A Survey of Bluetooth Vulnerabilities Trends
As usage of fitness trackers, wireless headsets and smart home devices become increasingly popular in our daily lives, a growing reliance on the Bluetooth protocol is expected as it serves as the main medium of communication between devices. Amidst the COVID-19 pandemic, Bluetooth-enabled devices such as phones and hardware tokens were also used for contact-tracing purposes in countries such as Singapore [1]. Currently, the core specification of Bluetooth is 5.2 [2], and are generally divided into 2 categories – Bluetooth Low Energy (BLE) and Bluetooth Classic [3]. Given the increasing popularity and usage of Bluetooth, I started to wonder about the trend of Bluetooth related vulnerabilities.
I turned to the CVE List and searched for Bluetooth related vulnerabilities. At the point of writing, there was a total of 445 publicly listed vulnerabilities related to Bluetooth [4]. Based on the returned vulnerabilities and with reference to Figure 1, I plotted a simple graph to look at the trend. Do note that for the year 2021, the data is only partial as the year of 2021 has not ended yet. In addition, there could also be a possibility that certain CVE IDs have not been publicly disclosed, or that Bluetooth-related vulnerabilities were not submitted to the CVE List.
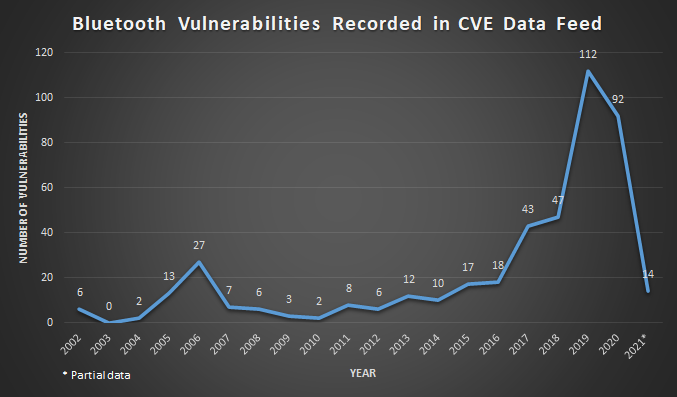
Figure 1: Bluetooth Vulnerabilities from Year 2002 to 2021
It was interesting to note that the formal specification of Bluetooth 1.0 was first released in 1999 [5], and the first Bluetooth related vulnerability was recorded in the CVE database in the year 2002. Having said that, the Bluetooth “vulnerabilities” for the year 2002 were actually web application related. However, as I wanted to collate all vulnerability data that were related (even if it was indirect) to Bluetooth, I have kept it there. The actual vulnerabilities with Bluetooth protocol started in the year 2004 (CVE-2004-0143), and the device affected was a Nokia 6310i mobile phone [4]. Vulnerabilities associated with Bluetooth had a short spike up in 2006, and remained relatively stable until 2017 where a spike in vulnerabilities occurred. Finally, the highest number of Bluetooth related vulnerabilities found was in the year 2019 across a wide spectrum of devices (Samsung, Texas Instruments, Xiaomi, Cypress PSoC, and even vaping kits) and software (Android, Nulock).
Recent research in Bluetooth Low Energy (BLE) implementations of various vendors have shown that the BLE stacks were vulnerable to some fundamental attacks. The SweynTooth family of vulnerabilities showed that many implementation details specified by the Bluetooth Core Specification were not adhered to by the System-on-Chip (SoC) vendors [6], and this also further affected multiple products that relied on those SoC running vulnerable implementations of BLE [6]. Patching the devices can also prove to be a complicated issue as product vendors have to contact the respective SoC vendor for the security patches.
This does not mean that the usage of Bluetooth devices is discouraged. However, users should start to be more discerning and consider checking whether the Bluetooth devices currently in use are affected by any security issues. Moreover, users should also check if the devices will be actively supported by the manufacturers in terms of security patches and/or firmware updates to fix any potential vulnerabilities discovered by researchers in future. From a corporate organization’s perspective, it might also be worthwhile to consider having a policy/directive and brief audit on usage of Bluetooth devices (For example, are vulnerable Bluetooth devices being used? Are there any current risks/vulnerabilities in Bluetooth devices used by employees?). Looking at the data trend of Bluetooth vulnerabilities submitted to CVE List and a multitude of published papers with respect to Bluetooth vulnerabilities in peer-reviewed journals and conferences, it is likely that Bluetooth will be scrutinized further in the months and years to come (and hopefully, a more secure Bluetooth ecosystem for all).
References:
[1] https://support.tracetogether.gov.sg/hc/en-sg/articles/360053530773-What-is-the-TraceTogether-Programme-
[2] https://www.bluetooth.com/wp-content/uploads/2020/01/Bluetooth_5.2_Feature_Overview.pdf
[3] https://www.bluetooth.com/learn-about-bluetooth/radio-versions/
[4] https://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=bluetooth
[5] https://web.archive.org/web/20180525083558/https://www.bluetooth.com/about-us/our-history
[6] https://asset-group.github.io/disclosures/sweyntooth/
-----------
Yee Ching Tok, ISC Handler
Personal Site
Twitter


Comments