improved checks. An app may be able to break out of its sandbox |
|||||||
| x | x | ||||||
| CVE-2023-32419 [moderate] ChatGPT-CVSS: 8.8 Cellular The issue was addressed with improved bounds checks. A remote attacker may be able to cause arbitrary code execution |
|||||||
| x | |||||||
| CVE-2023-32385 [moderate] ChatGPT-CVSS: 4.3 PDFKit A denial-of-service issue was addressed with improved memory handling. Opening a PDF file may lead to unexpected app termination |
|||||||
| x | x | ||||||
| CVE-2023-32365 [moderate] ChatGPT-CVSS: N/A Photos The issue was addressed with improved checks. Shake-to-undo may allow a deleted photo to be re-surfaced without authentication |
|||||||
| x | x | ||||||
| CVE-2023-32367 [important] ChatGPT-CVSS: 7.5 Security This issue was addressed with improved entitlements. An app may be able to access user-sensitive data |
|||||||
| x | x | ||||||
| CVE-2023-23532 [important] ChatGPT-CVSS: 7.0 Apple Neural Engine This issue was addressed with improved checks. An app may be able to break out of its sandbox |
|||||||
| x | |||||||
| CVE-2023-28181 [important] ChatGPT-CVSS: 9.8 CoreCapture The issue was addressed with improved memory handling. An app may be able to execute arbitrary code with kernel privileges |
|||||||
| x | x | ||||||
| CVE-2023-32410 [important] ChatGPT-CVSS: 7.5 IOSurface An out-of-bounds read was addressed with improved input validation. An app may be able to leak sensitive kernel state |
|||||||
| x | x | x | x | ||||
| CVE-2023-27940 [moderate] ChatGPT-CVSS: 4.0 Kernel The issue was addressed with additional permissions checks. A sandboxed app may be able to observe system-wide network connections |
|||||||
| x | x | x | |||||
| CVE-2023-32397 [important] ChatGPT-CVSS: 6.5 Shell A logic issue was addressed with improved state management. An app may be able to modify protected parts of the file system |
|||||||
| x | x | x | x | ||||
| CVE-2023-32386 [moderate] ChatGPT-CVSS: 5.0 Contacts A privacy issue was addressed with improved handling of temporary files. An app may be able to observe unprotected user data |
|||||||
| x | x | x | |||||
| CVE-2023-32360 [moderate] ChatGPT-CVSS: 6.5 CUPS An authentication issue was addressed with improved state management. An unauthenticated user may be able to access recently printed documents |
|||||||
| x | x | x | |||||
| CVE-2023-32387 [moderate] ChatGPT-CVSS: 8.8 dcerpc A use-after-free issue was addressed with improved memory management. A remote attacker may be able to cause unexpected app termination or arbitrary code execution |
|||||||
| x | x | x | |||||
| CVE-2023-27945 [moderate] ChatGPT-CVSS: 4.3 Dev Tools This issue was addressed with improved entitlements. A sandboxed app may be able to collect system logs |
|||||||
| x | x | ||||||
| CVE-2023-32369 [important] ChatGPT-CVSS: 6.5 libxpc A logic issue was addressed with improved state management. An app may be able to modify protected parts of the file system |
|||||||
| x | x | x | |||||
| CVE-2023-32405 [important] ChatGPT-CVSS: 7.8 libxpc A logic issue was addressed with improved checks. An app may be able to gain root privileges |
|||||||
| x | x | x | |||||
| CVE-2023-32380 [critical] ChatGPT-CVSS: 8.8 Model I/O An out-of-bounds write issue was addressed with improved bounds checking. Processing a 3D model may lead to arbitrary code execution |
|||||||
| x | x | x | |||||
| CVE-2023-32382 [important] ChatGPT-CVSS: 5.3 Model I/O An out-of-bounds read was addressed with improved input validation. Processing a 3D model may result in disclosure of process memory |
|||||||
| x | x | x | |||||
| CVE-2023-32355 [important] ChatGPT-CVSS: 7.5 PackageKit A logic issue was addressed with improved state management. An app may be able to modify protected parts of the file system |
|||||||
| x | x | x | |||||
| CVE-2023-32395 [important] ChatGPT-CVSS: 7.0 Perl A logic issue was addressed with improved state management. An app may be able to modify protected parts of the file system |
|||||||
| x | x | x | |||||
| CVE-2023-32414 [important] ChatGPT-CVSS: 4.0 DesktopServices The issue was addressed with improved checks. An app may be able to break out of its sandbox |
|||||||
| x | |||||||
| CVE-2023-32375 [important] ChatGPT-CVSS: 7.5 Model I/O An out-of-bounds read was addressed with improved input validation. Processing a 3D model may result in disclosure of process memory |
|||||||
| x | x | ||||||
| CVE-2023-32363 [important] ChatGPT-CVSS: 0 Screen Saver A permissions issue was addressed by removing vulnerable code and adding additional checks. An app may be able to bypass Privacy preferences |
|||||||
| x | |||||||
| CVE-2023-23535 [important] ChatGPT-CVSS: 7.5 ImageIO The issue was addressed with improved memory handling. Processing a maliciously crafted image may result in disclosure of process memory |
|||||||
| x | |||||||
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
A Quick Survey of .zip Domains: Your highest risk is running into Rick Astley.
A week ago, I wrote about Google starting to offer ".zip" domains and the possible risks associated with this [1]. Earlier today, I quickly surveyed registered .zip domains to see what people are doing with them.
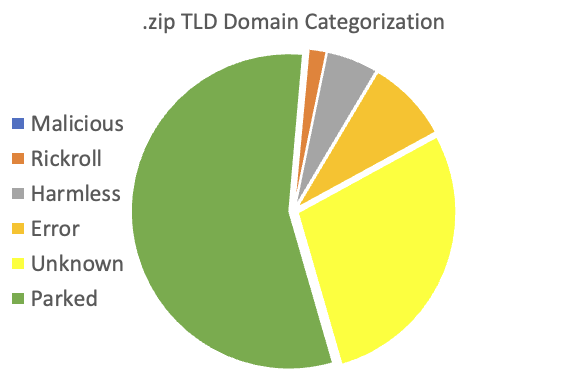
I found a total of 2,753 domains with content. Out of these files, I was able to categorize 1,928. The remaining is still a work in progress.
So far, most domains are "Parked" (1,506). This is typical for new domains displaying a registrar default page until the owner configures content. 229 of the domains are showing various errors. I classified 143 domains as harmless, meaning they link to different other pages that, as far as I can tell, do not provide malicious content. Some "harmless" sites appear registered by security companies or individuals either directing to their page or displaying messages warning about the .zip TLD issues. A few of the pages do, for example, direct to individual LinkedIn profiles.
48 domains direct to Rick Astley ("rickrolling") content or similar videos mostly meant to annoy visitors.
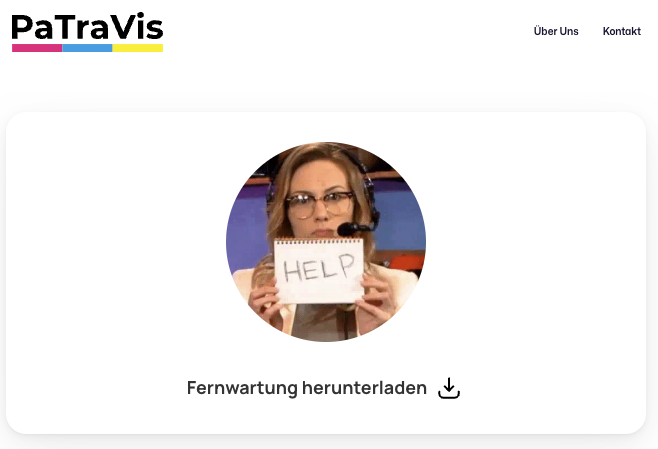
So far, I only found one domain that I consider "suspect": fermwartung[.]zip ("Fernwartung" is the German word for Remote Maintenance). It directs to what looks like a legitimate company's webpage, but the download triggers some suspicious signatures on Virustotal [2]. I am unfamiliar with the company, but according to the web page, they appear to be an IT service provider. It is possible that their remote assistance tool triggers some Anti-Virus warnings.
sentineloneinstaller[.]zip appeared to be advertising Norton Anti-Virus. Currently, the website is down, so I cannot verify if it attempted to play the "fake anti-virus" game.
This is still a work in progress, and I will update this story as I can classify more domains. The classification is based on keywords, so I will surely miss something. Let me know if you find an "interesting" (malicious) .zip domain.
A couple of sites offered online compression/decompression of zip files. There is an obvious risk here that, first of all, the file's content may be leaked, and secondly, the file you get back may be altered. But this is not specific to the ".zip" TLD, and I classified these sites as "harmless" for now.
One site displayed a login form. But I suspect this was just a login form for the site's admin interface. It did not resemble a brand I recognized and only asked for a password, not a username.
[1] https://isc.sans.edu/diary/The+zip+gTLD+Risks+and+Opportunities/29838/
[2] https://www.virustotal.com/gui/file/06298771950708c66951149af0962079c260e08d9eb536a17d9c5f54c0d888a7
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|


Comments