Exploit Kit Evolution During 2014 - Nuclear Pack
This is a guest diary submitted by Brad Duncan.
Nuclear exploit kit (also known as Nuclear Pack) has been around for years. Version 2.0 of Nuclear Pack was reported in 2012 [1] [2]. Blogs like malware.dontneedcoffee.com have mentioned version 3.0 of Nuclear Pack in posts during 2013 [3] [4].
This month, Nuclear Pack changed its traffic patterns. The changes are significant enough that I wonder if Nuclear Pack is at version 4. Or is this merely an evolution of version 3, as we've seen throughout 2014? Let's look at the traffic.
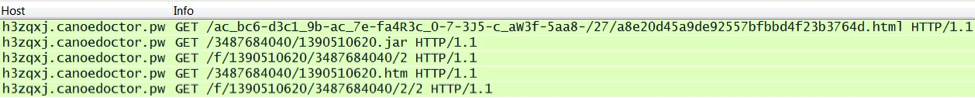
In January 2014, traffic from Nuclear Pack was similar to what I'd seen in 2013. Here's an example from January 24th using Java to infect a VM [5]:
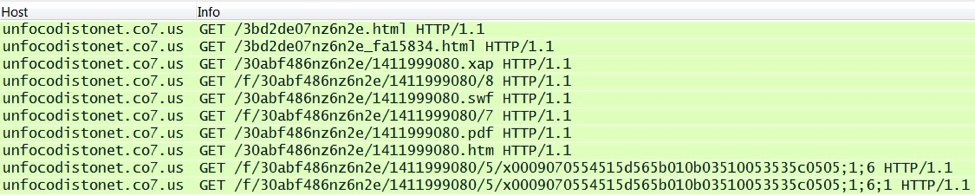
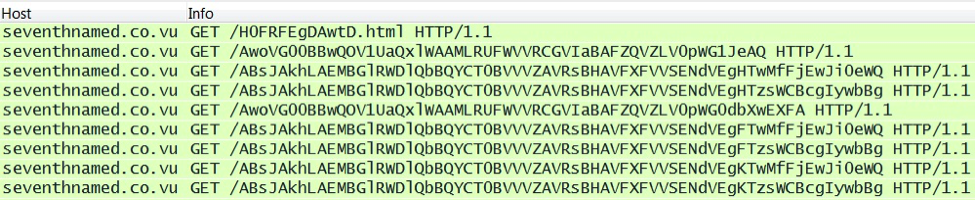
2014 saw Fiesta exploit kit-style URLs from Nuclear Pack. Also, like other exploit kits, Nuclear sent Flash and Silverlight exploits. Here's an example from September 29th [6]:
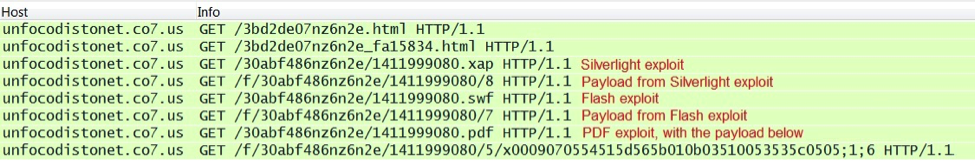
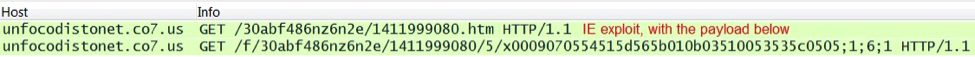
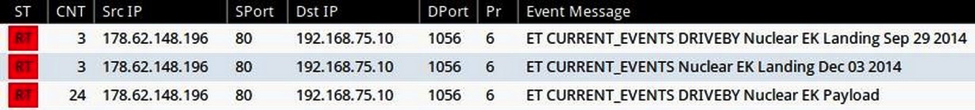
The above example has Silverlight, Flash, PDF and IE exploits. In each case, a payload was sent to the vulnerable VM. The traffic consists of two TCP streams. The images below show the separate streams and their HTTP GET requests:
These patterns are not far off from the beginning of the year. I only saw additional exploits from Nuclear Pack that I hadn't noticed before.
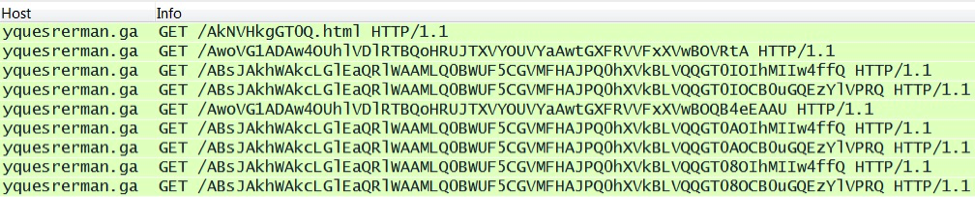
In December 2014, Nuclear Pack moved to a different URL structure. I first noticed this on a pcap from Threatglass.com [7]. Initially, I'd mistaken the traffic for Angler exploit kit. After reviewing the pcap in Security Onion, I realized this was Nuclear Pack.
Here's another Nuclear Pack example from 2014-12-12 [8]:
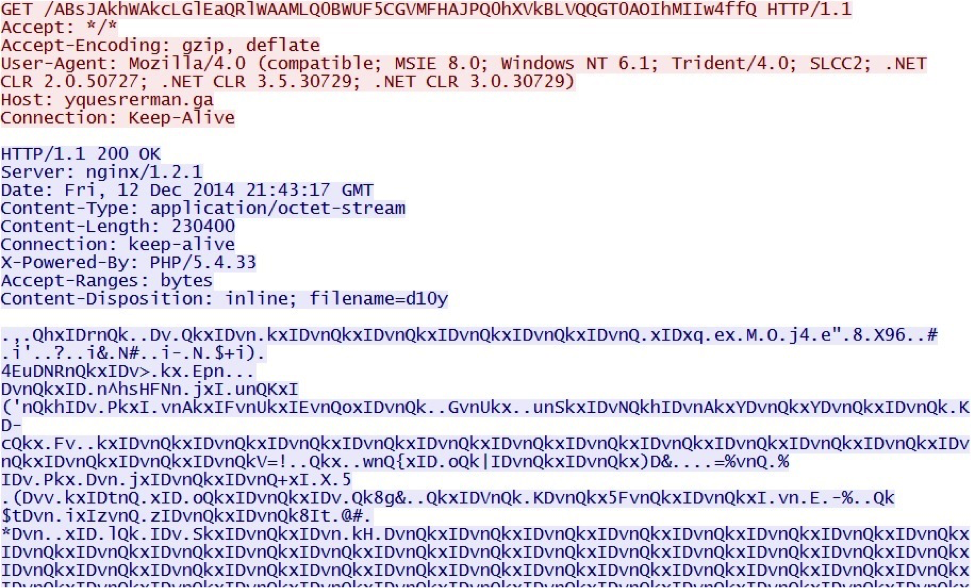
Since the change in URL patterns, Nuclear Pack is XOR-ing the malware payload. The image below shows an example where one of payloads is XOR-ed with the ASCII string: DvnQkxI
The change in traffic patterns is fairly significant for Nuclear Pack. I haven't found any reason on why the change occurred. Is this merely an evolution, or do these changes indicate a new version of Nuclear Pack?
----------
Brad Duncan is a Security Analyst at Rackspace, and he runs a blog on malware traffic analysis at http://www.malware-traffic-analysis.net
References:
[1] http://blog.spiderlabs.com/2012/04/a-new-neighbor-in-town-the-nuclear-pack-v20-exploit-kit.html
[2] http://www.webroot.com/blog/2012/10/31/nuclear-exploit-pack-goes-2-0/
[3] http://malware.dontneedcoffee.com/2013/08/cve-2013-2465-integrating-exploit-kits.html
[4] http://3.bp.blogspot.com/-iqXmOKC5Zgk/UieYOEA8jPI/AAAAAAAAA_c/nlX2cgxhyZo/s1600/screenshot_2013-09-04_020.png
[5] http://malware-traffic-analysis.net/2014/01/24/index.html
[6] http://malware-traffic-analysis.net/2014/09/29/index.html
[7] http://threatglass.com/malicious_urls/firstliving-org
[8] http://malware-traffic-analysis.net/2014/12/12/index.html


Comments