Diving into a Singapore Post Phishing E-mail
With the sustained persistence of COVID-19 globally, postal and e-commerce related phishing e-mails remain as one of the most widely favoured methods by adversaries and cybercrime groups. Although postal and shipping companies have often put-up warnings with respect to phishing sites and e-mails (for example Singapore Post [1] and DHL [2]), phishing sites and e-mails continue to be propagated. While organizations continue to deploy technologies and invest in security awareness training to allow better detection of phishing e-mails, individuals who are not particularly IT-savvy could fall prey to such phishing e-mails, especially with respect to their personal e-mail accounts who may not have enterprise phishing protection features. I was recently forwarded one phishing e-mail for a quick look. Unfortunately, by the time I got to it, the phishing page appeared to have been taken down. However, there were some salient points that struck me when I analyzed the contents of the e-mail, and wanted to talk a bit about it so as to increase awareness.
A check on the e-mail headers yielded the following information (with reference to Figure 1, and some details were omitted to preserve privacy):
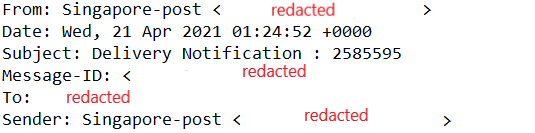
Figure 1: E-Mail Headers
I did some research on the e-mail address in the “From” and “Sender” fields, and discovered that it originated from a legitimate company (hence the redaction). Of course, the name reflected in the “From” and “Sender” fields should have triggered some red flags since it stated “Singapore-post” but displayed another e-mail address.
Moving on to the contents of the e-mail. With reference to Figure 2 below, we can see the contents (some information have been removed to preserve privacy).
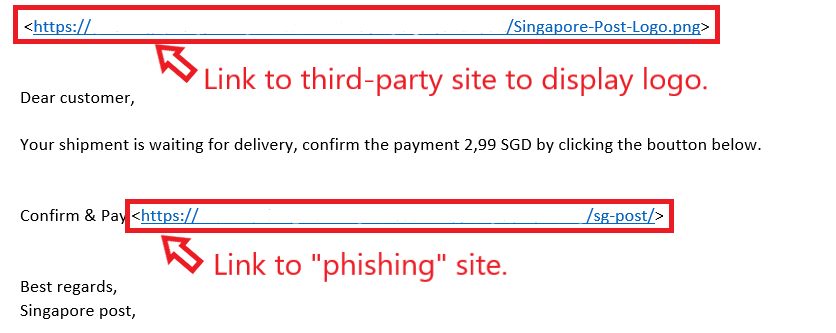
Figure 2: Contents of Phishing E-Mail
The first thing that drew my attention was the logo that was retrieved from a third-party site which felt particularly dodgy. After visiting the “phishing” site, a webpage related to the original site loaded with no signs of any content related to Singapore Post (thankfully!). While it appeared that the owner of the website removed phishing content and replaced with something of their own, the link was still kept.
Looking at all the factors, there were many opportunities to deny the adversaries from succeeding in sending out the phishing e-mail. The factors that could be addressed are as follows:
1. Image Hotlinking: This is a common issue faced by many individuals and organizations hosting their websites. If left unchecked, it could affect the uptime and bandwidth costs (this is especially so for small businesses that often cannot afford high-capacity web hosting plans). In this case, we can see that the third-party website inadvertently facilitated the adversaries’ attempts in providing the logo for their phishing e-mails. To mitigate this issue, one can consider using Content Delivery Networks (CDN) that have hotlink protection features, or tweak cPanel settings (if it is used to administer your website) as shown here [3]. There are also a few other methods, but configuration will vary due to the type of CMS that the website is running on. Nevertheless, there are some robust documentations available online with respect to image hotlinking, and owners should consider implementing them if possible.
2. Securing assets: A legitimate organization’s e-mail system was compromised to send out the phishing e-mail, and another legitimate organization’s website was used to host the phishing page. I did not probe into the affected organizations’ assets, but such compromises are usually due to unpatched systems, security misconfiguration or a successful phish of administrative credentials. Unfortunately, other than taking a proactive approach towards cybersecurity within limits of a given budget, there isn’t really much an organization can do (ignoring the issue can be one way, but that is bound to bring more disastrous and pressing issues to the organization/business in future). Building and maintaining security controls can be challenging, but there is useful documentation such as the CIS Controls (version 8 launching soon [4]) that organizations could refer to bolster their cybersecurity readiness.
As always, when in doubt, verify the authenticity of the e-mail received. In addition, why not consider checking in with your loved ones and friends to see if they received any phishing e-mails and let them know how they could spot potential ones? These are no doubt challenging times, and being able to maintain access to your digital accounts should be one of the top priorities.
References:
[1] https://www.singpost.com/online-security-you
[2] https://www.dhl.com/sg-en/home/footer/fraud-awareness.html
[3] https://documentation.cpanel.net/display/84Docs/Hotlink+Protection
[4] https://www.sans.org/blog/cis-controls-v8/
-----------
Yee Ching Tok, ISC Handler
Personal Site
Twitter


Comments