Do Vulnerabilities Ever Get Old? Recent "Mirai" Variant Scanning for 20 Year Old Amanda Version?
We always say how network security is changing every day. Take a long lunch, and you may miss a critical exploit. But sometimes, time appears to stand still. We just passed 1.6 Billion seconds in the Unix Epoch. Back when the Unix timestamp still had 9 digits, in the late 90s also known as "pre Y2K", one of the servers you may have used for backups was Amanda (Advanced Maryland Automatic Network Disk Archiver). Still active and alive today, back then Amanda V 2.3 was current.
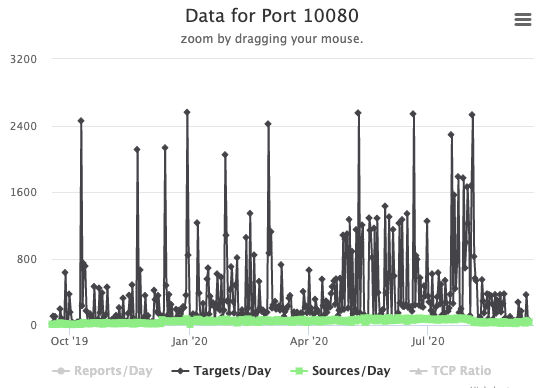
Amanda typically listens on port port 10080, and while port 10080 is scanned, we see not a lot of scans for that port. Shodan also comes up with "not much" for port 10080.
So I was a bit surprised to see these strings in a recent Mirai type bot I captured:
Amanda 2.3 REQ HANDLE 000-65637373 SEQ 954568800
SERVICE amanda
This particular string is used by Nessus since July 14th 2000 (maybe longer). The version "2.3" is a bit misleading here. This is a request that is typically sent to the Amanda client (not server). Nessus uses this request to detect the client's version. So this may as well look for more recent Amanda client versions.
So is it looking for a 20-year-old version? Possibly not. Why is it looking for backup clients? There are many possibilities:
- Data exfiltration: Unusual for Mirai bots, but this version appears to be "work in progress". Someone may be trying to use this to scan for internal Amanda clients once a network is breached.
- Ransomware: Ransomware doesn't like backups. Again not typical for Mirai, but a simple "delete all files, including backups" is certainly in scope and some Mirai variants like "Bricker Bot" did show destructive behavior.
I am still trying to trigger the Amanda scan behavior. So far, I had no luck with it and all the bot did so far is scan for port 23 (this is why I call it "Mirai"). It also connects to a C2 server at 45.145.185.94. This IP address is hardcoded and no DNS lookup is performed.
Virustotal: https://www.virustotal.com/gui/file/24f597ad10f4c2be2c27356adde514c59f05a524737f6a7c8461627bbb9b1e5c/detection
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|


Comments