A recent decline in traffic associated with Operation Windigo
Introduction
According to a 2014 report by ESET, Windigo is the code name for an ongoing operation that started as early as 2011 [1]. As noted in the report, legitimate traffic to servers compromised by the Windigo group redirect visitors to an exploit kit (EK). If the Windows client is vulnerable, it would be infected by the EK.
In December 2014, the Windigo group started using Nuclear EK to deliver its payload. Kafeine first tweeted about this in December [2], and I posted a few blog entries covering Operation Windigo in the following months [3, 4, 5, 6, 7].
As summer draws to a close, I've seen less traffic from the Windigo group. It's still active, but I haven't found it at all in recent weeks. Fortunately, today (Friday, 2015-08-21) I was lucky enough to encounter a website compromised by the Windigo group. It kicked off a chain of events leading to Nuclear EK.
This diary examines the infection traffic.
Background
Last month, a reader informed me that forum.tramedibeautiful.com may be compromised. When I first checked, the website redirected to myfilestore.com, and I didn't see any EK traffic.
Today I tried forum.tramedibeautiful.com and saw the same redirect, but this time myfilestore.com led to Nuclear EK. Based on the traffic, you'll find myfilestore.com was compromised by the Windigo group and is redirecting to Nuclear EK.
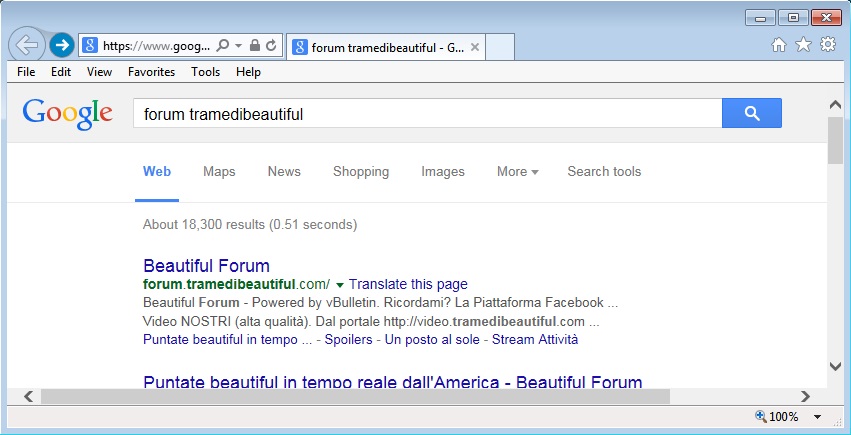
Shown above: Google search results to forum.tramedibeautiful.com.
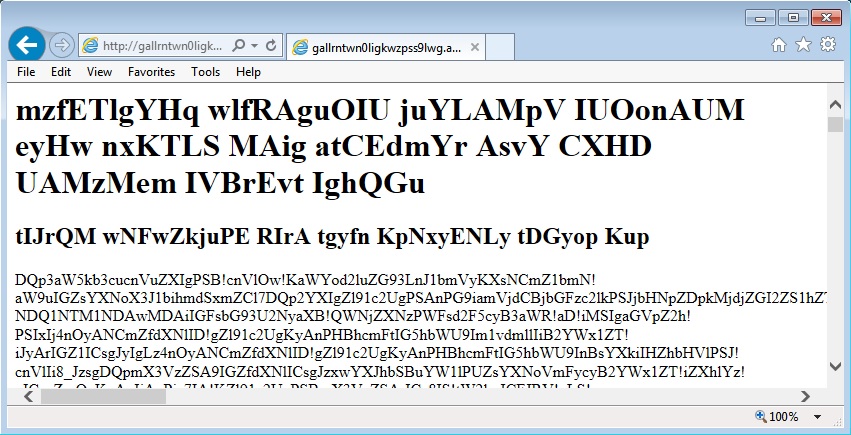
Shown above: a few seconds after I clicked on the Google search result.
Traffic
See the image below for the HTTP traffic generated by this infection chain of events. Traffic to 111.118.177.20 is a Cushion-style redirect and Nuclear EK used by the Windigo group. Post-infection traffic to 209.96.38.62 over TCP port 17326 and 108.163.245.234 over TCP port 49053 was caused by Glupteba malware sent from the EK.
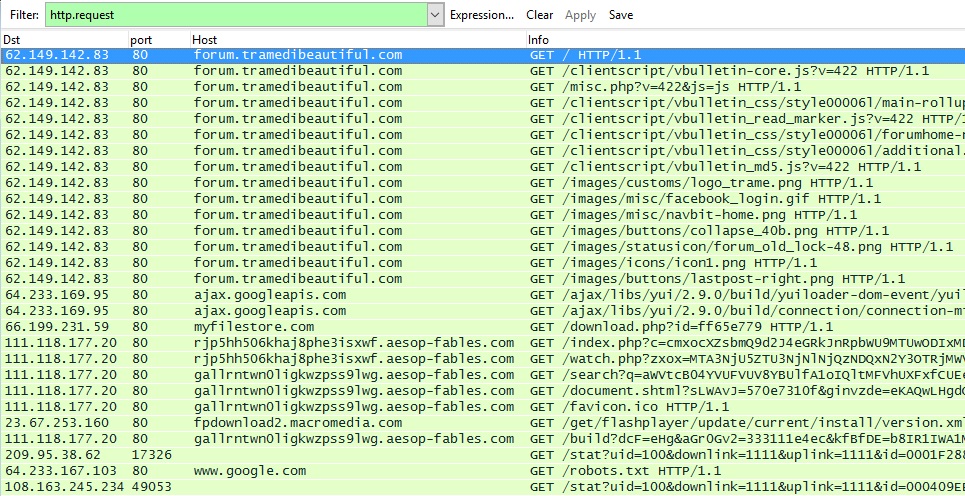
Shown above: Wireshark view of the traffic filtered for HTTP requests.
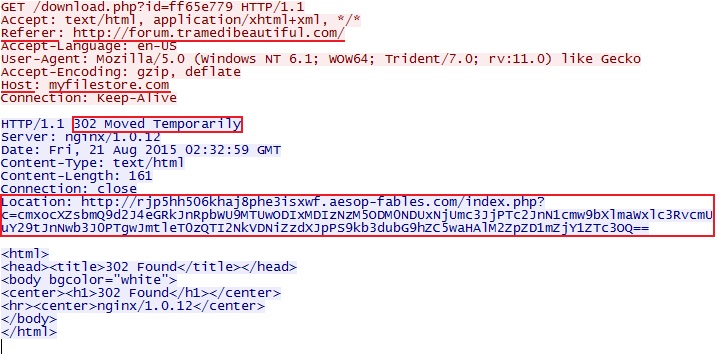
Shown above: myfilestore.com redirecting to a Cushion-style URL used by the Windigo group.
Snort events
A key indicator for Operation Windigo is the EmergingThreats (ET) alert ET CURRENT_EVENTS Cushion Redirection (sid:2017552) [8]. I replayed a pcap of the infection traffic in Security Onion using Suricata with the ET open rule set. In the image below, we find alerts associated with Nuclear EK traffic caused by the Windigo group.
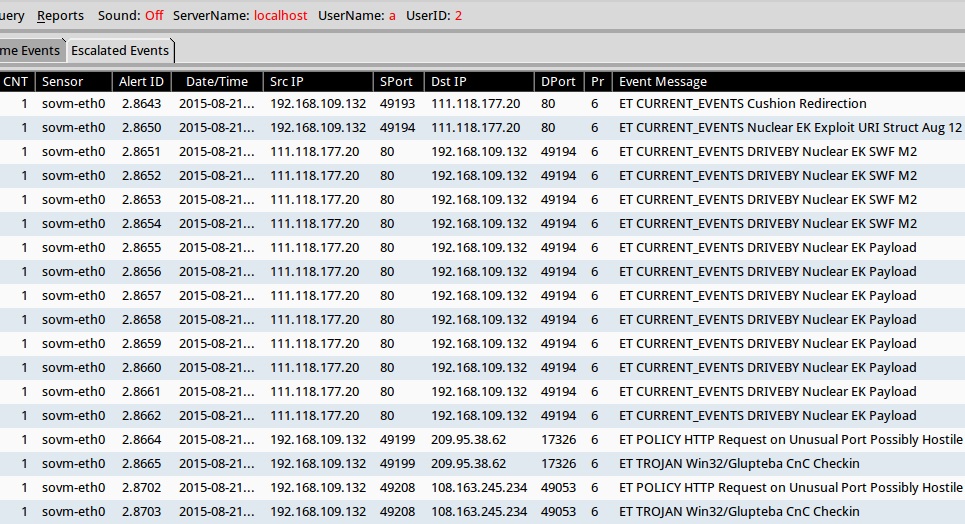
Shown above: Squil in Security Onion with events from the traffic.
I also used the latest version of Snort (2.9.7.5) with the snort registered rule set to read the pcap. The results show several alerts for post-infection traffic we typically see with malware used by the Windigo group.
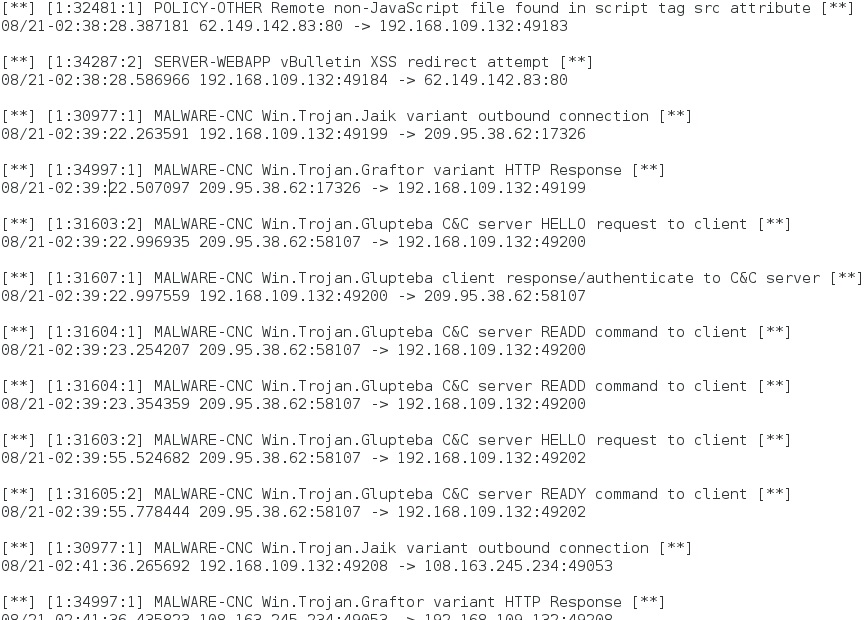
Shown above: Alerts from the traffic using Snort 2.9.7.5.
Final words
Don't know why I haven't been seeing as much Windigo group Nuclear EK lately. Maybe this actor is on the decline. Others may have more visibilty on this.
Traffic and malware from the analysis are listed below:
- A pcap of the Friday 2015-08-20 Windigo group Nuclear EK traffic is here.
- A zip archive containing associated malware and artifacts is available here.
The zip archive is password-protected with the standard password. If you don't know it, email admin@malware-traffic-analysis.net and ask.
---
Brad Duncan
Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] http://www.welivesecurity.com/wp-content/uploads/2014/03/operation_windigo.pdf
[2] https://twitter.com/kafeine/status/542231866687098880
[3] http://malware-traffic-analysis.net/2014/12/10/index.html
[4] http://malware-traffic-analysis.net/2014/12/25/index.html
[5] http://malware-traffic-analysis.net/2015/01/01/index.html
[6] http://malware-traffic-analysis.net/2015/02/11/index.html
[7] http://www.rackspace.com/blog/in-2015-operation-windigo-is-still-going-strong/
[8] http://docs.emergingthreats.net/bin/view/Main/2017552


Comments