Scanning tricks with scapy
by Manuel Humberto Santander Pelaez (Version: 1)
Sometimes, nmap can be quite noisy an trigger host IPS or network IPS alarms. When doing recon, one of the available options is ARP Ping. Let's see the packet distribution for a ARP Ping scan performed to a /24 network using the command nmap -PR 192.168.0.0/24:
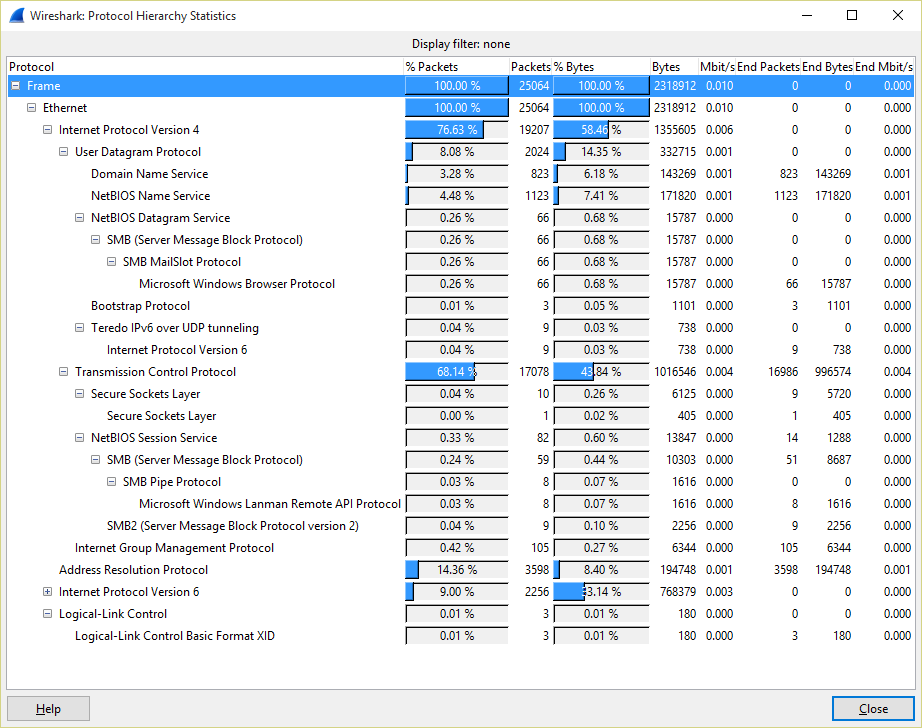
Not that much ARP packets, isn't it? nmap performs portscan to targets as well. If we want to be quiet, we could use the pattern performed by default gateways, which send ARP request to all the active nodes in its table from time to time. Let's see an example:
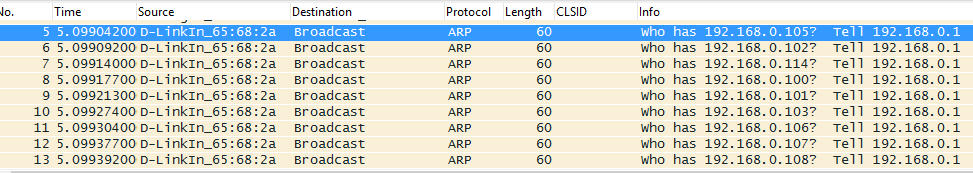
We can send the same packet sequence using scapy. Let's see the script:
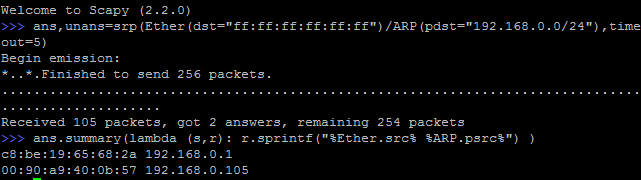
There are 6 hosts on the network only two answered. What happened? We just sent ARP packets without any options set. To reproduce the gateway packet pattern, we need to review the ARP header:
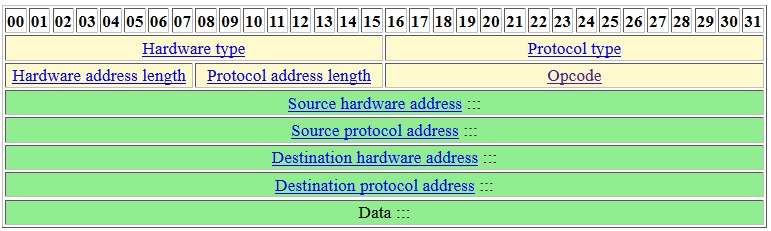
We just set the destination protocol address and all the other options are missing. What do we need to set?
- opcode: Need to be set to 1 (request)
- hardware type: Need to be set to 1 (Ethernet)
- protocol type: Need to be set to 0x0800 (IP)
Let's try again the scapy script with the new options:
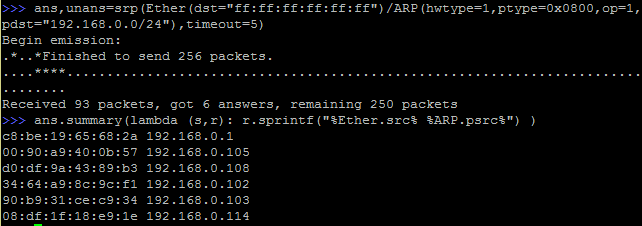
This scan is definitely not noisy. Let's see the packet distribution:
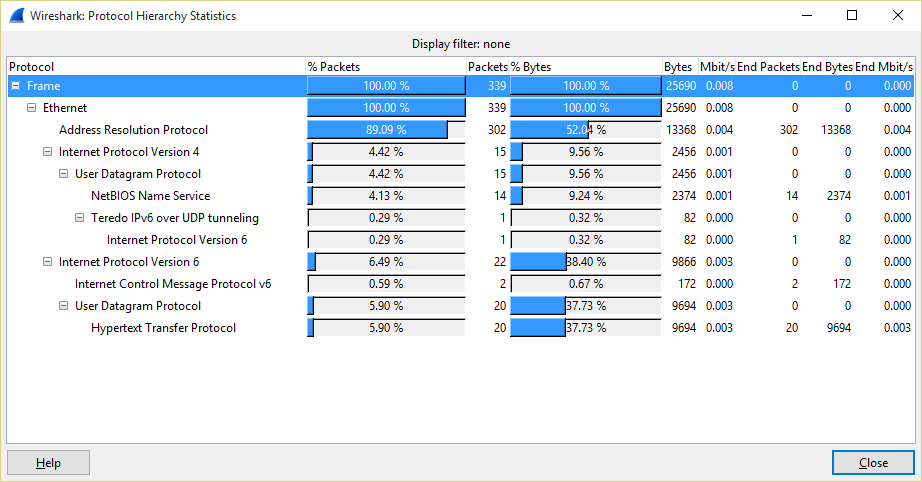
Scapy is so powerful. If you need specific features in pentesting, you should definitely consider building your own tools invoking libraries like this one.
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter: @manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org


Comments