Retrieving malware over Tor
A couple of years ago, Lenny Zeltser wrote a diary entry on how to use curl to retrieve malware samples.
If you don't want to disclose your public IP address when retrieving malware, you can use proxies. One way to do this, is to use the Tor anonimity network.
On Linux and OSX, it's quite easy to do so.
You install the tor and torsocks packages for your distro, start tor, and then launch your curl or wget command via torsocks.
torsocks curl http://www.example.com/page -D headers.txt -o sample.vir
Mind you, the Tor network can be slow or unstable sometimes, which may interfere with the sample download. And Tor nodes might also be blocked in countries where you want to download samples from.
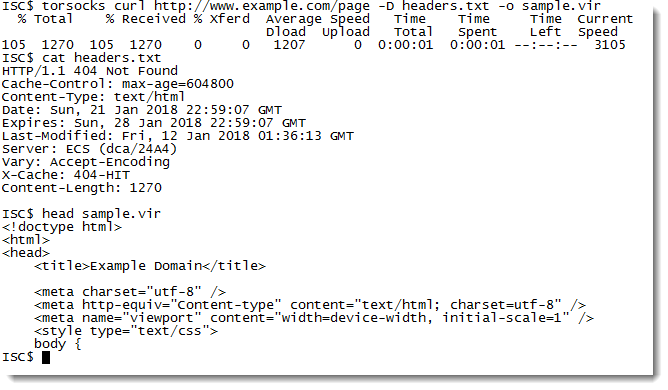
On Windows, you can use Tor but not torsocks.
For curl, that's not a problem. You just instruct curl to use the Tor socks proxy with option --socks5-hostname:
curl --socks5-hostname localhost:9050 http://www.example.com/page -D headers.txt -o sample.vir
For wget, it's a bit more complex, because wget can't talk to Socks directly. wget can talk to a HTTP/HTTPS proxy, so you can setup such a proxy between Tor and wget.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com


Comments