Merry christmas!
by Manuel Humberto Santander Pelaez (Version: 1)
We wish you and your families a merry christmas!
Manuel Humberto Santander Pelaez
SANS Internet Storm Center - Handler
Twitter:@manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org
Timely acquisition of network traffic evidence in the middle of an incident response procedure
by Manuel Humberto Santander Pelaez (Version: 1)
The acquisition of evidence is one of the procedures that always brings controversy in incident management. We must answer questions such as:
- Do we have all the elements required to execute the acquisition of evidence?
- What happens if the evidence is volatile and I don't have the software I need to capture it in accordance with the established procedure?
In the case of network evidence, it is clear that uncaptured traffic is lost forever. Therefore, the opportunity to capture evidence is essential to be able to have the greatest amount of information to determine elements such as indicators of commitment or tactics, techniques and procedures used by the attackers.
Imagine this situation: You are reviewing a computer that is allegedly compromised and apparently the intruder is still inside. The internet went down and you cannot install a sniffer. How can you proceed to capture the evidence quickly?
The quickest solution is to use the network trace capability built inside windows. This feature uses the NDIS driver to capture packets. Let's use powershell to perform the operations:
- Let's start a capture session named Example of Network trace, saving it into a file named as the local computername.etl and with a maximum size of 5 MB:
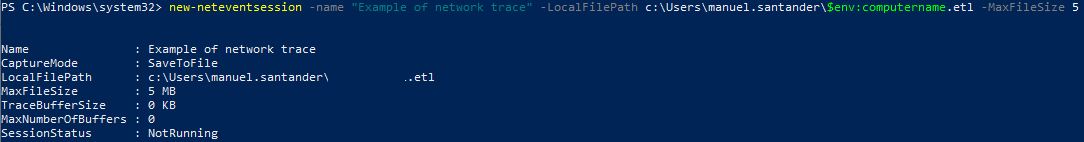
- Now we assign the packet capture provider to the session:
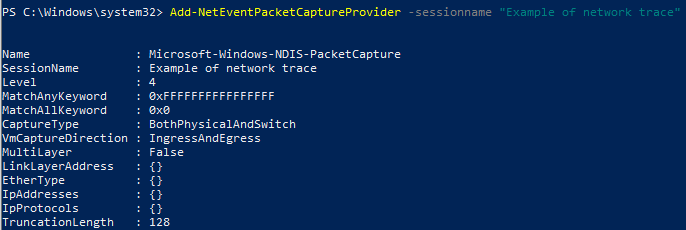
- Now we start the network capture and query the status of it:
.png)
- When finished, we stop the capture:

We can see the capture using Microsoft Message Analyzer, which is currently deprecated and no longer available through the Microsoft Website. If you still want to download it, you can use wayback machine and the following link: https://web.archive.org/web/20191104120853/https://www.microsoft.com/en-us/download/confirmation.aspx?id=44226
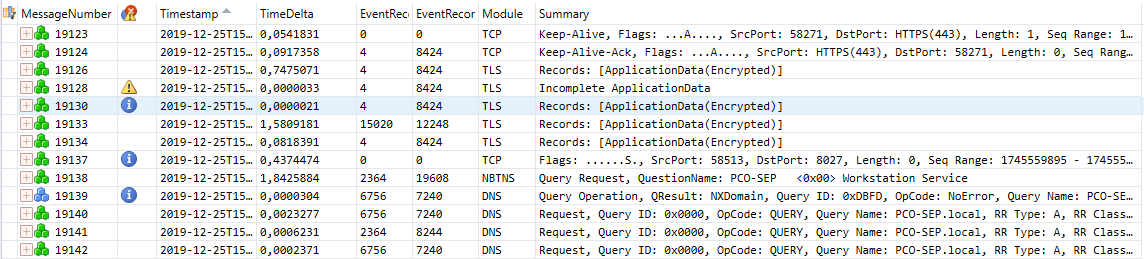
If you need to manipulate it in wireshark, you can export it to Microsoft Network Monitor (cap) format using the save as feature:
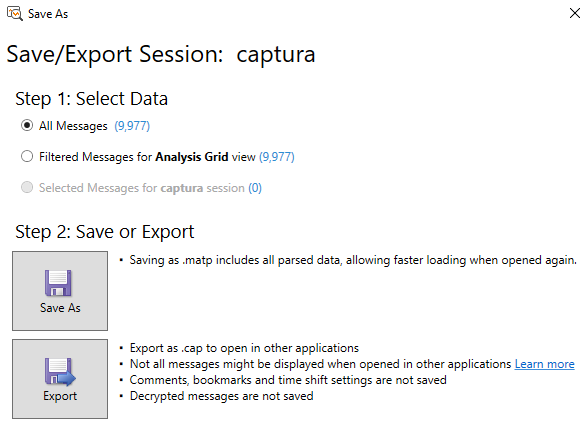
After that, you can open the cap file using wireshark:
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter:@manuelsantander
Web:http://manuel.santander.name
e-mail:msantand at isc dot sans dot org


Comments