Scam Report - Fake Voice Mail Email Notification Redirects to Malicious Site
We received a report of a recent scam that persuaded the victim to click on a link that claimed to be a recorded voice mail message. (Thanks for the pointer, Sean Thomas.)
According to VCU, the scammer's message had the following contents:
Subject: Voice Mail from 703-892-1228 (55 seconds)
You received a voice mail : N_V50-062-NIDS.WAV (182 KB)
Caller-Id: 703-892-1228
Message-Id: 458AH-PEL-02UEU
Email-Id: voice.mail@vcu.edu
This e-mail contains a voice message.
Double click on the link to listen the message.
Sent by Microsoft Exchange Server
Better Business Bureau published a screenshot of a similar message. According to BBB, although the "attachment appears to be a .wav audio file, but it’s really an HTML link that redirects recipients to a malicious website."
As far as we can tell, there is no email attachment in this attack; the message claims to contain a WAV file, but merely includes a link that claims to allow the victim to play that "voice mail."
XtremeComputer.com examined one instance of this attack, stating that the link directed the recipient to "hxxp: //tweetsbazaar.com /5ACeRRyc /index.html" or "hxxp: //www.luckylu.de / EuaWg3cd / index.html". The victim's browser was then presented with a malicious Java applet "Gam.jar" and was further redirect to a URL at 173. 255. 221.74.
The Jsunpack website captured contents of one instance of the exploit being delivered via Gam.jar from 173.255.221.74, which (not surprisingly) contained the malicious Java applet and obfuscated JavaScript. This looks like an instance of the Blackhole Exploit Kit.
If you have additional details regarding this scam and the associated client-side attack, please let us know or leave a comment.
-- Lenny Zeltser
Lenny Zeltser focuses on safeguarding customers' IT operations at NCR Corp. He also teaches how to analyze malware at SANS Institute. Lenny is active on Twitter and Google+. He also writes a security blog.
Analyzing Malicious RTF Files Using OfficeMalScanner's RTFScan
Attackers have been using Rich Text Format (RTF) files to carry exploits targeting vulnerabilities in Microsoft Office and other products. We documented one such incident in June 2009 ("details.rtf"). In a more recent example, the CVE-2012-0158 vulnerability was present in Active X controls within MSCOMCTL.OCX, which could be activated using Microsoft Office and other applications. McAfee described one such exploit, which appeared in the wild in April 2012:
"In the malicious RTF, a vulnerable OLE file is embedded with \object and \objocx tags. ... Upon opening a crafted file with the vulnerable application, as in other document exploit files, we see an innocent file posing as bait, while in the background, the Trojan files are installed."
How might you analyze a suspicious RTF file, perhaps delivered to you or your users as an email attachment? RTFScan, now available as part of Frank Boldewin's OfficeMalScanner toolkit, can examine RTF files and assist in extracting embedded artifacts.
Consider the "details.rtf" file, which contained an embedded PE executable without any obfuscation. In an earlier diary we demonstrated a technique for extracting the PE executable from this file with the help of sed, Perl, hexdump and dd. RTFScan makes the task easier:
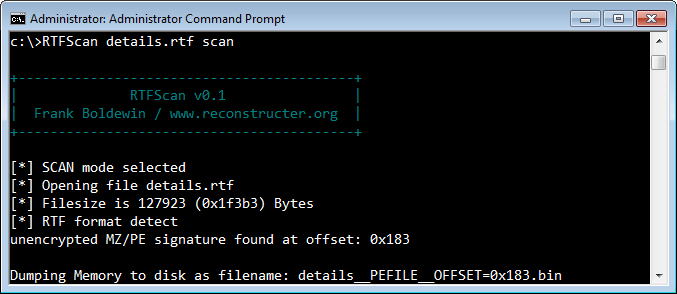
RTFScan automatically located the embedded PE file and extracted it.
Consider the more sophisticated example that took advantage of the CVE-2012-0158 vulnerability mentioned above. In one such incident, a file named "6TH WPCT Action Plan from Environment Group.doc" was delivered to victims by email as part of a targeted attack. Though the file ends with the .doc extension, it is actually an RTF file. RTFScan can scan it and identify malicious artifacts:
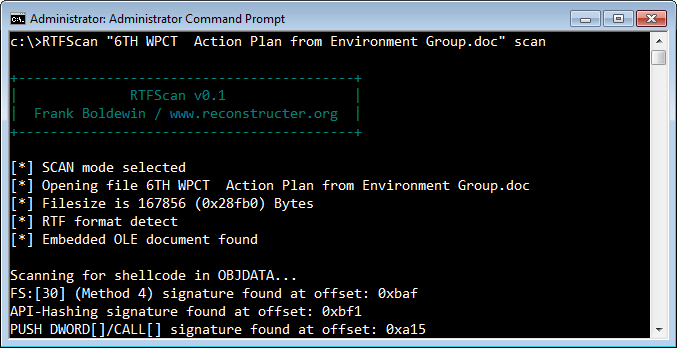
In this case, the malicious executable wasn't directly stored within the RTF file. Instead, the RTF file embedded an OLE object that included the attacker's shellcode. A vulnerable version of Microsoft Word could be tricked into executing the shellcode, which deobfuscated and extracted the malicious PE executable hidden within it.
RTFScan located the embedded OLE object and extracted it. Moreover, it scanned the OLE object for the patterns commonly included in shellcode, such as "FS:[30]" (looking for PEB), API hashing and others. At this point, you could use another tool in the OfficeMalScanner toolkit, called MalHost-Setup, to extract the shellcode and debug it to better understand its functionality. (If you're wondering what the executable embedded into this sample does, see an overview by Byt0r.)
If this is interesting to you, take a look at the article How Malicious Code Can Run in Microsoft Office Documents.
-- Lenny Zeltser
Lenny Zeltser focuses on safeguarding customers' IT operations at NCR Corp. He also teaches how to analyze malware at SANS Institute. Lenny is active on Twitter and Google+. He also writes a security blog.
ISC Feature of the Week: Privacy Policy
Overview
There have been a lot of data leaks of email, password, credit card information and more lately. I wanted to take a moment and remind everyone about the Internet Storm Center's and the SANS Institute's commitment to protecting private information as outlined in our ISC/DShield Privacy Policy at https://isc.sans.edu/privacy.html.
Additionally, any source information in DShield submissions as well as any other project such as the 404project are anonymised in public reports.
Features
I'll give a brief summary here and you can follow the links for complete details.
First line is Last Updated date so you'll know immediately if there are any current changes.
1. How We Gather Information - https://isc.sans.edu/privacy.html#1
The ISC Portal system saves your information and references it to your email address and password.
2. Log Files - https://isc.sans.edu/privacy.html#2
Web logs are stored and used to analyze trends, to administer the site, to track how visitors interact with the site.
3. Cookies - https://isc.sans.edu/privacy.html#3
ISC may use both session ID cookies and persistent cookies. We use session cookies to make it easier for you to navigate our site. You can remove your ISC Portal login cookie by clicking the "Logout" link.
4. How We Protect Your Personal Information - https://isc.sans.edu/privacy.html#4
ISC safeguards the security of the data you send us with physical, electronic, and managerial procedures. The ISC website uses SSL v3 and TLS v1 encryption on all web pages where personal information is submitted.
5. Access To Your Personal Information - https://isc.sans.edu/privacy.html#5
To review and update your personal contact information, simply click https://isc.sans.edu/login.html and log in with your email address and password, then click My Information.
6. Notifications and Promotional Email - https://isc.sans.edu/privacy.html#6
You are free to opt-in and/or opt-out of any notification or email.
7. Links To Other Sites - https://isc.sans.edu/privacy.html#7
The ISC web site contains links to other sites that are not owned or controlled by ISC. Please be aware that the ISC is not responsible for the privacy practices of such other sites.
8. Affiliates And Subsidiaries - https://isc.sans.edu/privacy.html#8
DShield.org provides Google Ads and uses Google Analytics in certain areas of the site.
9. Information Obtained From Third Parties - https://isc.sans.edu/privacy.html#9
ISC does not sell or trade your personal information. We may at times receive contact lists from other organizations. We may send mailings such as brochures to these addresses.
10. Changes To This Privacy Statement - https://isc.sans.edu/privacy.html#10
If we decide to change our privacy policy, we will post those changes to this privacy statement, the homepage, and other places we deem appropriate so that you are aware of what information we collect, how we use it, and under what circumstances, if any, we disclose it.
11. Contact Us - https://isc.sans.edu/privacy.html#11
If you have any questions or suggestions regarding our privacy policy, please contact us at handlers@sans.edu.
Post suggestions or comments in the section below or send us any questions or comments in the contact form on https://isc.sans.edu/contact.html#contact-form
--
Adam Swanger, Web Developer (GWEB, GWAPT)
Internet Storm Center https://isc.sans.edu


Comments