Resume-themed malspam pushing Smoke Loader
Introduction
Malicious spam (malspam) with malware disguised as a resume. This is a long-running theme frequently used by criminals to push various types of malware.
My Online Security reported about a recent wave earlier this month on 2017-11-10. These resume-themed emails contain Word documents with malicious macros, and the macros are designed to infect your Windows computer. Recent macros associated with this campaign have used 89.248.169[.]136/bigmac.jpg to retrieve malware used to infect a victim's computer. When I checked, that URL returned a Windows executable file, and it has hosted different types malware since it was first reported back in October 2017.
Emails from this most recent wave of malspam have been submitted to VirusTotal as recently as Saturday 2017-11-18. I collected some of these messages and generated an infection in my lab. Today's diary reviews recent emails from this wave of malspam, and it examines the associated infection traffic.
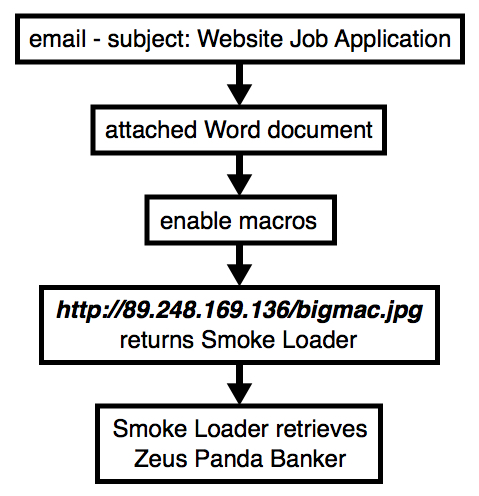
Shown above: Flow chart for the infection traffic.
What's the malware this time?
Last month on 2017-10-08, My Online Security reported Word documents from this malspam were pushing GlobeImposter ransomware. However, on 2017-11-18, Word documents from this malspam were pushing Smoke Loader (sometimes spelled as single word: SmokeLoader). Smoke Loader is a malware downloader, and it's also known as Sharik or Dofoil.
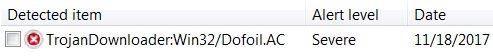
Shown above: Smoke Loader sample identified as Dofoil by Microsoft.
I've seen different malware downloaded by Smoke Loader, but during Saturday's 2017-11-18 infection, the follow-up malware was Zeus Panda Banker.
The emails
Send dates show as Wednesday 2017-11-15 or Thursday 2017-11-16, but emails from this malspam were received through Saturday 2017-11-18. Each email had a similar message body, but with random names for the sender and email attachments. All emails from this malspam had the same subject line: Website Job Application.
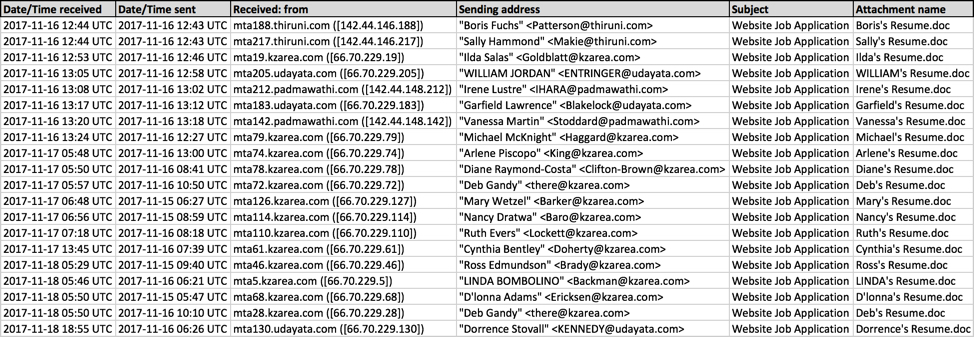
Shown above: Screenshot from a spreadsheet tracker.
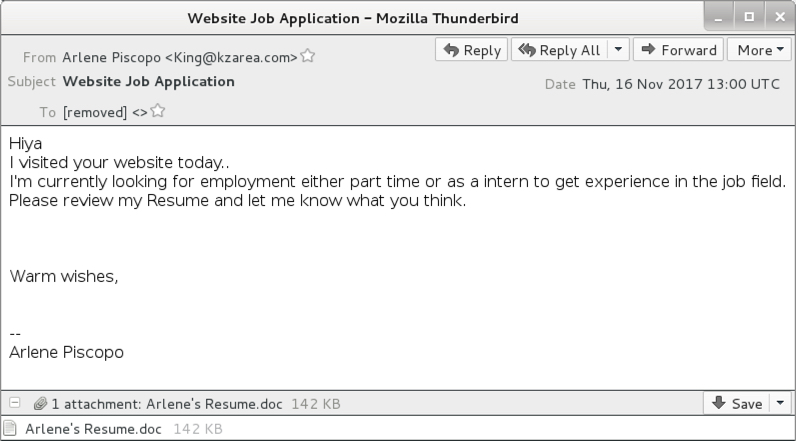
Shown above: Screenshot from one of the emails.
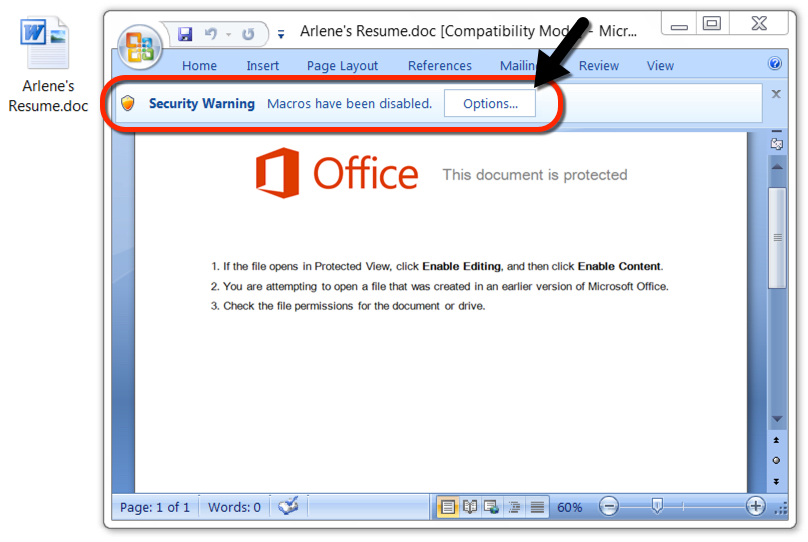
Shown above: Attachment from one of the emails.
The traffic
The Smoke Loader sample didn't run on a virtual machine (VM), and it didn't do anything when submitted to publicly available sandboxes like www.reverse.it. I had to generate infection traffic on a physical Windows host.
From a physical host in my lab, the Word document macro downloaded Smoke Loader, and Smoke Loader downloaded Zeus Panda Banker. Network traffic and the associated alerts confirmed this activity.
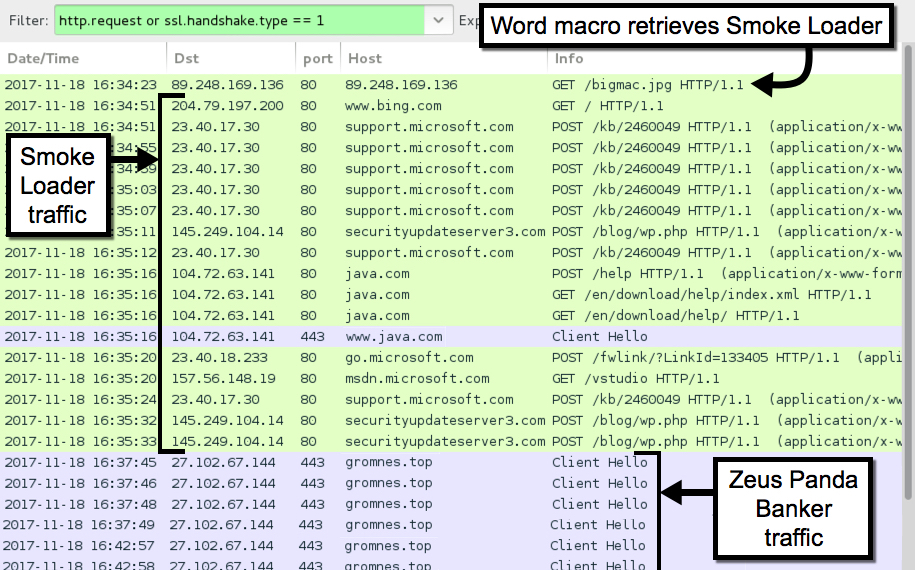
Shown above: Traffic from an infection filtered in Wireshark.

Shown above: Alerts from the traffic in Sguil on Security Onion using Suricata and the EmergingThreats Pro ruleset.
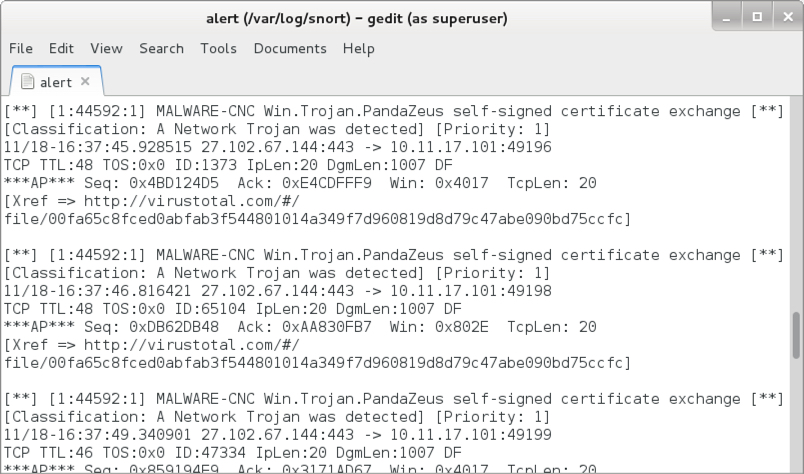
Shown above: Post-infection alerts for Zeus Panda Banker using Snort 2.9.11 and the Snort Subscription ruleset.
Indicators
The following traffic to legitimate domains was generated by Smoke Loader:
- www.bing.com - GET /
- support.microsoft.com - POST /kb/2460049
- java.com - POST /help
- java.com - GET /en/download/help/index.xml
- java.com - GET /en/download/help/
- go.microsoft.com - POST /fwlink/?LinkId=133405
- msdn.microsoft.com - GET /vstudio
The following traffic to malicious domains was noted during the infection.
Word macro downloading Smoke Loader:
- 89.248.169[.]136 port 80 - 89.248.169[.]136 - GET /bigmac.jpg
Smoke Loader traffic for check-in and downloading follow-up malware:
- 145.249.104[.]14 port 80 - securityupdateserver3[.]com - POST /blog/wp.php
HTTPS/SSL/TLS traffic caused by Zeus Panda Banker:
- 27.102.67[.]144 port 443 - gromnes[.]top
The following file hashes were noted for Word documents from this malspam:
- f697fc7a32389318a674207c62eccafe89442efd93b202500e83ad428f64a2be - Arlene's Resume.doc
- 9782eb60b45b531fe03e7024a2b96e9df9a3e3fa62a5cf71553f2d4973ecfbab - Boris's Resume.doc
- 1f95594b0023d215c49be99f79a39fab6d5696bed56cb7cb59bb50dfc52ccf71 - Cynthia's Resume.doc
- 630b17eafbfc5947a4018dec53ef6f1aac305d84c350f7e493c4b74a60352737 - D'lonna's Resume.doc
- 1137df638b156a6ed5c05c39398db7c8e465c7edf815084862c1774be41c942e - Deb's Resume.doc
- 2533bb19f3ab496bf5494e2d490649121e368b3c4b63590e0156680d2903237c - Deb's Resume.doc
- bc849b0817f56e124b6e619d10cf998f0e0e5fa03ed5f13fc91e6a47df003b4c - Diane's Resume.doc
- 71b806ce67bda6d50936b1238f2953f7765aa8d9158e6602a2a313b0f62af4ef - Dorrence's Resume.doc
- 466a40786278f93d7b882a84e495735c80408d53e033e2a273e0ee5b1e915eca - Garfield's Resume.doc
- a5f311940da7390d3035ed88b59e31d75ce877e9aa66943c77f8c3a341582981 - Ilda's Resume.doc
- 3d52d1be7f5bbc1eae53d382a71c4b9de40c834111cd58db2a7e79f9e04fd087 - Irene's Resume.doc
- 2930451c2d31ba89eba50d3e5aa0beef5725a1c1836bcb0b18f8acdf4b1161a8 - LINDA's Resume.doc
- 729b641fc9dd4cda4d7360fc392d310c43c679e5194520b808f3126f50f3b9c4 - Mary's Resume.doc
- 15de93edc87cbfda1ebd4e367f2a8c687b6f345042f3b9bff6e2380af36b19f9 - Michael's Resume.doc
- 22c351ad8953c9654ee3b8f8eaa8a5e7c7f6592543c7912bd6ba2867a63c143b - Nancy's Resume.doc
- b4db40ba1a10471ad0afa0fa65f1b9ab75c5051cde8b0233e3ecf17bb75e783d - Ross's Resume.doc
- 241a66f6989cf879fe2926c131afbb15c5607d76cd34784686b10459bfd4aaba - Ruth's Resume.doc
- 7887343bd47bab3b8c41cb92c29f8b83b1c2b22dd1a1c93042cc4893eb5a2181 - Sally's Resume.doc
- 162771bdd281b920080a5ab3812d1029a66bab422cc2563f697fd413db92fb2d - Vanessa's Resume.doc
- 4093f9410938608921116c79cc3abc21863a74498a8df8ee346096a313488c84 - WILLIAM's Resume.doc
The following file hash was noted for Smoke Loader from this infection:
- SHA256 hash: e8b306a0c742d34f976c7af1ee7a63fe65f2c2403fe5fc1eced82848f07fd1b3
- File size: 212,992 bytes
- File location: C:\Users\[username]\AppData\Roaming\Microsoft\vsuwdiba\gresctab.exe
The following file hash was noted for Zeus Panda Banker from this infection:
- SHA256 hash: 171aaf4d4960df961a1cb054355ce0d834053a7a7486f95dae05fdaa3a97b61a
- File size: 212,992 bytes
- File location: C:\Users\[username]\AppData\Roaming\[existing file path]\[random file name].exe
Final words
Malspam uses a variety of attachments and techniques to distribute malware. I've seen a lot of Word attachments from malspam in recent weeks, and malicious Office macros are a common method. However, these macros are fairly obvious, and educated users can easily avoid them. Additionally, system administrators and the technically inclined can implement best practices like Software Restriction Policies (SRP) or AppLocker to prevent these types of infections.
Email, malware, and traffic samples for today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments