Triaging suspicious files with pestudio
Triaging suspicious files with pestudio
Pestudio[1] by is a utility can be used to Triage malware analysis . all you need is to drop the suspicious file to Pestudio and it will show you the imports, the resources and it will send the MD5 hash of the file to virustotal.
Usage:
Pestudio can be obtained from https://winitor.com/download , there is no need for registration to download it.
Once you download Pestudio you have just to extract the file and use it.
If you are a command line fan you can just type the following:
|
pestudiox.exe |
And it will show you the options
|
pestudiox 8.61 - Malware Initial Assessment Copyright © 2009-2017 Marc Ochsenmeier www.winitor.com
pestudiox -file:input [-xml:output]
-file: input file to analyse -xml: output xml report file |
As you can see it’s straightforward to use the command line version of Pestudio ,you have just to specify the suspicious file and you have to specify the xml output file name.
Now let’s put Pestudio in action and try some sucepicious files. In this diary, I am going to use the GUI version.
For this diary I have obtain a sample malware from malware traffic analysis blog[2] which is maintained by Brad Duncan the ISC Handler.
To triage a file with Pestudio you have to run it then you can drop the suspicious file to it or you can choose open file from the file menu.
It will take few seconds to do it’s analysis . As you can see in the screenshot the first thing it will show some general info about the file such as the MD5 hash and entropy.
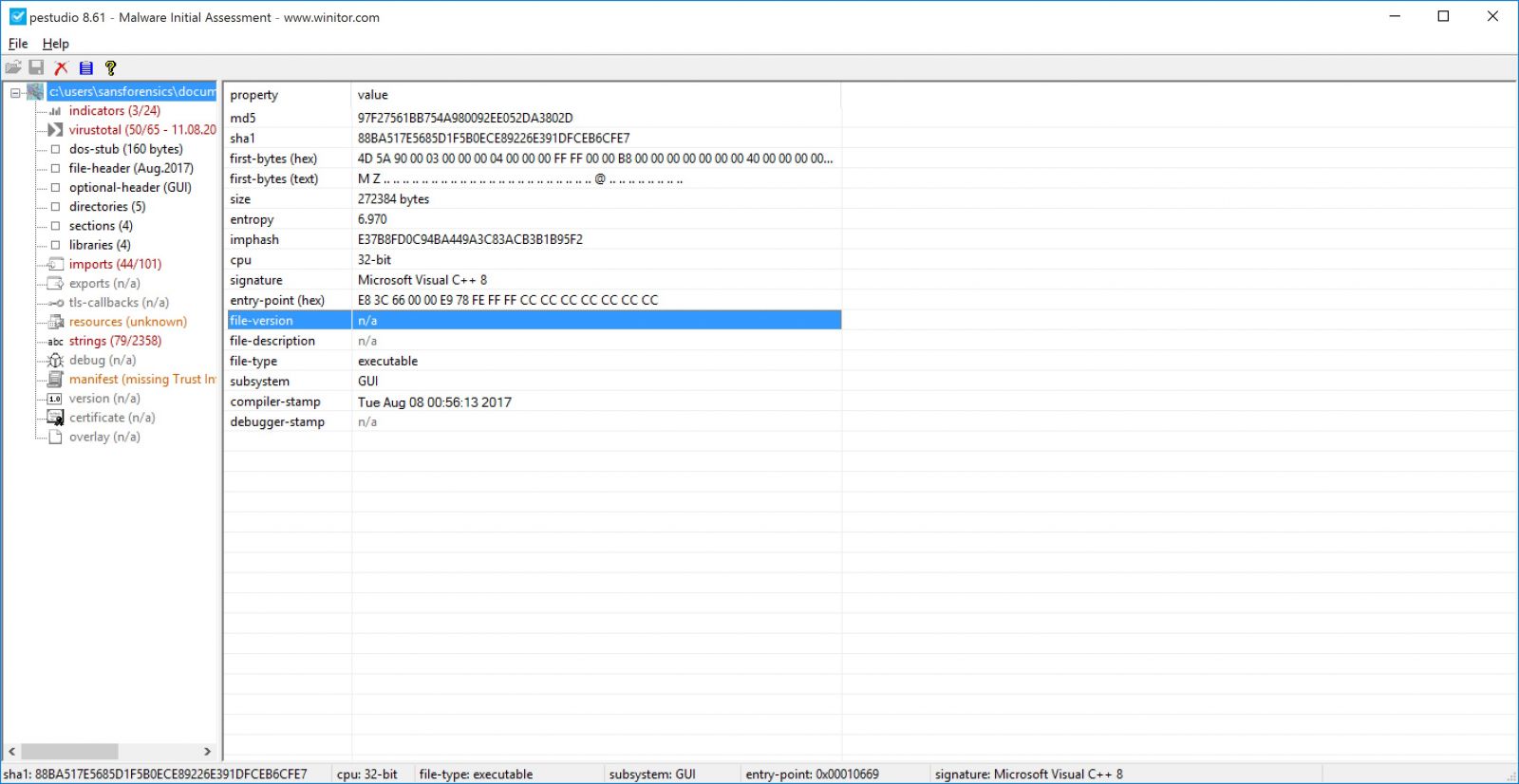
Then there will be the indicator window, here Pestudio will tell you why it thinks this file is suspicious.
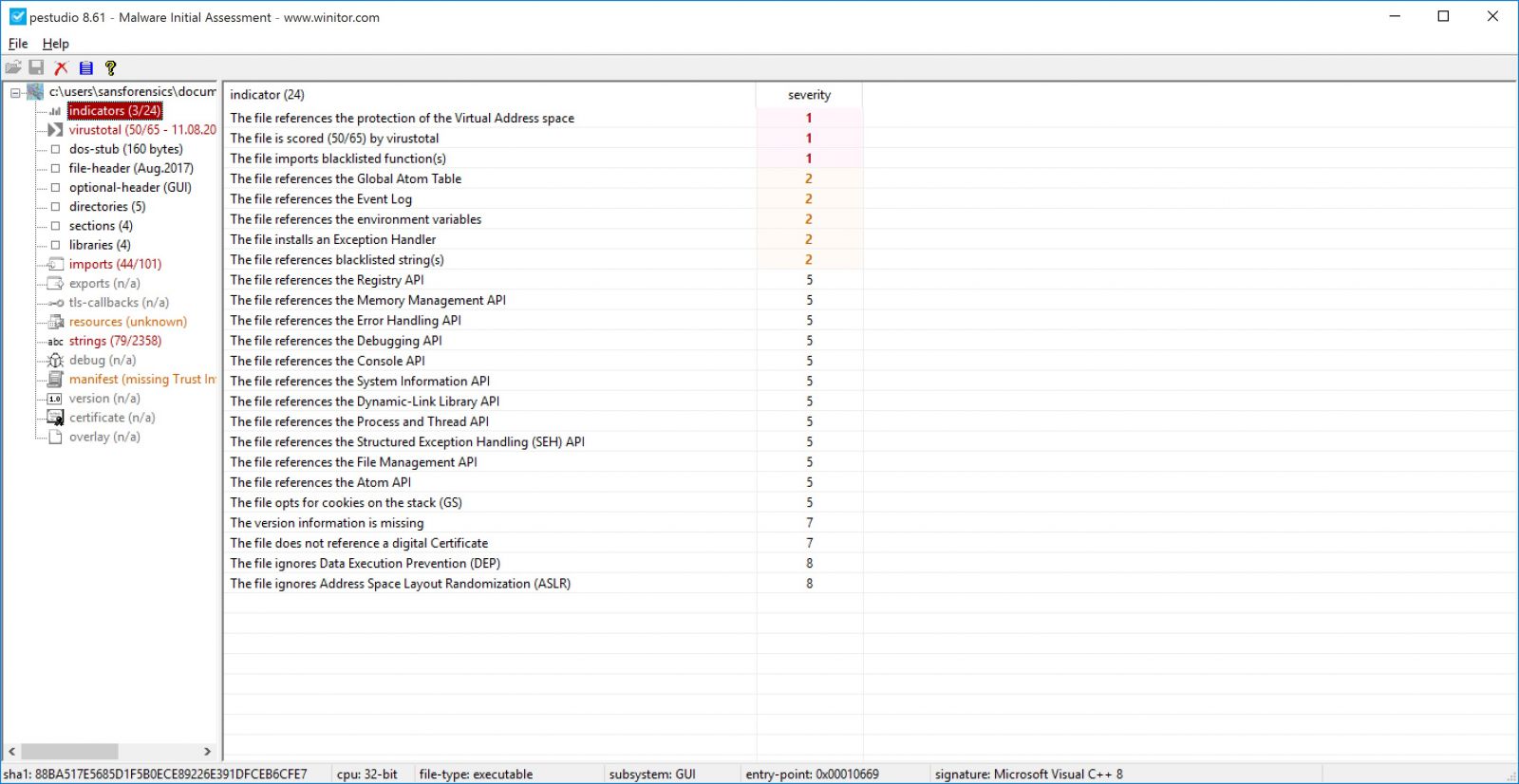
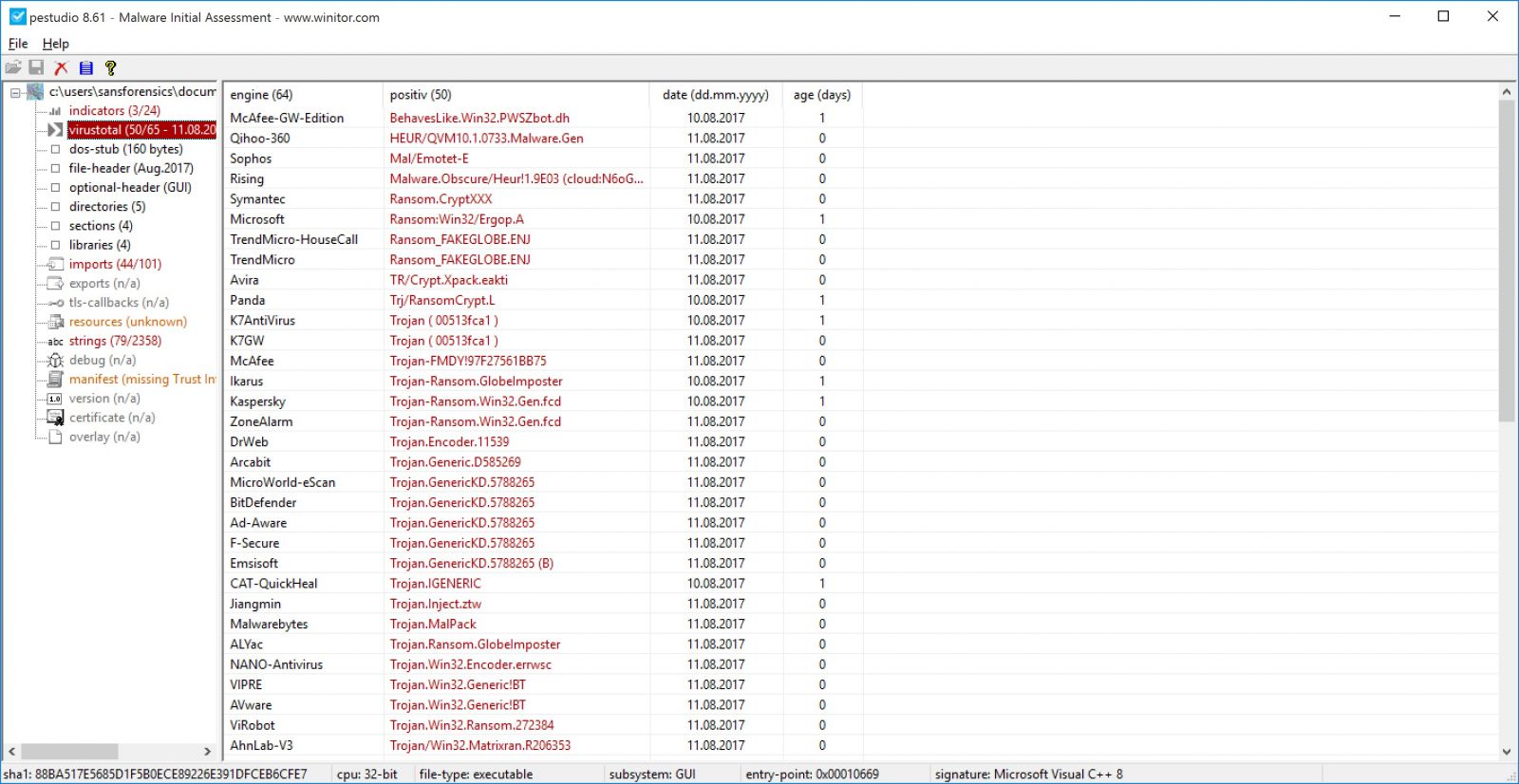
By default Pestudio will send a MD5 hash of the file to Virustotal and it will retrieve the results, if you don’t feel comfortable of sending such info to a third-party website. You can disable it by changing <score-file enable="1"/> to <score-file enable="0"/> in settings.xml file which is located in xml directory.
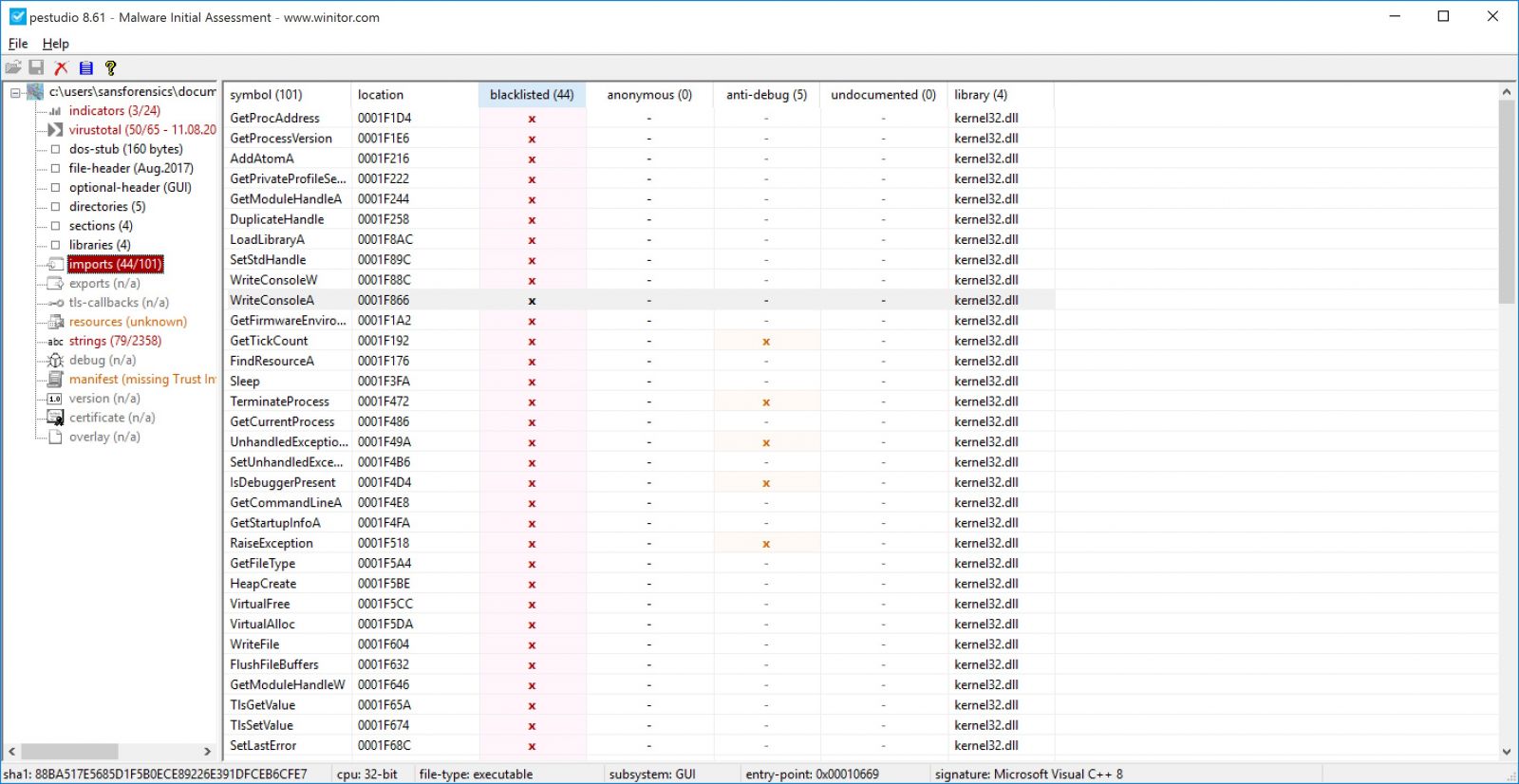
Pestudio retrieves the libraries and the functions referenced in the suspicious file. Pestudio comes with a predefined list of libraries and functions which is often used by malware.
The resources section will show if the suspicious file host a payload , in this example I have used different malware sample.
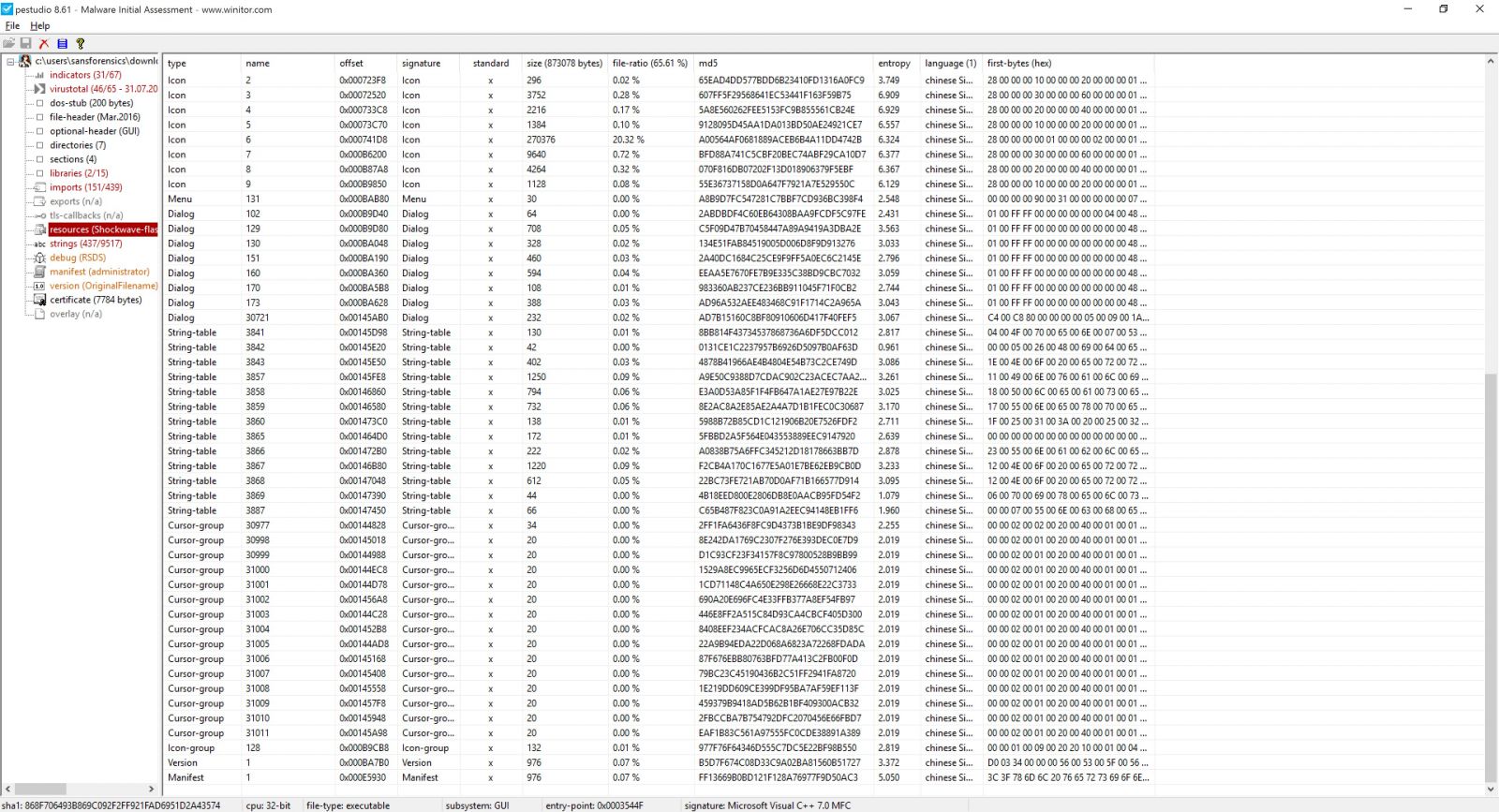
Unlike linux/unix strings command, pestudio will mark any suspicious string . pestudio comes with a predefined list of a suspicious strings (strings.xml).
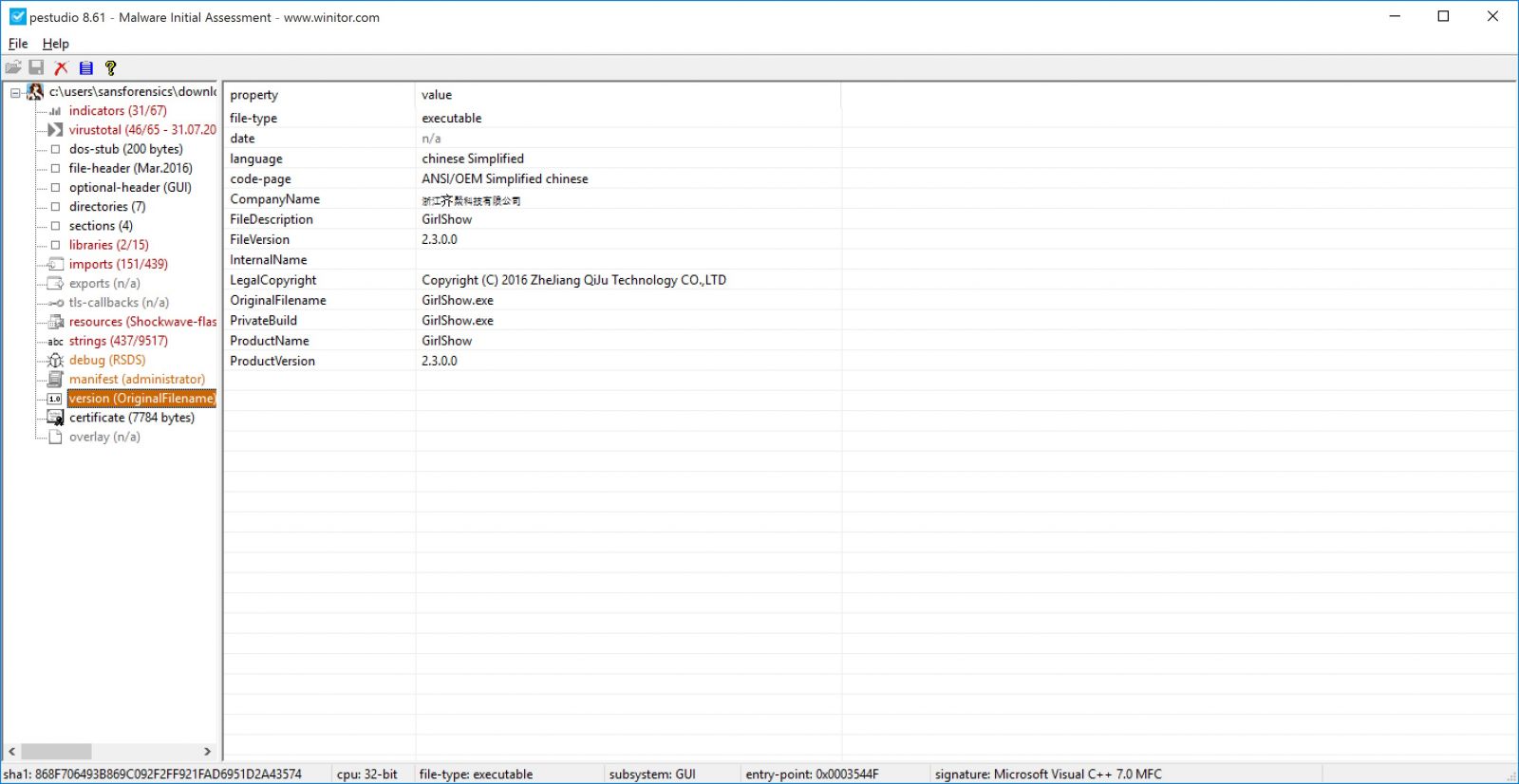
In the version (OriginalFilename) it will show you the orginal file name and other information such as language and Product version.
Finally you can save the triage report as xml file and with your favorite xml parser.
VMware Security Advisories -VMSA-2017-0014
VMware has released the following new security advisory:
1. Summary
VMware NSX-V Edge updates address OSPF Protocol LSA DoS.
2. Relevant Products
- VMware NSX-V Edge
- 3. Problem Description
a. VMware NSX-V Edge OSPF Protocol LSA Denial of Service
VMware NSX-V implementation of the OSPF protocol doesn’t correctly handle the link-state advertisement (LSA). A rogue LSA may exploit this issue resulting in continuous sending of LSAs between two routers eventually going in loop or loss of connectivity.
Note: The issue cannot be exploited in case the OSPF protocol is not configured. At setup time, no particular protocol is configured. For more information on static and dynamic routing for NSX Edge refer to the NSX Administration Guide, section Logical Router.
VMware would like to thank Adi Sosnovich, Orna Grumberg and Gabi Nakibly for reporting this issue to us.
The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the identifier CVE-2017-4920 to this issue.
for further information:
https://www.vmware.com/security/advisories/VMSA-2017-0014.html


Comments