Emotet infection with spambot activity
Introduction
On Monday 2019-12-16, I tested some Emotet samples. I normally get Trickbot as the follow-up malware, which I've already documented from Monday. But every once in a while, I'll see spambot traffic instead of (or in addition to) Trickbot.
When I tested another Emotet sample later that day, I saw spambot traffic. Today's diary reviews information from that infection.
The email
On Monday afternoon (Unite States Central time), I saw an Emotet malspam message that made it to my inbox.
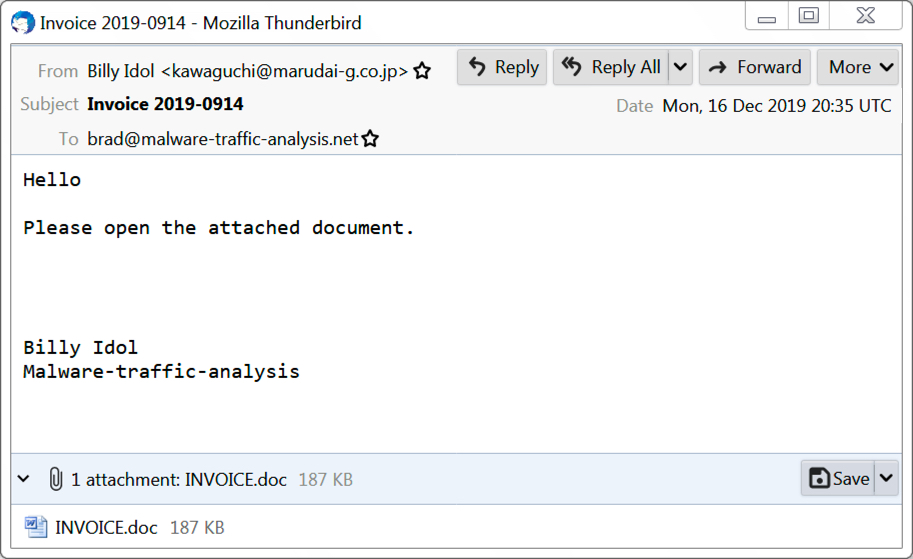
Shown above: Emotet malspam that made it to my inbox.
Why is the sender named Billy Idol? Because that was a name in the address book from one of my Emotet-infected Windows hosts a few months back. I generally make up names as I spin up vulnerable hosts in my lab. At some point, I vaguely remember using "Billy Idol" as a name when I'd set up a fake email account and generated some items for the inbox of a lab host.
That doesn't mean "Billy Idol" was infected. It just means an Emotet-infected host had an email in the inbox (or sent items) with an address using that name as an alias.
The email had an attached Word document, which I tested in my lab.
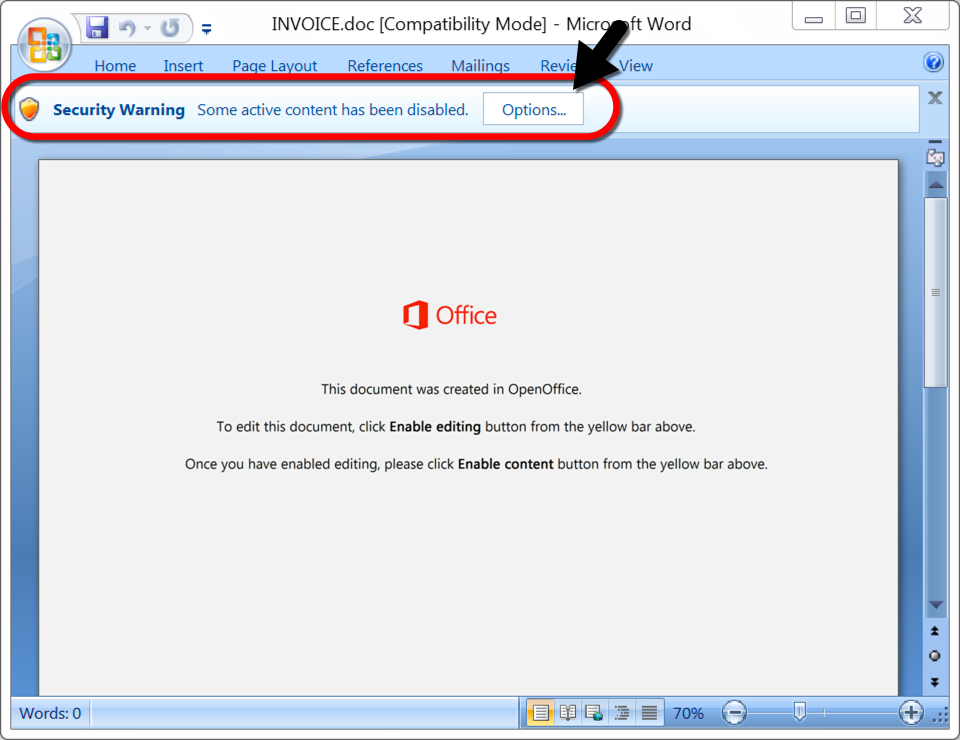
Shown above: Word doc from the email with macro for Emotet.
The infected Window host
My infected host had a Windows executable for Emotet made persistent through the Windows registry as shown below. This is normal behavior for Emotet.
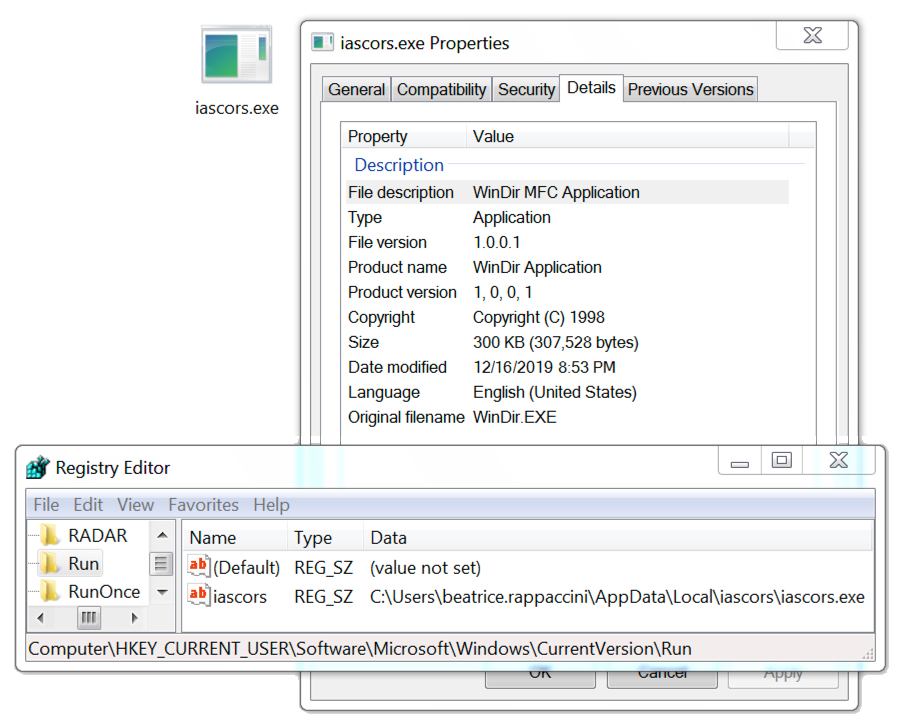
Shown above: Emotet persistent on an infected Windows host.
Infection traffic
The traffic patterns were typical for Emotet. However, if an Emotet-infected Windows client turns into a spambot, it will generate SMTP and encrypted SMTP traffic. The spambot traffic is mostly encrypted SMTP--in fact, most often all of it is encrypted. But sometimes you might find unencrypted SMTP when reviewing the traffic in Wireshark as shown below. You can also use Wireshark to export emails found in unencrypted SMTP traffic from the pcap.
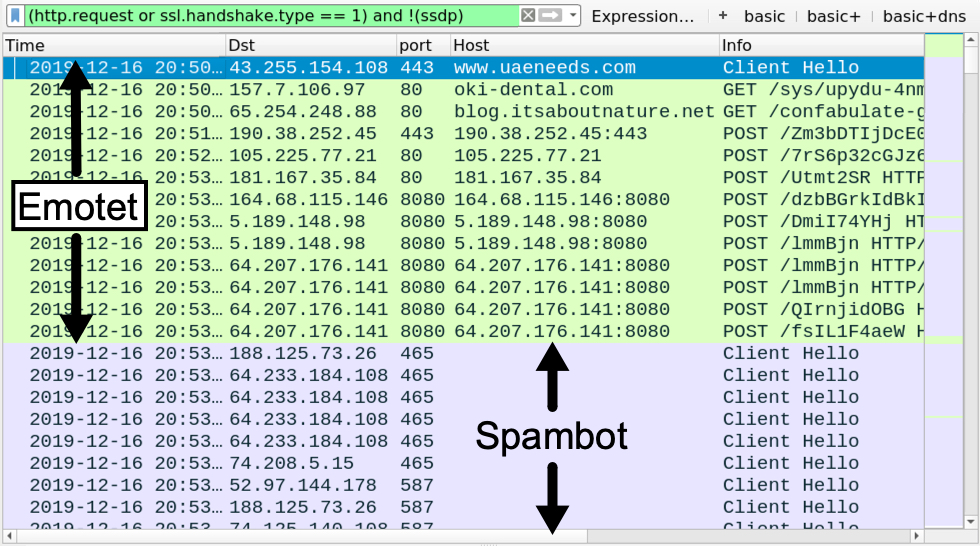
Shown above: Filtering on web traffic in Wireshark shows SSL/TLS spambot traffic to mailservers, mostly over TCP ports 25, 465, and 587.
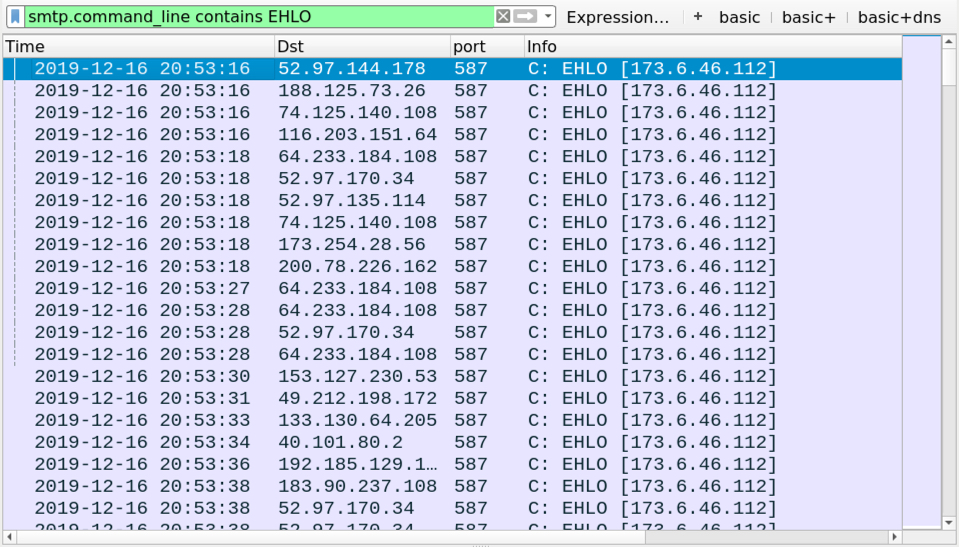
Shown above: You can filter on various SMTP commands (like EHLO) to get a better idea of the encrypted/unencrypted spambot traffic.
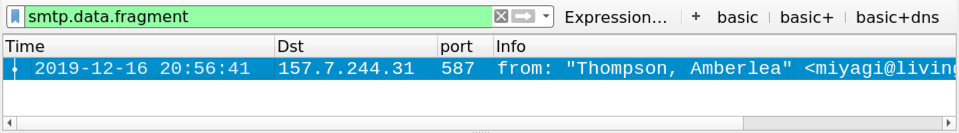
Shown above: You can filter on smtp.data.fragment to find any emails in the pcap from unencrypted SMTP.

Shown above: Using Wireshark to export emails from unencrypted email traffic in a pcap.

Shown above: Traffic from my infected lab host only had one email I could export from the pcap.

Shown above: The exported email file opened in a text editor.
Indicators of Compromise (IoCs)
Malware from an infected Windows host:
SHA256 hash: b82542fa69e2a8936972242c0d2d5049235b6b0d24030073a886937f1f179680
- File size: 191,744 bytes
- File name: INVOICE.doc
- File description: Malspam attachment--Word doc with macro for Emotet
SHA256 hash: 8bfb28788bd813e2ec3e7dc0cce9c95bda8d5df89a65b911c539e0a6aebcfc05
- File size: 307,528 bytes
- File location: hxxp://blog.itsaboutnature[.]net/confabulate-grainy/tad0m4bjt-li6lr-5546823/
- File location: C:\Users\[username]\26.exe
- File location: C:\Users\[username]\AppData\local\iascors\iascors.exe
- File description: Emotet malware binary retrieved by Word macro
Traffic caused by Word macro to retrieve an Emotet EXE file:
- 104.27.149[.]107 port 80 - www.simple-it[.]org - attempted TCP connections but no response from the server
- 43.255.154[.]108 port 443 - www.uaeneeds[.]com - HTTPS/SSL/TLS traffic
- 157.7.106[.]97 port 80 - oki-dental[.]com - GET /sys/upydu-4nmmykhbf-292/
- 65.254.248[.]88 port 80 - blog.itsaboutnature[.]net - GET /confabulate-grainy/tad0m4bjt-li6lr-5546823/
Emotet post-infection HTTP traffic:
- 190.38.252[.]45 port 443 - 190.38.252[.]45:443 - POST /Zm3bDTIjDcE0VBqqFO
- 105.225.77[.]21 port 80 - 105.225.77[.]21 - POST /7rS6p32cGJz6yHNBUKW
- 181.167.35[.]84 port 80 - 181.167.35[.]84 - POST /Utmt2SR
- 164.68.115[.]146 port 8080 - 164.68.115[.]146:8080 - POST /dzbBGrkIdBkIqwPjf
- 5.189.148[.]98 port 8080 - 5.189.148[.]98:8080 - POST /DmiI74YHj
- 5.189.148[.]98 port 8080 - 5.189.148[.]98:8080 - POST /lmmBjn
- 64.207.176[.]141 port 8080 - 64.207.176[.]141:8080 - POST /lmmBjn
- 64.207.176[.]141 port 8080 - 64.207.176[.]141:8080 - POST /QIrnjidOBG
- 64.207.176[.]141 port 8080 - 64.207.176[.]141:8080 - POST /fsIL1F4aeW
- 64.207.176[.]141 port 8080 - 64.207.176[.]141:8080 - POST /Qb6Hb0ONYVQ2an
- 64.207.176[.]141 port 8080 - 64.207.176[.]141:8080 - POST /Cux8Ia00axEqkIhB2
- 64.207.176[.]141 port 8080 - 64.207.176[.]141:8080 - POST /lqcZ9GHhKIkoVPdb
- 64.207.176[.]141 port 8080 - 64.207.176[.]141:8080 - POST /xaMc6JN
- 64.207.176[.]141 port 8080 - 64.207.176[.]141:8080 - POST /VJ9ZrKRKSWYOwNrPCk
- 82.145.43[.]153 port 8080 - 82.145.43[.]153:8080 - POST /PKgFIQr2tR
- 149.202.153[.]251 port 8080 - 149.202.153[.]251:8080 - POST /iEo555d
- 149.202.153[.]251 port 8080 - 149.202.153[.]251:8080 - POST /1SxH7
Spambot traffic:
- Various IP addresses over various TCP ports - SMTP and encrypted SMTP traffic
Final words
A malspam example, a pcap of the infection traffic, and the associated malware can be found here.
--
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments