Detecting VSTO Office Files With ExifTool
VSTO Office files can be detected with ExifTool:
This was discovered by @ochsenmeier.
VSTO Office files are Office documents that are linked to a Visual Studio Office File application. That application is written with .NET, and can contain arbitrary code.
This feature can be used for malicious purposes, just like VBA. VSTO Office files do not contain VBA code (although they can), but they contain references and metadata to launch the VSTO file (a .NET application) when they are opened. And it is possible to host the VSTO files and accompanying files on a web server.
Referencing a VSTO file is done with 2 user defined properties: _AssemblyLocation and _AssemblyName. These properties can be extracted with zipdump.py for OOXML files and with oledump.py for OLE files.
Or with ExifTool.
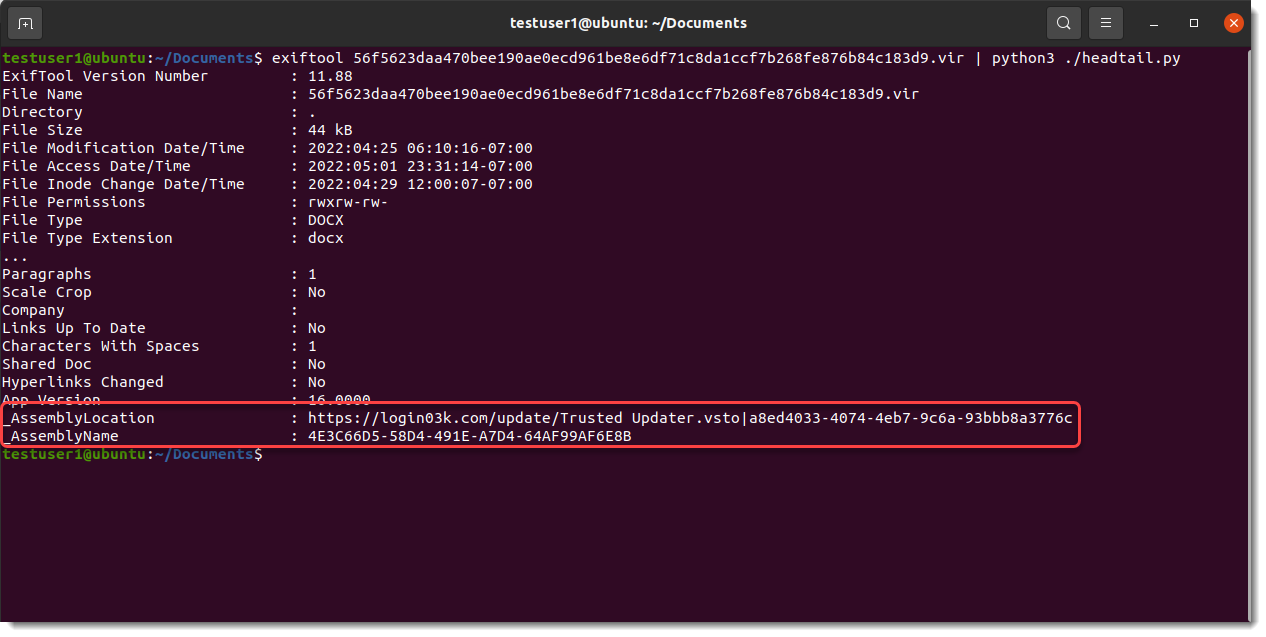
For OOXML files, ExifTool displays the actual names of these user defined properties:

While for ole files, ExifTool uses "Tag Assembly Location" and "Tag Assembly Name":
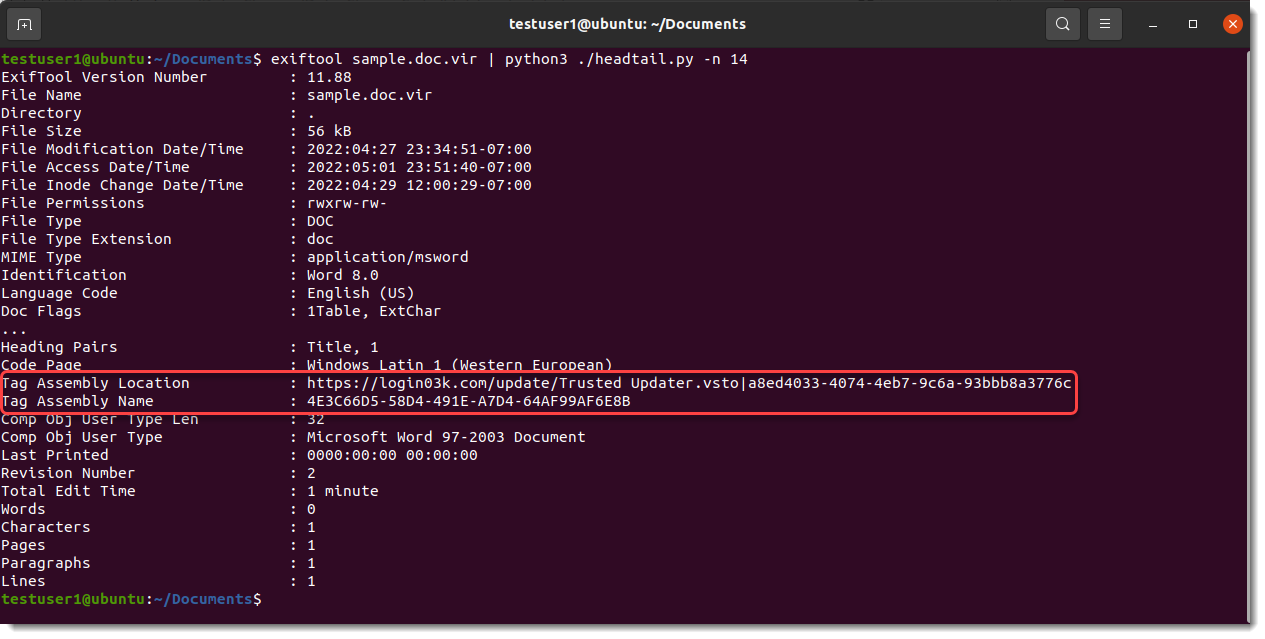
When the VSTO file is downloaded from the Internet, the user defined property _AssemblyLocation will be a URL.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com


Comments